I'm failing to pass tags collection for new azure resource when using Azure CLI.
I have several tags validation policies, yet I have verified them via Azure Portal and the tags values are valid.
I'm using PowerShell 7.3
Command
$TAGS = "foo=X/12345/01/01 [email protected] app=myapp1"
az group create `
--name $RESOURCE_GROUP `
--location $LOCATION `
--query "properties.provisioningState" `
--tags $TAGS
Validation errors
Type: PolicyViolation
Info: {
"evaluationDetails": {
"evaluatedExpressions": [
{
"result": "True",
"expressionKind": "Field",
"expression": "type",
"path": "type",
"expressionValue": "Microsoft.Resources/subscriptions/resourcegroups",
"targetValue": "Microsoft.Resources/subscriptions/resourceGroups",
"operator": "Equals"
},
{
"result": "True",
"expressionKind": "Field",
"expression": "tags[foo]",
"path": "tags[foo]",
"expressionValue": "X/12345/01/01 [email protected] app=myapp1",
"targetValue": [
"X/12345/01/01",
...
],
"operator": "NotIn"
}
]
},
"policyDefinitionId": "/providers/Microsoft.Management/managementgroups/Non-Production/providers/Microsoft.Authorization/policyDefinitions/Enforce_tag_foo_rg",
"policyDefinitionName": "Enforce_tag_foo_rg",
"policyDefinitionDisplayName": "Require foo tag name and correct values on resource group",
"policyDefinitionEffect": "deny",
"policyAssignmentId": "/providers/Microsoft.Management/managementGroups/Non-Production/providers/Microsoft.Authorization/policyAssignments/Enforce_tag_foo_rg",
"policyAssignmentName": "Enforce_tag_foo_rg",
"policyAssignmentDisplayName": "Enforce Tag - foo on resource groups",
"policyAssignmentScope": "/providers/Microsoft.Management/managementGroups/Non-Production",
"policyAssignmentParameters": {
"tagName": "foo",
"tagValue": [
"X/12345/01/01",
...
]
}
}
Note this line
"expressionValue": "X/12345/01/01 [email protected] app=myapp1"
This looks like invalid argument format, but az group create -h is clear about it.
Command
az group create : Create a new resource group.
Arguments
--tags : Space-separated tags: key[=value] [key[=value] ...].
Use "" to clear existing tags.
CodePudding user response:
Per comments, PowerShell is invoking this command for you:
az group create --name name --location location --query properties.provisioningState --tags "foo=X/12345/01/01 [email protected] app=myapp1"
with --tags "foo=X/12345/01/01 [email protected] app=myapp1" at the end.
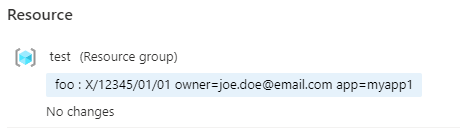
The az command is interpretting this as a tag called foo with a value X/12345/01/01 [email protected] app=myapp1, but that violates your policy so you get an error.
Note - if your policy wasn't there, az would quite happily create the resource group like this:
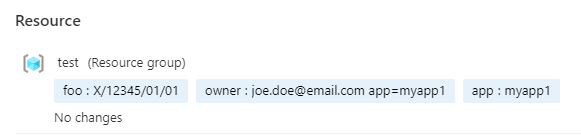
What you actually want is this:
so working backwards your az command needs to be
az group create --name name --location location --query properties.provisioningState --tags "foo=X/12345/01/01" "[email protected]" "app=myapp1"
with --tags "foo=X/12345/01/01" "[email protected]" "app=myapp1" at the end,
and to do that you need to use this:
$tags = @("foo=X/12345/01/01", "[email protected]", "app=myapp1")