I am working on hosting an web app on Azure, that uses APIM, functions app(serverless), storage account. Now I am looking at making communication between all those secure. For that I found Vnet and private endpoint on Azure.
So the scenario is, I have lockdown the storage account in a VNET and created an private endpoint for that. But to make it accessible from function app, the function app also lies in same VNET, which is not possible in case of serverless function app .(Apps with minimum premium plan can be lockdown in VNET)
So my question here is how can I make those communication between function app and storage account more secure??
For function app I can define a IP rule with APIm IP so that it is not accessible from outside, but what to do for storage account.
Thanks
CodePudding user response:
Do you really need to block at all?
Storage account encrypts data at rest and if you Function App and your storage account stays in the same Datacenter, Microsoft will automatic route the communications between your devices thru the backbone.
So, the communication will be “secure” and the access to your storage account will also be secure by SAS Token or key…
If you really need to secure more, you must change your function app.
CodePudding user response:
how can I make those communications between function app and storage account more secure??
Azure storage account has additional settings to enforce secure communication with client applications. You can get these settings by navigating to Settings > Configuration:
1. Restrict the blob access from public
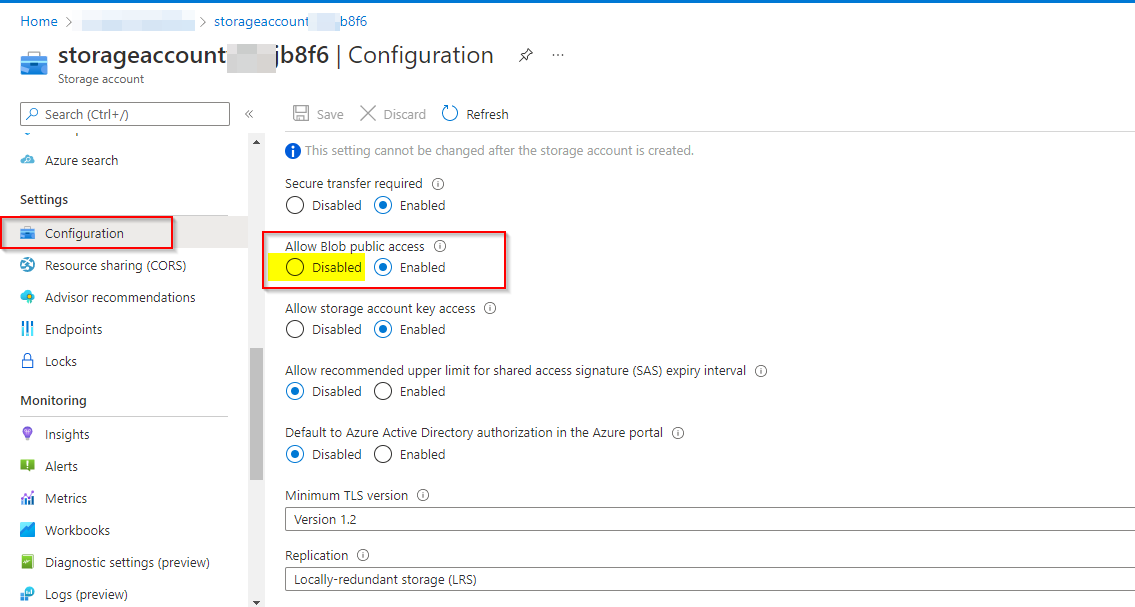
- Configure the storage account firewall to selectedNetworks radio button.
- There are 5 major areas in which the security is set-up to storage account like:
- Management Plane Security
- Data Plane security
- Encryption in transit
- Encryption at rest
- CROSS (Cross-Origin ResourceSharing)
Data Plane Security:
It refers to the ways for securing data objects within the storage account (blobs, queues, tables, and files).
Container and queue access is controlled by Azure Active Directory. Azure Active Directory has several advantages over traditional authorization methods, including the elimination of the need to store secrets in your code.
Storage account keys provide you full access to all of the data in your storage account.
We use shared access signatures to grant access to services such as blobs, queues, or a combination of them. If we want to restrict access to specific levels, such as read-only, update, or delete, we use time-limited access for that purpose.
You can encrypt the data before being moving to azure storage using HTTPS encryption and cross-origin policy by referring few settings using SAS where the client-side is encrypted and decrypted by Azure.
For more details, you can refer how to configure for encrypting/securing the data between your function app to storage account
