When deploying from template,
This service is stack as CREATE_IN_PROGRESS
ServiceD69D759B arn:aws:ecs:ap-northeast-1:6781002281XX:service/AdminCluster/CdkFargateStack-ServiceD69D759B-sm274jjTfbP7 AWS::ECS::Service CREATE_IN_PROGRESS Resource creation Initiated -
However I have no idea where to start.
This docker image receive the access from 8011, so in local
it works in local like this
docker run -p 8011:8011 -it st_admin_site:latest
I check CloudWatch but can't find the log.
This is my cdk command
constructor(scope: Construct, id: string, props?: StackProps) {
super(scope, id, props);
const cluster = new ecs.Cluster(this, "SampleCluster", {
clusterName: "AdminCluster"
});
const adminImage = ecs.ContainerImage.fromRegistry('st_admin_site:latest');
const taskDefinition = new ecs.FargateTaskDefinition(this, "TaskDef");
const container = taskDefinition.addContainer("DefaultContainer", {
image: adminImage,
memoryLimitMiB: 512,
cpu: 256
});
container.addPortMappings({
containerPort: 8011
});
const ecsService = new ecs.FargateService(this, "Service", {
cluster,
taskDefinition,
desiredCount: 2
});
const lb = new elb.ApplicationLoadBalancer(this, "LB", {
vpc: cluster.vpc,
internetFacing: true
});
const listener = lb.addListener("Listener", { port: 80 });
const targetGroup = listener.addTargets("ECS", {
protocol: elb.ApplicationProtocol.HTTP,
port: 8011,
targets: [ecsService]
});
And it makes the template.
{
"Resources": {
"SampleClusterB4B72990": {
"Type": "AWS::ECS::Cluster",
"Properties": {
"ClusterName": "AdminCluster"
},
"Metadata": {
"aws:cdk:path": "CdkFargateStack/SampleCluster/Resource"
}
},
"SampleClusterVpcD1C6ABD9": {
"Type": "AWS::EC2::VPC",
"Properties": {
"CidrBlock": "10.0.0.0/16",
"EnableDnsHostnames": true,
"EnableDnsSupport": true,
"InstanceTenancy": "default",
"Tags": [
{
"Key": "Name",
"Value": "CdkFargateStack/SampleCluster/Vpc"
}
]
},
"Metadata": {
"aws:cdk:path": "CdkFargateStack/SampleCluster/Vpc/Resource"
}
},
"SampleClusterVpcPublicSubnet1SubnetE377A512": {
"Type": "AWS::EC2::Subnet",
"Properties": {
"CidrBlock": "10.0.0.0/18",
"VpcId": {
"Ref": "SampleClusterVpcD1C6ABD9"
},
"AvailabilityZone": {
"Fn::Select": [
0,
{
"Fn::GetAZs": ""
}
]
},
"MapPublicIpOnLaunch": true,
"Tags": [
{
"Key": "aws-cdk:subnet-name",
"Value": "Public"
},
{
"Key": "aws-cdk:subnet-type",
"Value": "Public"
},
{
"Key": "Name",
"Value": "CdkFargateStack/SampleCluster/Vpc/PublicSubnet1"
}
]
},
"Metadata": {
"aws:cdk:path": "CdkFargateStack/SampleCluster/Vpc/PublicSubnet1/Subnet"
}
},
"SampleClusterVpcPublicSubnet1RouteTable7114D244": {
"Type": "AWS::EC2::RouteTable",
"Properties": {
"VpcId": {
"Ref": "SampleClusterVpcD1C6ABD9"
},
"Tags": [
{
"Key": "Name",
"Value": "CdkFargateStack/SampleCluster/Vpc/PublicSubnet1"
}
]
},
"Metadata": {
"aws:cdk:path": "CdkFargateStack/SampleCluster/Vpc/PublicSubnet1/RouteTable"
}
},
"SampleClusterVpcPublicSubnet1RouteTableAssociation0B5402E3": {
"Type": "AWS::EC2::SubnetRouteTableAssociation",
"Properties": {
"RouteTableId": {
"Ref": "SampleClusterVpcPublicSubnet1RouteTable7114D244"
},
"SubnetId": {
"Ref": "SampleClusterVpcPublicSubnet1SubnetE377A512"
}
},
"Metadata": {
"aws:cdk:path": "CdkFargateStack/SampleCluster/Vpc/PublicSubnet1/RouteTableAssociation"
}
},
"SampleClusterVpcPublicSubnet1DefaultRoute28A82BC4": {
"Type": "AWS::EC2::Route",
"Properties": {
"RouteTableId": {
"Ref": "SampleClusterVpcPublicSubnet1RouteTable7114D244"
},
"DestinationCidrBlock": "0.0.0.0/0",
"GatewayId": {
"Ref": "SampleClusterVpcIGW21649D5C"
}
},
"DependsOn": [
"SampleClusterVpcVPCGW39AFB859"
],
"Metadata": {
"aws:cdk:path": "CdkFargateStack/SampleCluster/Vpc/PublicSubnet1/DefaultRoute"
}
},
"SampleClusterVpcPublicSubnet1EIPD2C3FC83": {
"Type": "AWS::EC2::EIP",
"Properties": {
"Domain": "vpc",
"Tags": [
{
"Key": "Name",
"Value": "CdkFargateStack/SampleCluster/Vpc/PublicSubnet1"
}
]
},
"Metadata": {
"aws:cdk:path": "CdkFargateStack/SampleCluster/Vpc/PublicSubnet1/EIP"
}
},
"SampleClusterVpcPublicSubnet1NATGateway715FE613": {
"Type": "AWS::EC2::NatGateway",
"Properties": {
"SubnetId": {
"Ref": "SampleClusterVpcPublicSubnet1SubnetE377A512"
},
"AllocationId": {
"Fn::GetAtt": [
"SampleClusterVpcPublicSubnet1EIPD2C3FC83",
"AllocationId"
]
},
"Tags": [
{
"Key": "Name",
"Value": "CdkFargateStack/SampleCluster/Vpc/PublicSubnet1"
}
]
},
"Metadata": {
"aws:cdk:path": "CdkFargateStack/SampleCluster/Vpc/PublicSubnet1/NATGateway"
}
},
"SampleClusterVpcPublicSubnet2SubnetB88D2B08": {
"Type": "AWS::EC2::Subnet",
"Properties": {
"CidrBlock": "10.0.64.0/18",
"VpcId": {
"Ref": "SampleClusterVpcD1C6ABD9"
},
"AvailabilityZone": {
"Fn::Select": [
1,
{
"Fn::GetAZs": ""
}
]
},
"MapPublicIpOnLaunch": true,
"Tags": [
{
"Key": "aws-cdk:subnet-name",
"Value": "Public"
},
{
"Key": "aws-cdk:subnet-type",
"Value": "Public"
},
{
"Key": "Name",
"Value": "CdkFargateStack/SampleCluster/Vpc/PublicSubnet2"
}
]
},
"Metadata": {
"aws:cdk:path": "CdkFargateStack/SampleCluster/Vpc/PublicSubnet2/Subnet"
}
},
"SampleClusterVpcPublicSubnet2RouteTable8A11EEAD": {
"Type": "AWS::EC2::RouteTable",
"Properties": {
"VpcId": {
"Ref": "SampleClusterVpcD1C6ABD9"
},
"Tags": [
{
"Key": "Name",
"Value": "CdkFargateStack/SampleCluster/Vpc/PublicSubnet2"
}
]
},
"Metadata": {
"aws:cdk:path": "CdkFargateStack/SampleCluster/Vpc/PublicSubnet2/RouteTable"
}
},
"SampleClusterVpcPublicSubnet2RouteTableAssociation857BF408": {
"Type": "AWS::EC2::SubnetRouteTableAssociation",
"Properties": {
"RouteTableId": {
"Ref": "SampleClusterVpcPublicSubnet2RouteTable8A11EEAD"
},
"SubnetId": {
"Ref": "SampleClusterVpcPublicSubnet2SubnetB88D2B08"
}
},
"Metadata": {
"aws:cdk:path": "CdkFargateStack/SampleCluster/Vpc/PublicSubnet2/RouteTableAssociation"
}
},
"SampleClusterVpcPublicSubnet2DefaultRouteFD4087CF": {
"Type": "AWS::EC2::Route",
"Properties": {
"RouteTableId": {
"Ref": "SampleClusterVpcPublicSubnet2RouteTable8A11EEAD"
},
"DestinationCidrBlock": "0.0.0.0/0",
"GatewayId": {
"Ref": "SampleClusterVpcIGW21649D5C"
}
},
"DependsOn": [
"SampleClusterVpcVPCGW39AFB859"
],
"Metadata": {
"aws:cdk:path": "CdkFargateStack/SampleCluster/Vpc/PublicSubnet2/DefaultRoute"
}
},
"SampleClusterVpcPublicSubnet2EIPCB2281EA": {
"Type": "AWS::EC2::EIP",
"Properties": {
"Domain": "vpc",
"Tags": [
{
"Key": "Name",
"Value": "CdkFargateStack/SampleCluster/Vpc/PublicSubnet2"
}
]
},
"Metadata": {
"aws:cdk:path": "CdkFargateStack/SampleCluster/Vpc/PublicSubnet2/EIP"
}
},
"SampleClusterVpcPublicSubnet2NATGatewayB385D543": {
"Type": "AWS::EC2::NatGateway",
"Properties": {
"SubnetId": {
"Ref": "SampleClusterVpcPublicSubnet2SubnetB88D2B08"
},
"AllocationId": {
"Fn::GetAtt": [
"SampleClusterVpcPublicSubnet2EIPCB2281EA",
"AllocationId"
]
},
"Tags": [
{
"Key": "Name",
"Value": "CdkFargateStack/SampleCluster/Vpc/PublicSubnet2"
}
]
},
"Metadata": {
"aws:cdk:path": "CdkFargateStack/SampleCluster/Vpc/PublicSubnet2/NATGateway"
}
},
"SampleClusterVpcPrivateSubnet1Subnet24256A44": {
"Type": "AWS::EC2::Subnet",
"Properties": {
"CidrBlock": "10.0.128.0/18",
"VpcId": {
"Ref": "SampleClusterVpcD1C6ABD9"
},
"AvailabilityZone": {
"Fn::Select": [
0,
{
"Fn::GetAZs": ""
}
]
},
"MapPublicIpOnLaunch": false,
"Tags": [
{
"Key": "aws-cdk:subnet-name",
"Value": "Private"
},
{
"Key": "aws-cdk:subnet-type",
"Value": "Private"
},
{
"Key": "Name",
"Value": "CdkFargateStack/SampleCluster/Vpc/PrivateSubnet1"
}
]
},
"Metadata": {
"aws:cdk:path": "CdkFargateStack/SampleCluster/Vpc/PrivateSubnet1/Subnet"
}
},
"SampleClusterVpcPrivateSubnet1RouteTable55080EB4": {
"Type": "AWS::EC2::RouteTable",
"Properties": {
"VpcId": {
"Ref": "SampleClusterVpcD1C6ABD9"
},
"Tags": [
{
"Key": "Name",
"Value": "CdkFargateStack/SampleCluster/Vpc/PrivateSubnet1"
}
]
},
"Metadata": {
"aws:cdk:path": "CdkFargateStack/SampleCluster/Vpc/PrivateSubnet1/RouteTable"
}
},
"SampleClusterVpcPrivateSubnet1RouteTableAssociationBC171CD8": {
"Type": "AWS::EC2::SubnetRouteTableAssociation",
"Properties": {
"RouteTableId": {
"Ref": "SampleClusterVpcPrivateSubnet1RouteTable55080EB4"
},
"SubnetId": {
"Ref": "SampleClusterVpcPrivateSubnet1Subnet24256A44"
}
},
"Metadata": {
"aws:cdk:path": "CdkFargateStack/SampleCluster/Vpc/PrivateSubnet1/RouteTableAssociation"
}
},
"SampleClusterVpcPrivateSubnet1DefaultRouteB1C5B147": {
"Type": "AWS::EC2::Route",
"Properties": {
"RouteTableId": {
"Ref": "SampleClusterVpcPrivateSubnet1RouteTable55080EB4"
},
"DestinationCidrBlock": "0.0.0.0/0",
"NatGatewayId": {
"Ref": "SampleClusterVpcPublicSubnet1NATGateway715FE613"
}
},
"Metadata": {
"aws:cdk:path": "CdkFargateStack/SampleCluster/Vpc/PrivateSubnet1/DefaultRoute"
}
},
"SampleClusterVpcPrivateSubnet2Subnet25DCB36D": {
"Type": "AWS::EC2::Subnet",
"Properties": {
"CidrBlock": "10.0.192.0/18",
"VpcId": {
"Ref": "SampleClusterVpcD1C6ABD9"
},
"AvailabilityZone": {
"Fn::Select": [
1,
{
"Fn::GetAZs": ""
}
]
},
"MapPublicIpOnLaunch": false,
"Tags": [
{
"Key": "aws-cdk:subnet-name",
"Value": "Private"
},
{
"Key": "aws-cdk:subnet-type",
"Value": "Private"
},
{
"Key": "Name",
"Value": "CdkFargateStack/SampleCluster/Vpc/PrivateSubnet2"
}
]
},
"Metadata": {
"aws:cdk:path": "CdkFargateStack/SampleCluster/Vpc/PrivateSubnet2/Subnet"
}
},
"SampleClusterVpcPrivateSubnet2RouteTable35B9289E": {
"Type": "AWS::EC2::RouteTable",
"Properties": {
"VpcId": {
"Ref": "SampleClusterVpcD1C6ABD9"
},
"Tags": [
{
"Key": "Name",
"Value": "CdkFargateStack/SampleCluster/Vpc/PrivateSubnet2"
}
]
},
"Metadata": {
"aws:cdk:path": "CdkFargateStack/SampleCluster/Vpc/PrivateSubnet2/RouteTable"
}
},
"SampleClusterVpcPrivateSubnet2RouteTableAssociationC174EB56": {
"Type": "AWS::EC2::SubnetRouteTableAssociation",
"Properties": {
"RouteTableId": {
"Ref": "SampleClusterVpcPrivateSubnet2RouteTable35B9289E"
},
"SubnetId": {
"Ref": "SampleClusterVpcPrivateSubnet2Subnet25DCB36D"
}
},
"Metadata": {
"aws:cdk:path": "CdkFargateStack/SampleCluster/Vpc/PrivateSubnet2/RouteTableAssociation"
}
},
"SampleClusterVpcPrivateSubnet2DefaultRoute74AE4D72": {
"Type": "AWS::EC2::Route",
"Properties": {
"RouteTableId": {
"Ref": "SampleClusterVpcPrivateSubnet2RouteTable35B9289E"
},
"DestinationCidrBlock": "0.0.0.0/0",
"NatGatewayId": {
"Ref": "SampleClusterVpcPublicSubnet2NATGatewayB385D543"
}
},
"Metadata": {
"aws:cdk:path": "CdkFargateStack/SampleCluster/Vpc/PrivateSubnet2/DefaultRoute"
}
},
"SampleClusterVpcIGW21649D5C": {
"Type": "AWS::EC2::InternetGateway",
"Properties": {
"Tags": [
{
"Key": "Name",
"Value": "CdkFargateStack/SampleCluster/Vpc"
}
]
},
"Metadata": {
"aws:cdk:path": "CdkFargateStack/SampleCluster/Vpc/IGW"
}
},
"SampleClusterVpcVPCGW39AFB859": {
"Type": "AWS::EC2::VPCGatewayAttachment",
"Properties": {
"VpcId": {
"Ref": "SampleClusterVpcD1C6ABD9"
},
"InternetGatewayId": {
"Ref": "SampleClusterVpcIGW21649D5C"
}
},
"Metadata": {
"aws:cdk:path": "CdkFargateStack/SampleCluster/Vpc/VPCGW"
}
},
"TaskDefTaskRole1EDB4A67": {
"Type": "AWS::IAM::Role",
"Properties": {
"AssumeRolePolicyDocument": {
"Statement": [
{
"Action": "sts:AssumeRole",
"Effect": "Allow",
"Principal": {
"Service": "ecs-tasks.amazonaws.com"
}
}
],
"Version": "2012-10-17"
}
},
"Metadata": {
"aws:cdk:path": "CdkFargateStack/TaskDef/TaskRole/Resource"
}
},
"TaskDef54694570": {
"Type": "AWS::ECS::TaskDefinition",
"Properties": {
"ContainerDefinitions": [
{
"Cpu": 256,
"Essential": true,
"Image": "st_admin_site:latest",
"Memory": 512,
"Name": "DefaultContainer",
"PortMappings": [
{
"ContainerPort": 8011,
"Protocol": "tcp"
}
]
}
],
"Cpu": "256",
"Family": "CdkFargateStackTaskDef424235B4",
"Memory": "512",
"NetworkMode": "awsvpc",
"RequiresCompatibilities": [
"FARGATE"
],
"TaskRoleArn": {
"Fn::GetAtt": [
"TaskDefTaskRole1EDB4A67",
"Arn"
]
}
},
"Metadata": {
"aws:cdk:path": "CdkFargateStack/TaskDef/Resource"
}
},
"ServiceD69D759B": {
"Type": "AWS::ECS::Service",
"Properties": {
"Cluster": {
"Ref": "SampleClusterB4B72990"
},
"DeploymentConfiguration": {
"MaximumPercent": 200,
"MinimumHealthyPercent": 50
},
"DesiredCount": 2,
"EnableECSManagedTags": false,
"HealthCheckGracePeriodSeconds": 60,
"LaunchType": "FARGATE",
"LoadBalancers": [
{
"ContainerName": "DefaultContainer",
"ContainerPort": 8011,
"TargetGroupArn": {
"Ref": "LBListenerECSGroup1D445DF5"
}
}
],
"NetworkConfiguration": {
"AwsvpcConfiguration": {
"AssignPublicIp": "DISABLED",
"SecurityGroups": [
{
"Fn::GetAtt": [
"ServiceSecurityGroupC96ED6A7",
"GroupId"
]
}
],
"Subnets": [
{
"Ref": "SampleClusterVpcPrivateSubnet1Subnet24256A44"
},
{
"Ref": "SampleClusterVpcPrivateSubnet2Subnet25DCB36D"
}
]
}
},
"TaskDefinition": {
"Ref": "TaskDef54694570"
}
},
"DependsOn": [
"LBListenerECSGroup1D445DF5",
"LBListener49E825B4"
],
"Metadata": {
"aws:cdk:path": "CdkFargateStack/Service/Service"
}
},
"ServiceSecurityGroupC96ED6A7": {
"Type": "AWS::EC2::SecurityGroup",
"Properties": {
"GroupDescription": "CdkFargateStack/Service/SecurityGroup",
"SecurityGroupEgress": [
{
"CidrIp": "0.0.0.0/0",
"Description": "Allow all outbound traffic by default",
"IpProtocol": "-1"
}
],
"VpcId": {
"Ref": "SampleClusterVpcD1C6ABD9"
}
},
"Metadata": {
"aws:cdk:path": "CdkFargateStack/Service/SecurityGroup/Resource"
}
},
"ServiceSecurityGroupfromCdkFargateStackLBSecurityGroupF16A57958011E231ABAF": {
"Type": "AWS::EC2::SecurityGroupIngress",
"Properties": {
"IpProtocol": "tcp",
"Description": "Load balancer to target",
"FromPort": 8011,
"GroupId": {
"Fn::GetAtt": [
"ServiceSecurityGroupC96ED6A7",
"GroupId"
]
},
"SourceSecurityGroupId": {
"Fn::GetAtt": [
"LBSecurityGroup8A41EA2B",
"GroupId"
]
},
"ToPort": 8011
},
"Metadata": {
"aws:cdk:path": "CdkFargateStack/Service/SecurityGroup/from CdkFargateStackLBSecurityGroupF16A5795:8011"
}
},
"LB8A12904C": {
"Type": "AWS::ElasticLoadBalancingV2::LoadBalancer",
"Properties": {
"LoadBalancerAttributes": [
{
"Key": "deletion_protection.enabled",
"Value": "false"
}
],
"Scheme": "internet-facing",
"SecurityGroups": [
{
"Fn::GetAtt": [
"LBSecurityGroup8A41EA2B",
"GroupId"
]
}
],
"Subnets": [
{
"Ref": "SampleClusterVpcPublicSubnet1SubnetE377A512"
},
{
"Ref": "SampleClusterVpcPublicSubnet2SubnetB88D2B08"
}
],
"Type": "application"
},
"DependsOn": [
"SampleClusterVpcPublicSubnet1DefaultRoute28A82BC4",
"SampleClusterVpcPublicSubnet2DefaultRouteFD4087CF"
],
"Metadata": {
"aws:cdk:path": "CdkFargateStack/LB/Resource"
}
},
"LBSecurityGroup8A41EA2B": {
"Type": "AWS::EC2::SecurityGroup",
"Properties": {
"GroupDescription": "Automatically created Security Group for ELB CdkFargateStackLBFC3A10CF",
"SecurityGroupIngress": [
{
"CidrIp": "0.0.0.0/0",
"Description": "Allow from anyone on port 80",
"FromPort": 80,
"IpProtocol": "tcp",
"ToPort": 80
}
],
"VpcId": {
"Ref": "SampleClusterVpcD1C6ABD9"
}
},
"Metadata": {
"aws:cdk:path": "CdkFargateStack/LB/SecurityGroup/Resource"
}
},
"LBSecurityGrouptoCdkFargateStackServiceSecurityGroupB491C33C801194A30A9B": {
"Type": "AWS::EC2::SecurityGroupEgress",
"Properties": {
"GroupId": {
"Fn::GetAtt": [
"LBSecurityGroup8A41EA2B",
"GroupId"
]
},
"IpProtocol": "tcp",
"Description": "Load balancer to target",
"DestinationSecurityGroupId": {
"Fn::GetAtt": [
"ServiceSecurityGroupC96ED6A7",
"GroupId"
]
},
"FromPort": 8011,
"ToPort": 8011
},
"Metadata": {
"aws:cdk:path": "CdkFargateStack/LB/SecurityGroup/to CdkFargateStackServiceSecurityGroupB491C33C:8011"
}
},
"LBListener49E825B4": {
"Type": "AWS::ElasticLoadBalancingV2::Listener",
"Properties": {
"DefaultActions": [
{
"TargetGroupArn": {
"Ref": "LBListenerECSGroup1D445DF5"
},
"Type": "forward"
}
],
"LoadBalancerArn": {
"Ref": "LB8A12904C"
},
"Port": 80,
"Protocol": "HTTP"
},
"Metadata": {
"aws:cdk:path": "CdkFargateStack/LB/Listener/Resource"
}
},
"LBListenerECSGroup1D445DF5": {
"Type": "AWS::ElasticLoadBalancingV2::TargetGroup",
"Properties": {
"Port": 8011,
"Protocol": "HTTP",
"TargetGroupAttributes": [
{
"Key": "stickiness.enabled",
"Value": "false"
}
],
"TargetType": "ip",
"VpcId": {
"Ref": "SampleClusterVpcD1C6ABD9"
}
},
"Metadata": {
"aws:cdk:path": "CdkFargateStack/LB/Listener/ECSGroup/Resource"
}
},
"CDKMetadata": {
"Type": "AWS::CDK::Metadata",
"Properties": {
"Analytics": "v2:deflate64:H4sIAAAAAAAA/31Ry27CMBD8Fu7GBSr1TilFSFUVJYhr5ThbumDWkR9BKMq/184D0lbqaWdn18nMzoLPZ3w2ERc7lcVpqjDndeaEPLFAfdQgLa9XylsHhq0 aYCvwhyEg52wpxf4REKHmuLCb0aTE0hgRlz/NgNToYT4qIcNA7ng9b6UkdwnK5b4XKHMfE7g2sUbSrWPv88V3Pk7t7RWSxSDqHYQwXqbxPIu3CYouIgrSwxWUcztw1sK/gIeFjolfbd04TRfZyDHMpDeoLtujPZlZ I/YksHA9b 4dct3TAUZ16nurMTaziGEtahVFoUuVCCJNKhCvdZlmU4SmvuLcye21kXz49 vIchNep3Bjya70IkwfKgfNQ2DUvBam 6pMY4ZFu0iTaMdAH8aB q ROfP/LF5GgRp8aTwzPwtKvfgpQF22sCAAA="
},
"Metadata": {
"aws:cdk:path": "CdkFargateStack/CDKMetadata/Default"
},
"Condition": "CDKMetadataAvailable"
}
},
TEST
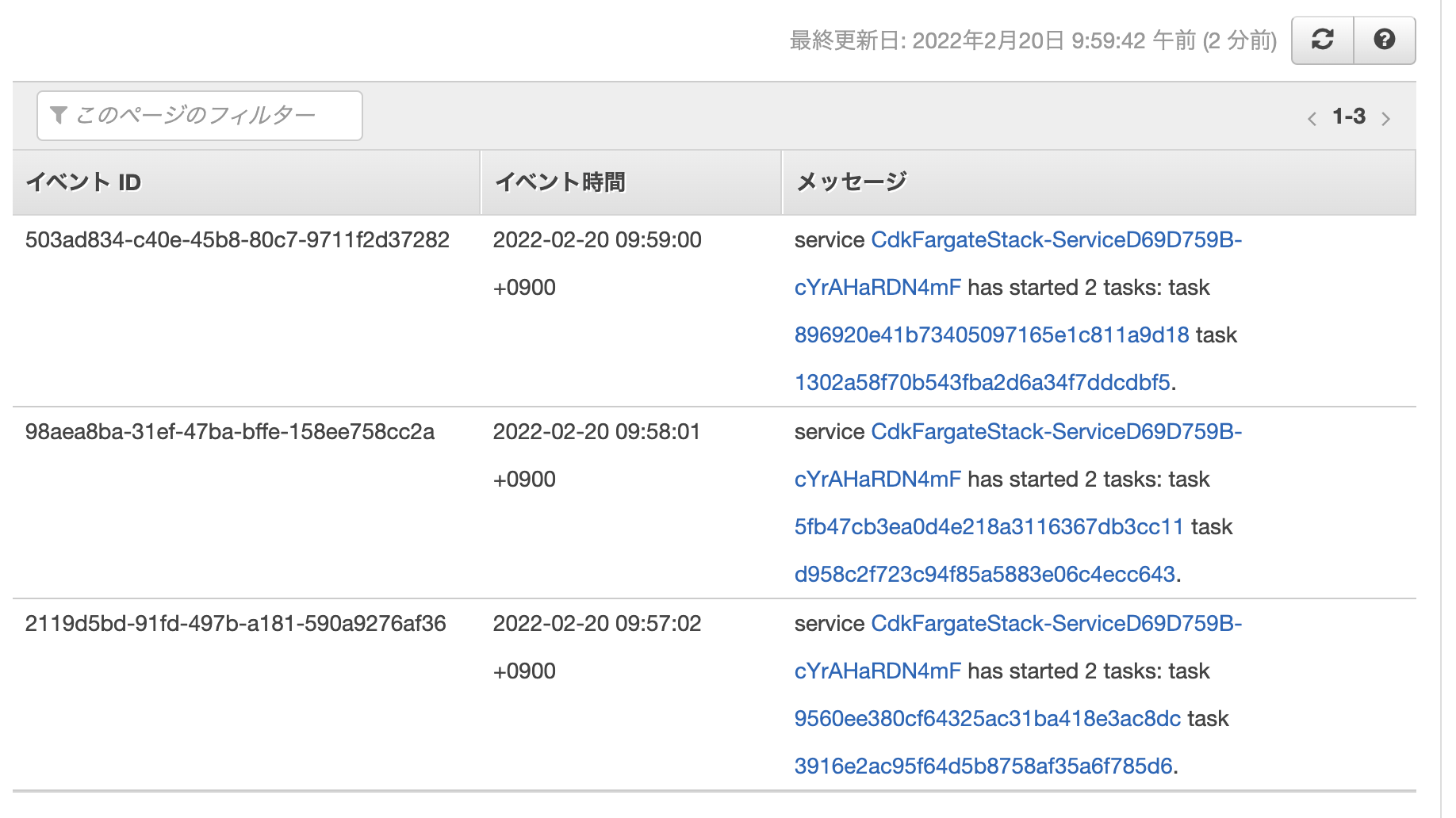
I am checking the log in in aws web console.
Cluster > AdminCluster > service: CdkFargateStack-ServiceD69D759B-cYrAHaRDN4mF
in event tab,
There are log like this
Service tries to start the task every one minutes.
TEST
ECS supports docker-compose style deployment.
So I try this with same image, then it works well
$docker context ls
default * moby Current DOCKER_HOST based configuration unix:///var/run/docker.sock swarm
desktop-linux moby unix:///Users/whitebear/.docker/run/docker.sock
docker-lamp-ecs ecs
$docker context use docker-lamp-ecs
$docker compose docker-compose.yml up
this deployment finished correctly container starts on ECS
However it fails in CDK.
SOLUTION
I found out the solution.
This could work
const adminRepo = ecr.Repository.fromRepositoryArn(this, 'AdminRepository', 'arn:aws:ecr:ap-northeast-1:678100XXXXXX:repository/st_admin_site')
const adminImage = ecs.ContainerImage.fromEcrRepository(adminRepo,"latest");
The previous code,
const adminImage = ecs.ContainerImage.fromRegistry('st_admin_site:latest')
it doesn't mean to get my ecrRepository....
I use ARN instead.
This is stupid mistakes.
However there is not the way to get the log.
So it takes long time to find out.
Thank you for your help.
CodePudding user response:
I had some stacks that took more than 30 minutes in the past :D How long were you waiting ?
What was the resources part looking ? What was already created, what was still "in action" :) ?
Did something crashed while creating and was in multiple retries ?
CodePudding user response:
Not much information to really know what's happening, but IIRC if your container fails to start it will fail to create the ECS service. You can check if the service was actually created in the ECS console, and if it exists, check the event log to see if they aren't failing. If they are failing, you can check the reason in the task.