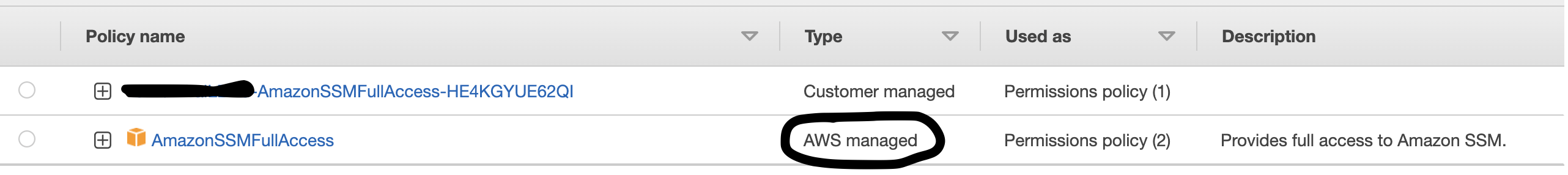
I want to add AWS managed policy (AmazonSSMFullAccess) to a role using CloudFormation.
I tried to use AWS::IAM::ManagedPolicy but it creates a Customer Managed policy and I don't want that. I want it to be AWS managed.
Do you have any idea how can I do that?
I am trying to add AWS managed AmazonSSMFullAccess and here is the code I am using in mu CF template:
AmazonSSMFullAccess:
Type: AWS::IAM::ManagedPolicy
Properties:
PolicyDocument:
Version: '2012-10-17'
Statement:
- Effect: Allow
Action:
- 'cloudwatch:PutMetricData'
- 'ds:CreateComputer'
- 'ds:DescribeDirectories'
- 'ec2:DescribeInstanceStatus'
- 'logs:*'
- 'ssm:*'
- 'ec2messages:*'
Resource: '*'
- Effect: Allow
Action: 'iam:CreateServiceLinkedRole'
Resource: >-
arn:aws:iam::*:role/aws-service-role/ssm.amazonaws.com/AWSServiceRoleForAmazonSSM*
Condition:
StringLike:
'iam:AWSServiceName': ssm.amazonaws.com
- Effect: Allow
Action:
- 'iam:DeleteServiceLinkedRole'
- 'iam:GetServiceLinkedRoleDeletionStatus'
Resource: >-
arn:aws:iam::*:role/aws-service-role/ssm.amazonaws.com/AWSServiceRoleForAmazonSSM*
- Effect: Allow
Action:
- 'ssmmessages:CreateControlChannel'
- 'ssmmessages:CreateDataChannel'
- 'ssmmessages:OpenControlChannel'
- 'ssmmessages:OpenDataChannel'
Resource: '*'
CodePudding user response:
You can't create AWS managed policies, because only AWS can do it. You, as an AWS customer can only create customer managed policies.