I made the CodePipeline to build the source code from CodeCommit to ECR by cdk
When deploying this cdk code, somehow the key named like this
codepipeline-cdkmynavirepomynavipipelinefe7f8d68 is made in KMS customer managed key
I am not sure why this is made, and I don't want to use this.
Why or where this key is made?
const adminPipeline = new codepipeline.Pipeline(this, 'mynaviPipeline', {
pipelineName: 'cdk-mynavi-pl',
});
const mynavi_cc_repo_name = 'cdk-mynavi-cc'
const mynavi_cc_repo = new codecommit.Repository(this,
"mynavi-cc-repo",{
repositoryName: mynavi_cc_repo_name,
description:"for resizer repo"
})
const adminBuildProject = new codebuild.PipelineProject(this, 'adminBuildproject', {
environment: {
buildImage:codebuild.LinuxBuildImage.STANDARD_4_0,
privileged:true,
},
buildSpec: codebuild.BuildSpec.fromSourceFilename("./buildspec.yml")
});
const adminSourceOutput = new codepipeline.Artifact();
const adminSourceAction = new cdk.aws_codepipeline_actions.CodeCommitSourceAction({
actionName: 'AdminSource',
repository: mynavi_cc_repo,
output: adminSourceOutput,
trigger: cdk.aws_codepipeline_actions.CodeCommitTrigger.POLL,
})
const dockerHubSecretArn = 'arn:aws:secretsmanager:ap-northeast-1:678100228231:secret:docker_login-TBFA5B';
const dockerHubSecret = secretsmanager.Secret.fromSecretCompleteArn(this, 'SecretFromCompleteArn', dockerHubSecretArn);
dockerHubSecret.grantRead(adminBuildProject)
cronEcrRepo.grantPullPush(adminBuildProject)
djangoEcrRepo.grantPullPush(adminBuildProject)
nginxEcrRepo.grantPullPush(adminBuildProject)
const adminBuildOutput = new codepipeline.Artifact();
const adminBuildAction = new cdk.aws_codepipeline_actions.CodeBuildAction({
actionName: 'AdminCodeBuild',
project: adminBuildProject,
input: adminSourceOutput,
outputs: [adminBuildOutput]
});
adminPipeline.addStage({
stageName: "mynaviSource",
actions: [adminSourceAction],
});
adminPipeline.addStage({
stageName : "mynaviBuild",
actions: [adminBuildAction]
});
CodePudding user response:
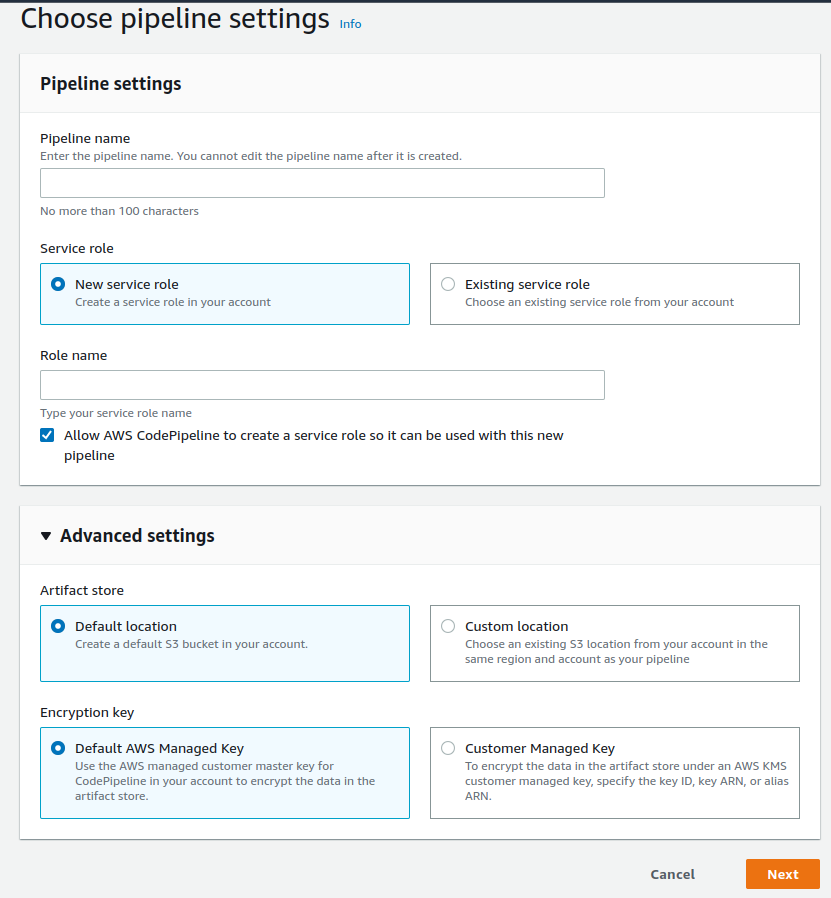
It has to do with encryption at rest.
Data in CodePipeline is encrypted at rest using AWS KMS keys. Code artifacts are stored in a customer-owned S3 bucket and encrypted with either the AWS managed key or a customer managed key.
Encrypting codepipline artifacts is enabled by default.
If you choose the default option for encrypting code artifacts, CodePipeline uses the AWS managed key. You cannot change or delete this AWS managed key.
You cannot disable the encryption, but you can choose how you encrypt the artifacts.
The good thing is that if you go with the default option, you don't have to manage the encryption keys.
This can be, for example, selected in the CodePipeline console:
More on Data Protection in AWS CodePipeline.