I'm trying to create a policy for all members of a group that will grant the user's access to particular S3 buckets based on a Tag value set on the user's account.
For example, my user has tag environment=staging, and I want to use this value to access buckets in s3 with the name staging -- for example: my-${environment}-bucket.
Here's what my policy looks like:
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "VisualEditor0",
"Effect": "Allow",
"Action": [
"s3:PutObject",
"s3:GetObject",
"s3:DeleteObject"
],
"Resource": "arn:aws:s3:::my-${aws:PrincipalTag/environment}-bucket/*"
},
{
"Sid": "VisualEditor1",
"Effect": "Allow",
"Action": [
"s3:CreateBucket",
"s3:ListBucket",
"s3:DeleteBucket"
],
"Resource": "arn:aws:s3:::my-${aws:PrincipalTag/environment}-bucket"
}
]
}
Currently this isn't working. I must be missing something.
EDIT:
I'm using the IAM Policy Simulator tool (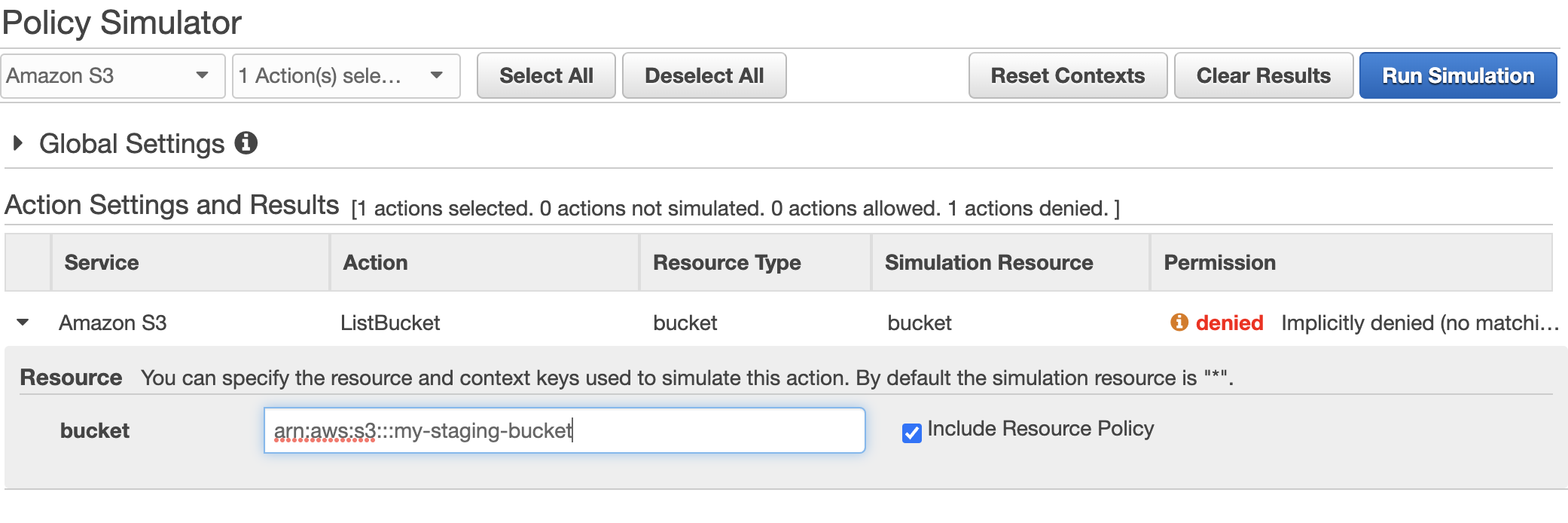
CodePudding user response:
I've been able to achieve the desired behavior. Here's a minimal reproducible example:
- I created a user "foobar" with no permissions. I gave this user a tag
environmentwith the valuetest. I gave this user the following inline policy:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "s3:ListBucket",
"Resource": "arn:aws:s3:::*${aws:PrincipalTag/environment}*"
}
]
}
- I created two buckets, one called
mydevbucketand another calledmytestbucket. I added one file to themytestbucket, "foo.txt". - I logged in the AWS account as the "foobar" user, and tried to navigate to the two buckets:
https://s3.console.aws.amazon.com/s3/buckets/mytestbucket?region=eu-west-2&tab=objectsfor the test bucket,https://s3.console.aws.amazon.com/s3/buckets/mydevbucket?region=eu-west-2&tab=objectsfor the dev bucket.
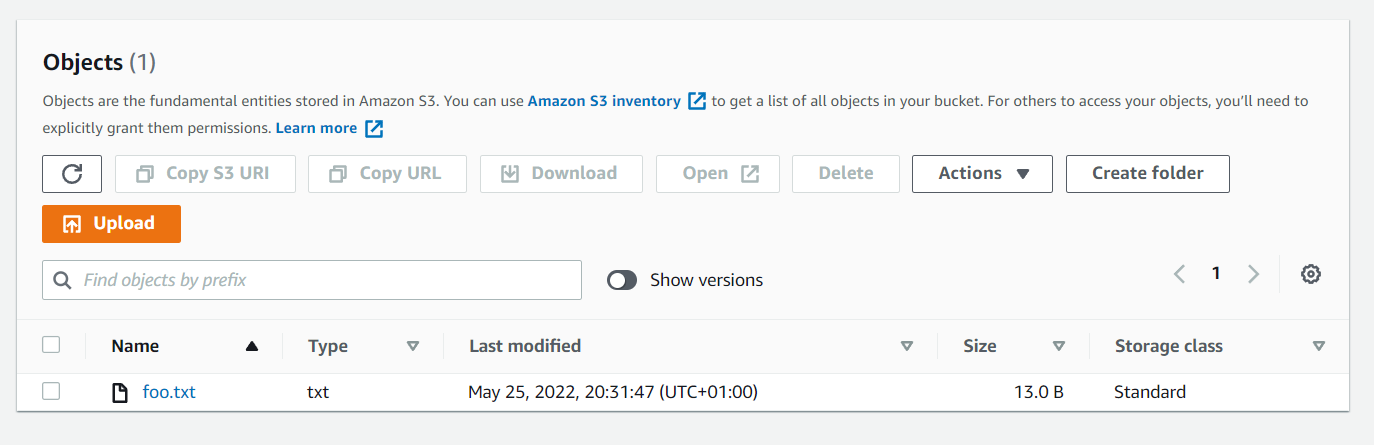
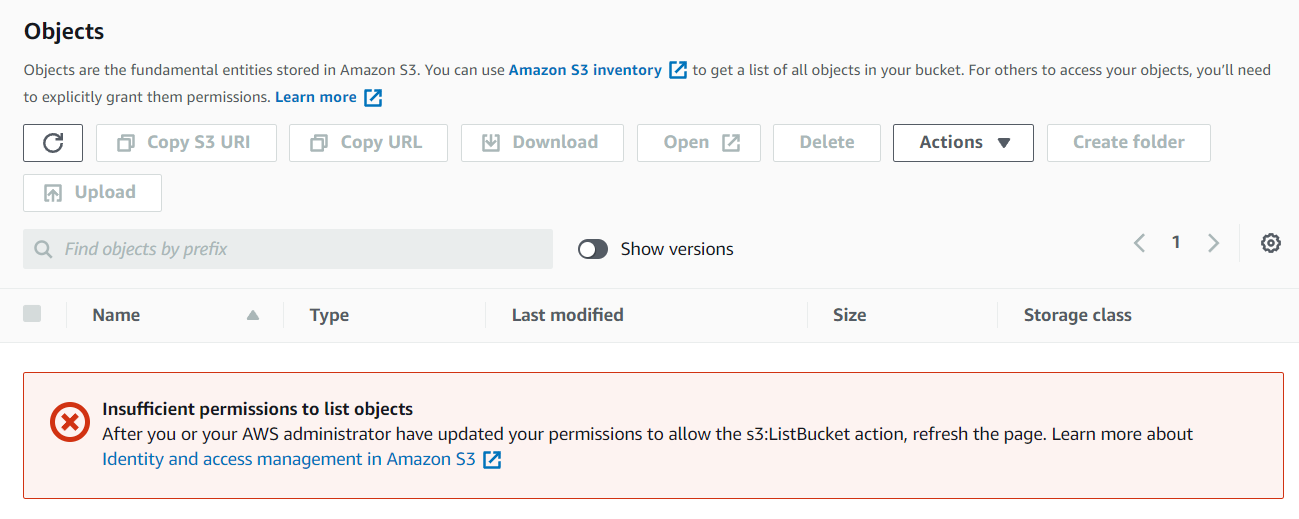
As expected, I can only see the test bucket (because theenvironmenttag has a the valuetest):
whereas in the dev bucket:
CodePudding user response:
I discovered that my policy does indeed work if I test programmatic access from the CLI. For example:
aws s3api list-objects --bucket my-staging-bucket --profile staging-user Returns results
aws s3api list-objects --bucket my-test-bucket --profile staging-user Shows Access Denied
However, I was unable to get my policy to work through the IAM Policy Simulator Tool. If anyone can explain this as part of this question, I think it could help others with similar experience.