I have faced issue with a Jenkins.
Some details:
I am using AWS Credentials 1.33 plugin
Role was created in AWS IAM. (Action : "sts:AssumeRole")
Policy was applied to that role. (Action : "ec2:Describe*")
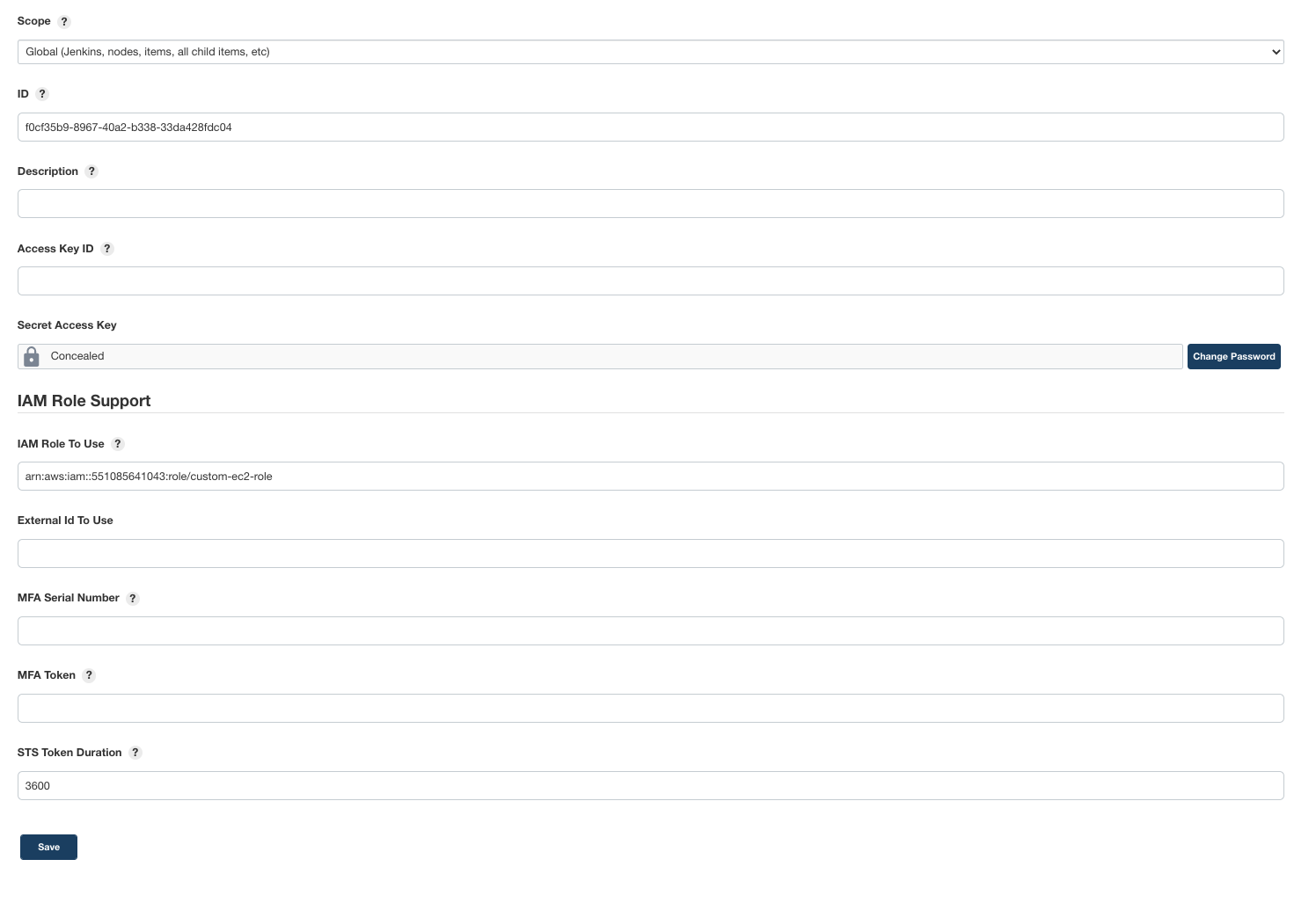
Credentials storing in Jenkins
Stage definition from the pipeline:
stage('Run aws command') {
steps {
withCredentials([[$class: 'AmazonWebServicesCredentialsBinding',credentialsId: "f0cf35b9-8967-40a2-b338-33da428fdc04", accessKeyVariable: 'AWS_ACCESS_KEY_ID', secretKeyVariable: 'AWS_SECRET_ACCESS_KEY']]) {
container('aws-cli') {
sh('env')
sh('aws sts get-caller-identity')
}
}
}
}
But I get following error in Jenkins:
[Pipeline] { (Run aws command)
[Pipeline] withCredentials
[Pipeline] // withCredentials
[Pipeline] }
[Pipeline] // stage
[Pipeline] }
[Pipeline] // timeout
[Pipeline] }
[Pipeline] // node
[Pipeline] }
[Pipeline] // podTemplate
[Pipeline] End of Pipeline
com.amazonaws.SdkClientException: Unable to load AWS credentials from any provider in the chain: [EnvironmentVariableCredentialsProvider: Unable to load AWS credentials from environment variables (AWS_ACCESS_KEY_ID (or AWS_ACCESS_KEY) and AWS_SECRET_KEY (or AWS_SECRET_ACCESS_KEY)), SystemPropertiesCredentialsProvider: Unable to load AWS credentials from Java system properties (aws.accessKeyId and aws.secretKey), WebIdentityTokenCredentialsProvider: You must specify a value for roleArn and roleSessionName, com.amazonaws.auth.profile.ProfileCredentialsProvider@59f986be: profile file cannot be null, com.amazonaws.auth.EC2ContainerCredentialsProviderWrapper@49ac96d0: Failed to connect to service endpoint: ]
at com.amazonaws.auth.AWSCredentialsProviderChain.getCredentials(AWSCredentialsProviderChain.java:136)
at com.amazonaws.http.AmazonHttpClient$RequestExecutor.getCredentialsFromContext(AmazonHttpClient.java:1269)
at com.amazonaws.http.AmazonHttpClient$RequestExecutor.runBeforeRequestHandlers(AmazonHttpClient.java:845)
at com.amazonaws.http.AmazonHttpClient$RequestExecutor.doExecute(AmazonHttpClient.java:794)
at com.amazonaws.http.AmazonHttpClient$RequestExecutor.executeWithTimer(AmazonHttpClient.java:781)
at com.amazonaws.http.AmazonHttpClient$RequestExecutor.execute(AmazonHttpClient.java:755)
at com.amazonaws.http.AmazonHttpClient$RequestExecutor.access$500(AmazonHttpClient.java:715)
at com.amazonaws.http.AmazonHttpClient$RequestExecutionBuilderImpl.execute(AmazonHttpClient.java:697)
at com.amazonaws.http.AmazonHttpClient.execute(AmazonHttpClient.java:561)
at com.amazonaws.http.AmazonHttpClient.execute(AmazonHttpClient.java:541)
at com.amazonaws.services.securitytoken.AWSSecurityTokenServiceClient.doInvoke(AWSSecurityTokenServiceClient.java:1727)
at com.amazonaws.services.securitytoken.AWSSecurityTokenServiceClient.invoke(AWSSecurityTokenServiceClient.java:1694)
at com.amazonaws.services.securitytoken.AWSSecurityTokenServiceClient.invoke(AWSSecurityTokenServiceClient.java:1683)
at com.amazonaws.services.securitytoken.AWSSecurityTokenServiceClient.executeAssumeRole(AWSSecurityTokenServiceClient.java:532)
at com.amazonaws.services.securitytoken.AWSSecurityTokenServiceClient.assumeRole(AWSSecurityTokenServiceClient.java:501)
at com.cloudbees.jenkins.plugins.awscredentials.AWSCredentialsImpl.getCredentials(AWSCredentialsImpl.java:161)
at com.cloudbees.jenkins.plugins.awscredentials.AmazonWebServicesCredentialsBinding.bind(AmazonWebServicesCredentialsBinding.java:124)
at org.jenkinsci.plugins.credentialsbinding.impl.BindingStep$Execution2.doStart(BindingStep.java:132)
at org.jenkinsci.plugins.workflow.steps.GeneralNonBlockingStepExecution.lambda$run$0(GeneralNonBlockingStepExecution.java:77)
at java.base/java.util.concurrent.Executors$RunnableAdapter.call(Executors.java:515)
at java.base/java.util.concurrent.FutureTask.run(FutureTask.java:264)
at java.base/java.util.concurrent.ThreadPoolExecutor.runWorker(ThreadPoolExecutor.java:1128)
at java.base/java.util.concurrent.ThreadPoolExecutor$Worker.run(ThreadPoolExecutor.java:628)
at java.base/java.lang.Thread.run(Thread.java:829)
Finished: FAILURE
Thank you
CodePudding user response:
AWS Credential Provider Chain
The error message tells you everything you need to know. AWS supports a variety of ways for a client to provide authentication information. They are a "chain" because each type has its own order of precedence.
From your screenshot it's evident that you are not even configuring the the AWS ACCESS_KEY and SECRET in your credential manager. You are leaving them blank, and then trying to establish a variable to hold the (blank) value in your withCredentials step.
For proof you can attempt to print
print "${AWS_ACCESS_KEY_ID}"
It will return nothing.
Solution
Add the access key and the secret key to the credential record you are referencing in your withCredential step. You don't even need to get the retrieve the values.
withCredentials([[$class: 'AmazonWebServicesCredentialsBinding',credentialsId: "f0cf35b9-8967-40a2-b338-33da428fdc04"]]) {
container('aws-cli') {
sh('env')
sh('aws sts get-caller-identity')
}
}
Also you might need withCredentials inside container
