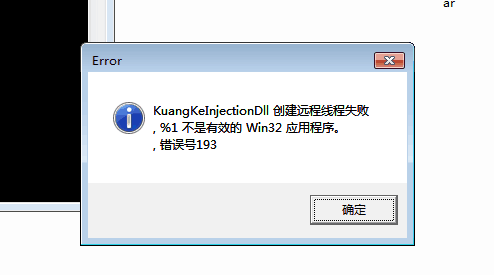
Known to modify the program to achieve this effect, PE but through test protection is not modified PE, so to solve any other ways to make CreateRemoteThreadex failed to create the remote thread, tip is not a valid win32 application,
CodePudding user response:
Fyi:/*
Application: Code Injection in Explorer
Author: @ _RT
Compiled on: Feb 2014
URL:http://www.codeproject.com/Tips/732044/Code-Injection-2
We will see the company's steps involved to perform a code injection into an already running process.
Following are the quick steps through the process of injection.
1. Get the API addresses that will be calling from the injected code.
2. Prepare the shell code of your function that you want to get executed from the injected process.
3. Get the process ID of the running process that wish to inject into by enumerating through the
A list of the processes or by finding the process 's window (in case it' s a GUI application) by the class name or title.
4. Open the process using its Pid with All Access rights.
5. The Allocate company's memory Spaces in the process that you are going to inject the to with desired access
Does the for holding the company segments of your shell code.
Code part (the executable instructions)
The Data part (strings, the function parameters, etc.)
6. Write the allocated memories with the respective values (code and data).
7. Call CreateRemoteThread API and pass it to the start of the allocated memory address where you have
Written your shell code from the process we are injecting.
*/
# include & lt; Windows. H>
# pragma comment (lib, "user32. Lib")
LPVOID addr.
LPVOID addr2;
BOOL InjectExecutable (DWORD dwPid LPVOID si, LPVOID PI, int sisize, int pisize)
{
LPVOID hNewModule;
HANDLE hProcess;
CHAR [] S={" C: \ \ Windows \ \ system32 \ \ notepad exe "};
X6a BYTE byt []={0, 0 x00 to 0 x6a, 0 x00 to 0 x6a, 0 x00 to 0 x6a, 0 x01, 0 x6a, 0 x00 to 0 x6a, 0 x00 to 0 x6a, 0 x00 to 0 x68};
//push 0, push 0, push 0, 1, push push 0, push 0, push 0, push 0 XXXXXXXXX
BYTE byt2 []=xe8 {0};//call 0 XXXXXXXXX
BYTE byt3 []=x68 {0};//push 0 XXXXXXXXX
HProcess=OpenProcess (PROCESS_ALL_ACCESS, FALSE, dwPid);
If (hProcess==NULL)
{
return FALSE;
}
LPVOID staddr=VirtualAllocEx (hProcess, NULL, sizeof (S), MEM_COMMIT, PAGE_READWRITE);
WriteProcessMemory (hProcess, staddr, S, sizeof (S), NULL);
LPVOID fnaddr=VirtualAllocEx (hProcess, NULL, 4, MEM_COMMIT, PAGE_READWRITE);
WriteProcessMemory (hProcess, fnaddr, PI, sisize, NULL);
LPVOID fnaddr2=VirtualAllocEx (hProcess, NULL, 4, MEM_COMMIT, PAGE_READWRITE);
WriteProcessMemory (hProcess, fnaddr2, si, pisize, NULL);
HNewModule=VirtualAllocEx (hProcess, NULL, 100, MEM_COMMIT, PAGE_EXECUTE_READWRITE);
If (hNewModule==NULL)
{
return FALSE;
}
LPTHREAD_START_ROUTINE strtaddr=(LPTHREAD_START_ROUTINE hNewModule);
WriteProcessMemory (hProcess, hNewModule byt3, sizeof (byt3), NULL);
HNewModule=(LPVOID) ((int) hNewModule + sizeof (byt3));
WriteProcessMemory (hProcess, hNewModule, & amp; Fnaddr, sizeof (fnaddr), NULL);
HNewModule=(LPVOID) ((int) hNewModule + sizeof (fnaddr));//push & amp; PI; LpProcessInformation
WriteProcessMemory (hProcess, hNewModule byt3, sizeof (byt3), NULL);
HNewModule=(LPVOID) ((int) hNewModule + sizeof (byt3));
WriteProcessMemory (hProcess, hNewModule, & amp; Fnaddr2, sizeof (fnaddr2), NULL);
HNewModule=(LPVOID) ((int) hNewModule + sizeof (fnaddr2));//push & amp; Si; LpStartupInfo
WriteProcessMemory (hProcess, hNewModule, byt, sizeof (byt), NULL);//push 0, push 0, push 0, 1, push push 0, push 0, push 0, push 0 XXXXXXXXX==& amp; S [0];" C: \ \ Windows \ \ system32 \ \ notepad exe
"HNewModule=(LPVOID) ((int) hNewModule + sizeof (byt));//lpCurrentDirectory lpEnvironment, dwCreationFlags bInheritHandles, lpThreadAttributes, lpProcessAttributes, lpCommandLine, lpApplicationName
WriteProcessMemory (hProcess, hNewModule, & amp; Staddr, sizeof (staddr), NULL);
HNewModule=(LPVOID) ((int) hNewModule + sizeof (staddr));
WriteProcessMemory (hProcess, hNewModule byt2, sizeof (byt2), NULL);
HNewModule=(LPVOID) ((int) hNewModule + sizeof (byt2));//call CreateProcessA
Addr=(LPVOID) ((int) addr - ((int) hNewModule + 4));
WriteProcessMemory (hProcess, hNewModule, & amp; Addr, sizeof (addr), NULL);
HNewModule=(LPVOID) ((int) hNewModule + sizeof (addr));
WriteProcessMemory (hProcess, hNewModule, byt, 2, NULL);
HNewModule=(LPVOID) ((int) hNewModule + 2);//push 0; DWORD dwExitCode//exit code for this thread
WriteProcessMemory (hProcess, hNewModule byt2, sizeof (byt2), NULL);
HNewModule=(LPVOID) ((int) hNewModule + sizeof (byt2));//call ExitThread
Addr2=(LPVOID) ((int) addr2 - ((int) hNewModule + 4));
nullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnull
