I am testing an environment where I have the credentials of a service principal of an application. My next step is to identify the objects owned by the application or the resources that the app can access.
I could get similar details for an AD user through the cli command
ad signed-in-user list-owned-objects
Running the same command when signed-in with the credentials of the sp results in the following error
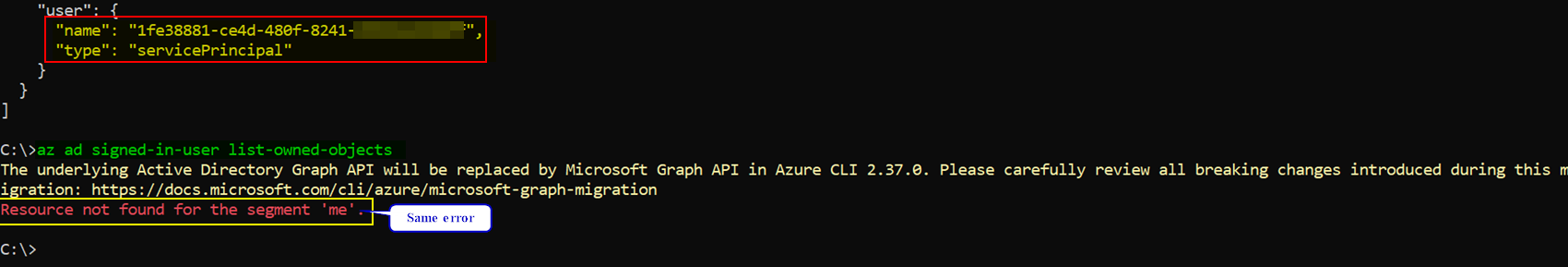
Resource not found for the segment 'me'.
My use-case is to enumerate the SP account to understand its access rights in the subscription. Can someone help me out with the right set of azure cli commands.
CodePudding user response:
I tried to reproduce the same in my environment and got below results:
I created one service principal with Storage Blob Data Contributor role at storage account scope like below:
az ad sp create-for-rbac --role "Storage Blob Data Contributor" --name <spname> --scopes /subscriptions/<subID>/resourceGroups/<rgname>/providers/Microsoft.Storage/storageAccounts/<storaccname>
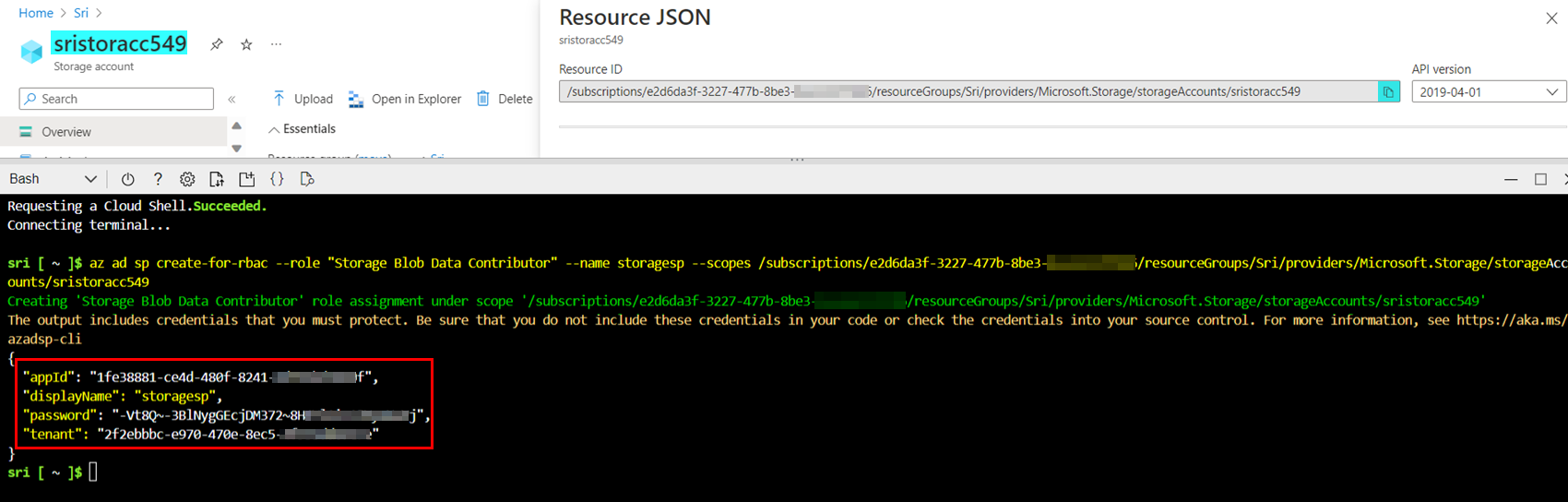
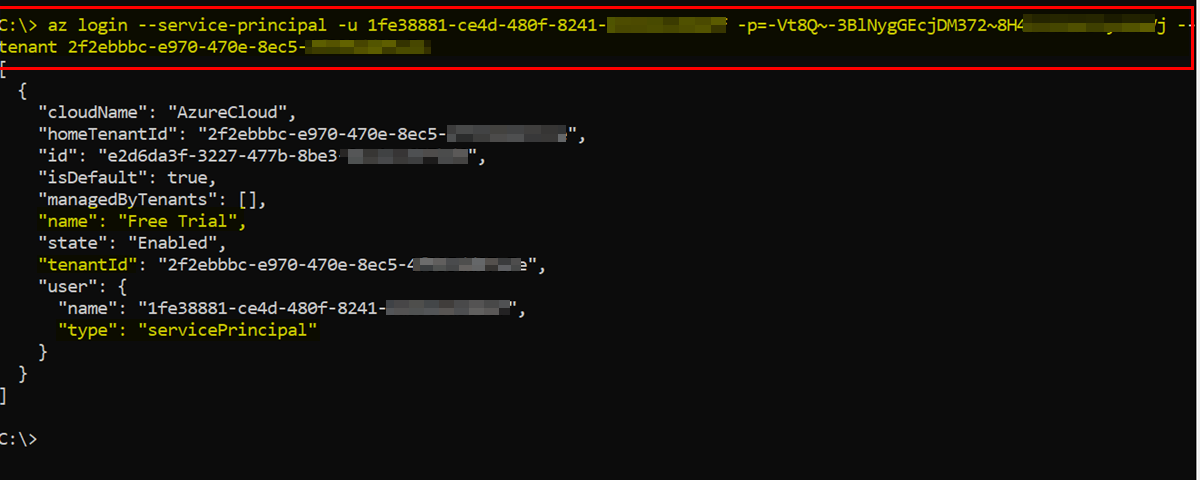
Now I logged in to Azure account successfully using above service principal credentials:
az login --service-principal -u appID -p password --tenant tenantID
When I ran the same command to get the resources that the app can access, I got same error as below:
az ad signed-in-user list-owned-objects
To list RBAC roles assigned to a service principal, you can make use of below command:
az role assignment list --assignee <service_principal_ID> --all
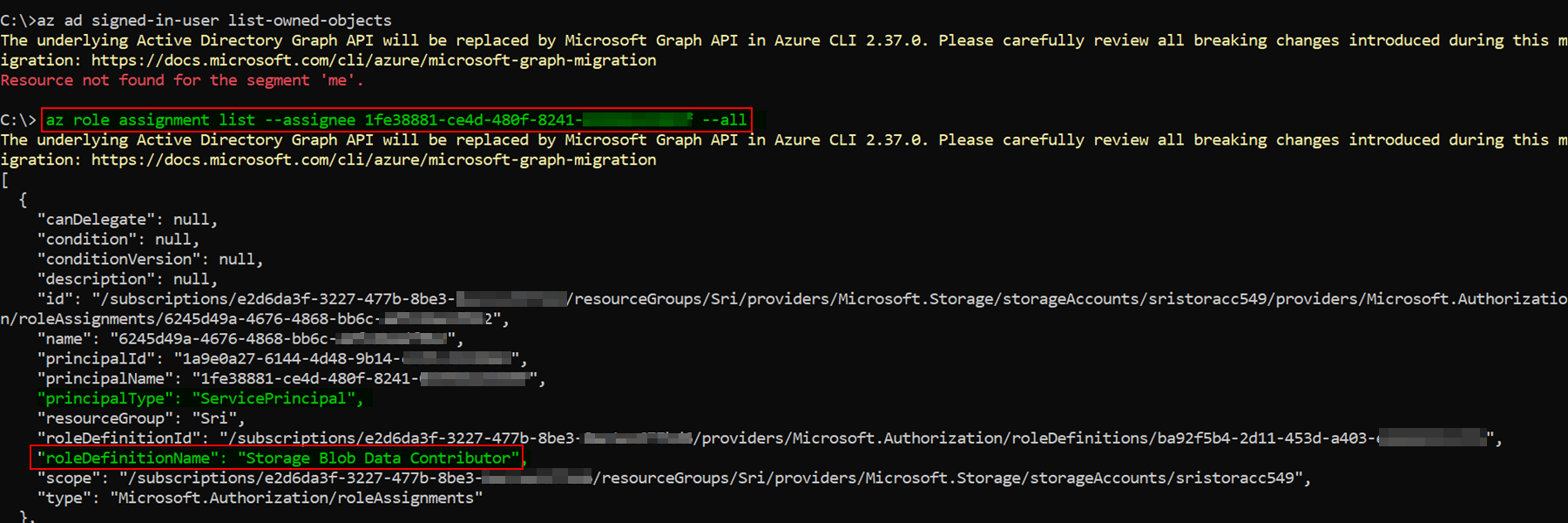
If your use case is to list all the resources/objects a service principal can access/own, currently there is no command available particularly for that.
To know more in detail, you can check below reference:
