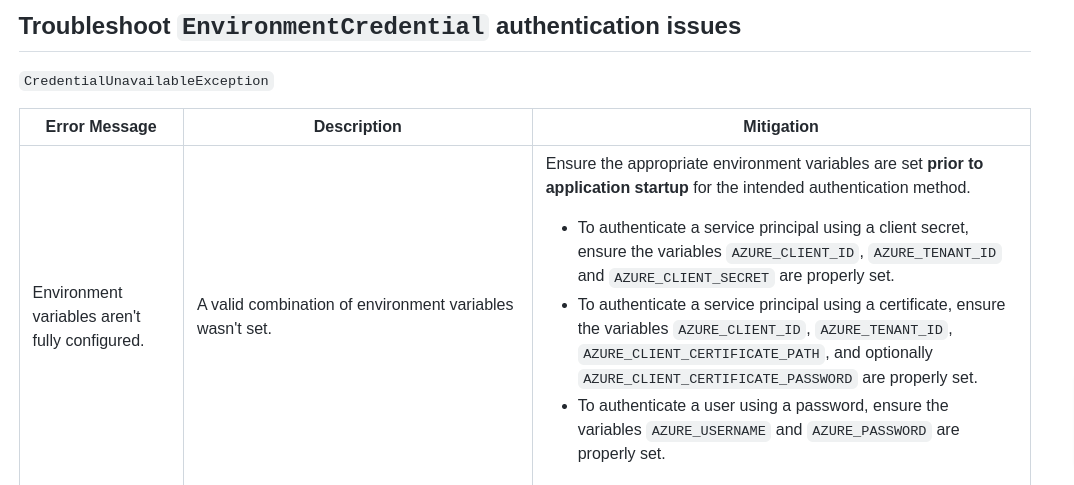
I am trying to use System Assigned Managed Identities with my Azure Function App. I do not want to do local debugging, just run the function through an API call. According to the documentation, if I wanted to do local debugging, I could set
AZURE_TENANT_ID
AZURE_CLIENT_SECRET
AZURE_CLIENT_ID
and then the function app would like for these in my local environment when doing local debugging, but as I said I am not doing local debugging (hitting endpoint through postman by way of API Management) so those ENV vars should not be included.
My confusion comes because when I remove them, I receive the following error:
EnvironmentCredential authentication unavailable. Environment variables are not fully configured. See the troubleshooting guide for more information. https://aka.ms/azsdk/net/identity/environmentcredential/troubleshoot
And the horrible irony of this error message is that it seems to be telling me that I need to set those ENV variables, even though I should not need to.
I must be mixing something up here, can someone see where my mistake is?
FYI - I am not a C# developer, so if you were going to require those ENV variables I listed above, where would you do that in the code? I'm wondering if they set things to always do local somehow, so it's requiring them.
CodePudding user response:
I realized my issue. I hadn't realized that one of the developers had added EnvironmentCredential() to the code, so it was always looking for the AZURE_CLIENT_ID, which is what broke things when removing the AZURE_CLIENT_ID.
The reason they added it was understandable though, they need to access a b2c tenant account's graph API and as of right now I am not sure how to give that permission through a MI instead of an App Registration, so for us it seems managed identities won't work well sadly. We did not want to tightly couple config and code by requiring a large number of ENV variables to gain access to various services, but it seems like we would need to do that to make things work. We also were running into local testing issues with eventgrid and System Assigned MI because it seems locally the user who is an owner of the subscription, is not able to write to eventgrid topics and we weren't able to find a way around that which seemed clean
CodePudding user response:
In my case, I had a similar error and I was searching in the wrong direction.
I only changed DefaultAzureCredintials to AzureCliCredintials.
from azure.identity import DefaultAzureCredential
Replaced with:
from azure.identity import AzureCliCredential
Then it was solved. source ;github azure-identity