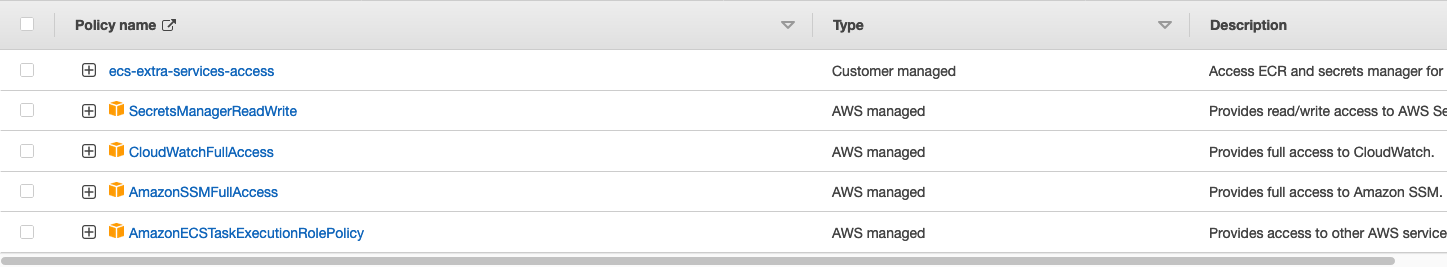
ecs-extra-services-access:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"ecr:GetAuthorizationToken",
"ecr:BatchCheckLayerAvailability",
"ecr:GetDownloadUrlForLayer",
"ecr:BatchGetImage",
"logs:CreateLogStream",
"logs:PutLogEvents",
"logs:CreateLogGroup"
],
"Resource": "*"
},
{
"Effect": "Allow",
"Action": [
"kms:Decrypt",
"ssm:GetParameters",
"secretsmanager:GetSecretValue",
"secretsmanager:GetResourcePolicy",
"secretsmanager:GetSecretValue",
"secretsmanager:DescribeSecret",
"secretsmanager:ListSecretVersionIds",
"secretsmanager:ListSecrets"
],
"Resource": [
"arn:aws:secretsmanager:us-west-2:576765093341:secret:prod/ecr-private-registry",
"arn:aws:kms:us-west-2:576765093341:key/807cbd08-a0ce-4948-b681-a49c7553003a"
]
}
]
}
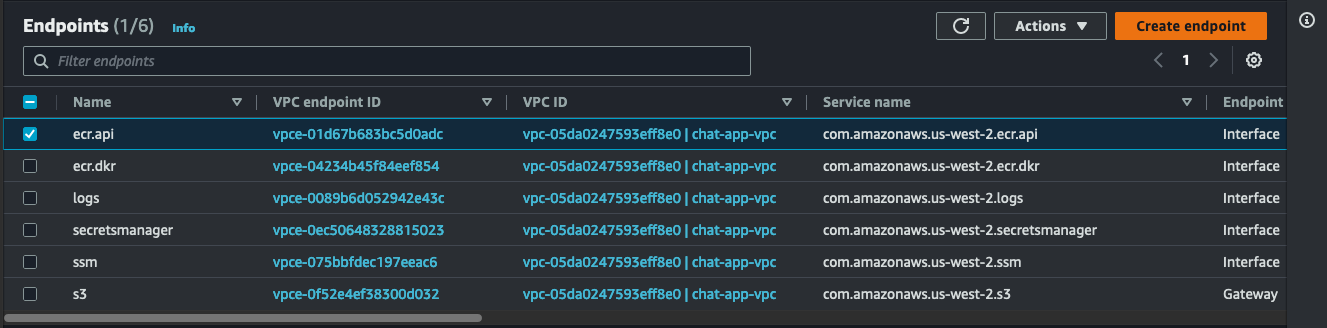
VPC Endpoints
These are attached to the public subnets.
Endpoint Policy for com.amazonaws.us-west-2.secretsmanager
{
"Statement": [
{
"Sid": "AccessSpecificAccount",
"Principal": {
"AWS": "*"
},
"Action": "secretsmanager:*",
"Effect": "Allow",
"Resource": "*"
}
]
}
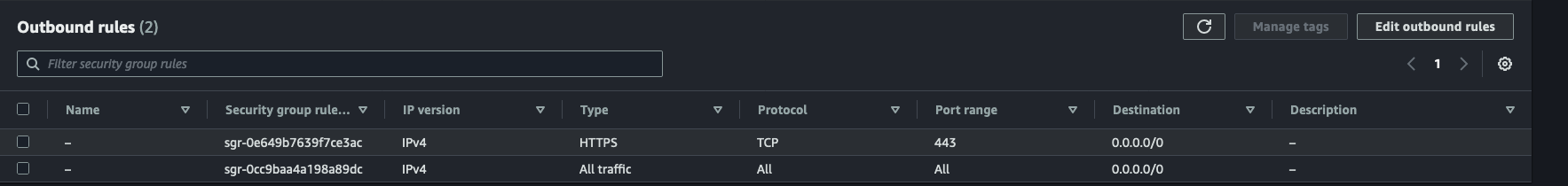
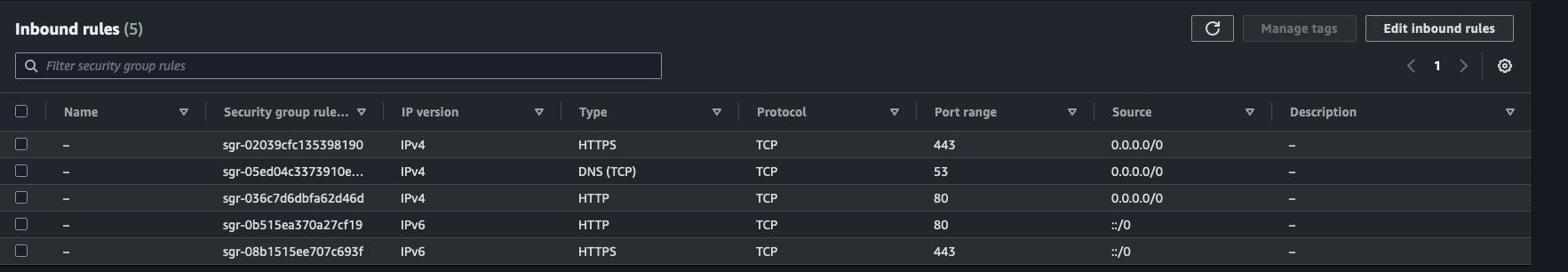
Security Group
Applies to ECS task and all endpoints
Other configs
- Task definition public IP create enabled
- Subnets public IP create enabled
- VPC DNS resolution and hostnames enabled
- Created repositories docker images with the flag
--endpoint-url https://api.ecr.us-west-2.amazonaws.com - Tried using ECR private registry permissions but they are "Not allowed" with no specified reason.
I also want to note that there are no logs being generated which makes me suspicious the entire taskExecutionRole (my extra permissions policy) is not being applied somehow.
CodePudding user response:
I launched the task in the default VPC with zero config (default security group) and it worked. Something wrong with my VPC config.
CodePudding user response:
I want to add that I was able to create a custom VPC and get it working but it would always fail if I created the VPC with this module.
https://registry.terraform.io/modules/terraform-aws-modules/vpc/aws/latest