Cloud git code address: https://gitee.com/lougd/snifferview.git
Compiled executable file: https://pan.baidu.com/s/1CPKh5cWyIog2Fbn7XHFxmQ
Author contact: qq: 412776488 mail:[email protected]
If feel this tool helps you please point a star, thank you!
Development record:
This tool is the first version of the 2015, because often have to work on different terminal PC caught analysis network protocol, has been caught by the wireshark analysis, wireshark installer is bigger, every time we pack too trival, also does not support the loopback network packet capture, then do it yourself a own packet protocol analysis tool, and there was the first version of this tool, then the function of the rich while using tools, have this version of the now,
Main functions and features:
The tool is not a demo, it is a stable, practical and available, relatively perfect in functions of network packets, analysis tools, if you need regular network packet capture, analysis, record can use this tool,
Support local all card network packet sniffer captures, including 127 addresses the loopback package,
Support similar wireshark packet filter statement, convenient and flexible to network packet filtering,
Support TCP flow tracing function, convenient tracking single TCP data flow,
Support process state detection network, which can be convenient to check the status of the specified process network,
Support has capture network data import and export, can easily ready to dump the captured network data,
Small tools, green (more than 1 MB, there is only one executable file), without any rely on, start running speed,
C + + language development, vs2008 integration tool development tools compile, open the project root directory with vs2008 SnifferView. SLNS project file can be compiled, detected
Tool function screenshots:
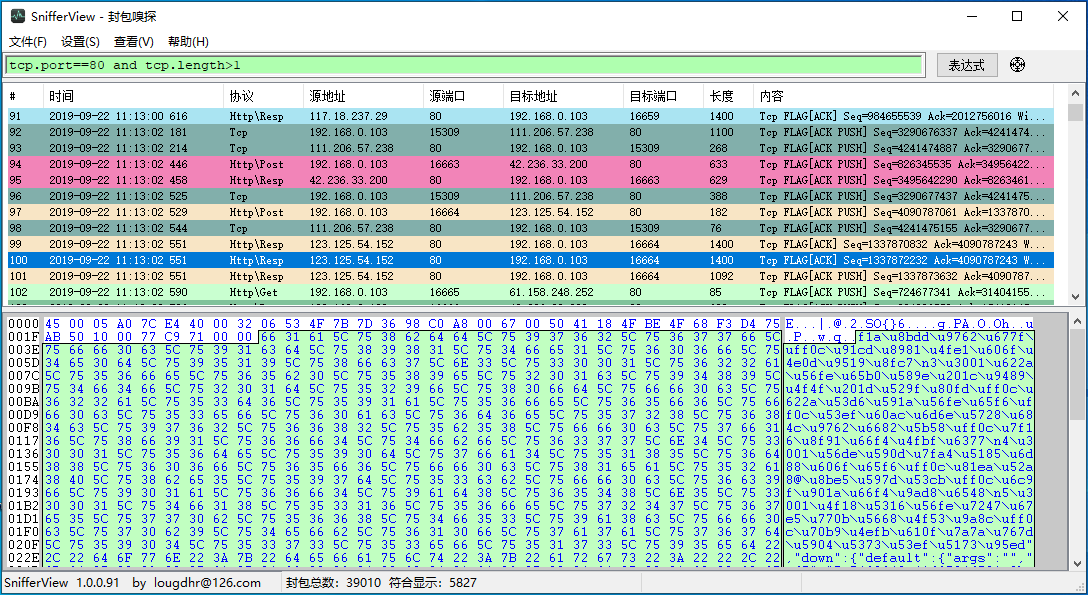
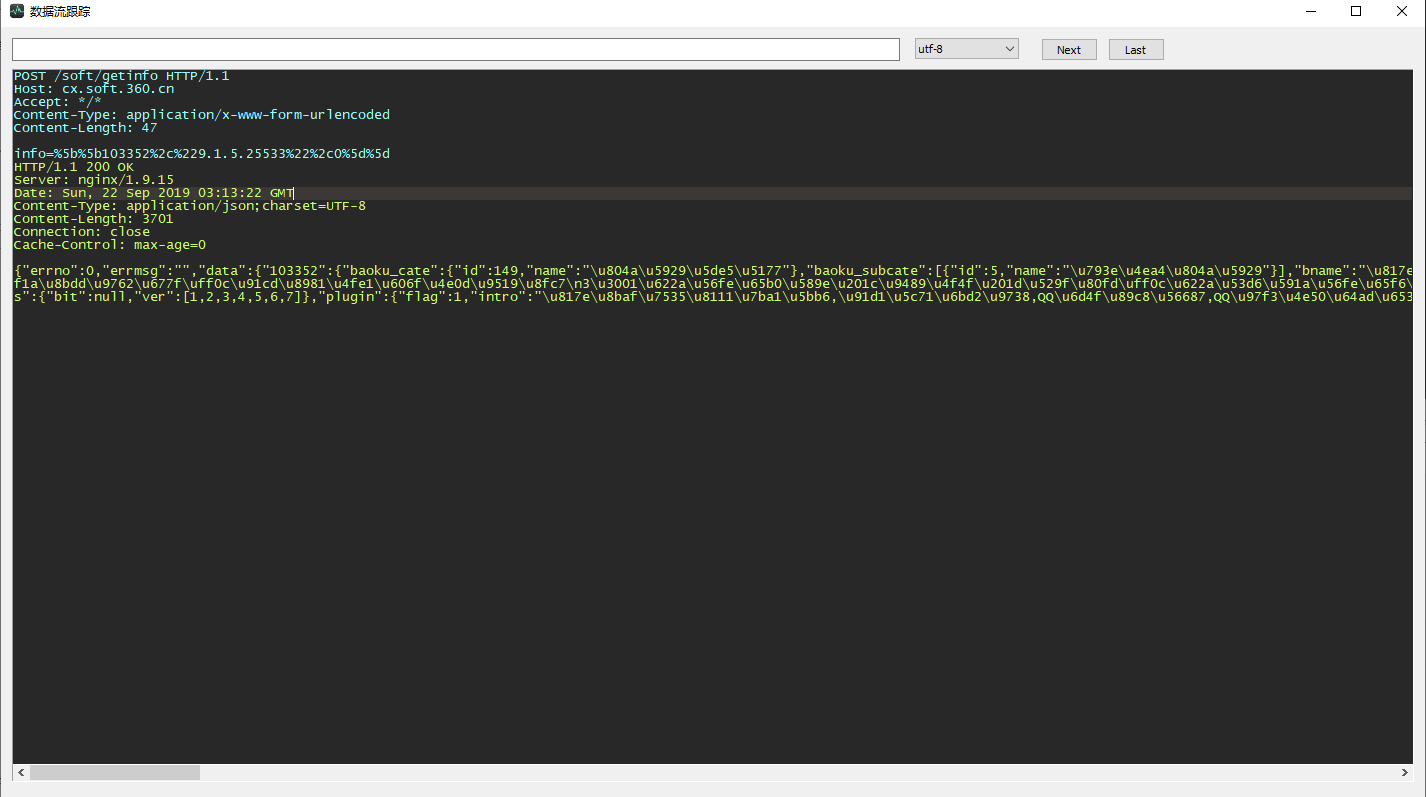
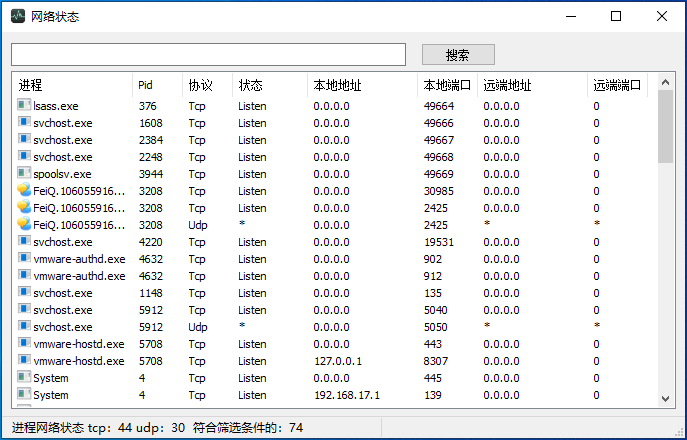
Software architecture
ComLib sub project:
Based static library functions, for each function to provide the basis of general functional components,
SnifferView sub project:
Main function module, the realization of the main functions, including the network packet sniffer, filter statement compiling parser implementation, network protocol analysis, data flow check, etc.,
Dumper sub project:
Exception handling processing module, capture not handle exceptions and generate abnormal dump and abnormal log, is applied to the analysis of abnormal reason,
SyntaxView sub project:
Syntax highlighting control, based on the Scintilla transformation, TCP data flow is used to display data,
Use the
Only one executable program, this program started packet sniffer program starts, but at this time because there is no filter statement, capture the packet will be a lot of, can be in the main interface of filtering rules box enter the appropriate filtering rules to capture network packets of interest, the specific filtering rules and the type of wireshark, and made some optimization, the main rules as follows,
SnifferView filtering rules:
SnifferView filter syntax, for example:
. IP addr==192.168.168.231 filtering IP source address or destination address for 192.168.168.231 network packet
The icmp filtering icmp protocol packet
Filtering tcp.src=https://bbs.csdn.net/topics/=8345 TCP source port 8345 network packet
TCP. Length> 128 filter length is greater than 128 bytes of TCP packets, the length of excluding the IP header and the TCP header
TCP contains "GET" filter content contained in the GET string TCP packet
TCP==0 x12ff filtering TCP user data migration take a 32-bit data size for 4 bytes 0 x12ff packet
TCP. Flag. The syn filter have a syn TCP packet
TCP=="GET" filter TCP user data migration O bytes for the GET packet
HTTP filter HTTP protocol
HTTP. Get filtering HTTP get agreement
Filter. The HTTP post HTTP post agreement
HTTP. Resp filtering HTTP return package
HTTP, url contains "img" HTTP url filtering img string contained in the packet
Filtering rules of key words:
IP layer: IP, IP addr, IP, SRC, IP, DST, IP. Length
The icmp layer: icmp
TCP layer: the TCP port, TCP. SRC, TCP. DST, TCP. Length, TCP. Flag. The syn | ack | fin | RST | PSH | urg, TCP (for migration, b is a specific data type, not a mean deviation of 0), TCP contains "aaa" (TCP packet contains the string aaa)
Udp layer:, similar to TCP
The application layer protocol:
HTTP protocol: HTTP, HTTP get, HTTP. Post, HTTP. Head, HTTP. Options, HTTP. Put, HTTP. Delete, HTTP. Tarce, HTTP, url contains "aaa" (HTTP url contains aaa packet)
Filtering rules to the type of data (for TCP or udp) :
N8 (8-bit unsigned integer), n16 (16-bit unsigned integer), and n32 by mechanical blending (32-bit unsigned integer), byte (n8), bytes (byte list), the char type (characters), chars (string)
Filtering rules of logical connection identifier:
(greater than), & lt; (less than), & gt;=(greater than or equal to), & lt;=(less than or equal to),==(equal),!=(is not equal to), & amp; (with)
Each filter expressions can be used and (& amp; & amp;) Or the or (| |) to connect, you can use parentheses such as gain length is larger than 128 GET packages or POST package:
TCP. Length> 128 and (TCP=="GET" or TCP=="POST")
SnifferView syntax relatively wireshark main improvements:
Wireshark filter packet content grammar is so of TCP, when a is offset, b to match the length of the migration started with TCP header and the TCP header or longer, and only in bytes each match, it's very inconvenient to use, we usually focus on is not the contents of the TCP header, but the content of the user data, thus SnifferView filter content when migration starts from the user data, the program automatically calculates the length of the TCP header, support a variety of data types match, automatically calculate the length of the match, if the match of the string of \ n \ r will automatically change as the carriage return and line feed,
For example:
TCP==0 x33ee from the user data migration 4 bytes to match a 16-bit integer data, size of 0 x33ee
TCP=="aaaa" from the user data migration 5 bytes matching a string aaaa
On configuring interface in host byte order and network byte order:
Selected in host byte order means that the packet data is stored in host byte order way, choose the network byte order mean packet in the data is stored in the network byte order,
For example:
TCP==0 x12345678
If choose host byte order will start where user data migration 4 bytes, in turn, match 0 x78, 0 x56, 0 x34, 0 x12
If selected is network byte order will start where user data migration 4 bytes, in turn, match 0 x12, 0 x34, 0 x56, 0 x78
About the author
Qq: 412776488 mail:[email protected]
Have questions or Suggestions you can contact the author, thank you!
CodePudding user response:
Thank you for the original poster to shareCodePudding user response:

Support the open source
CodePudding user response:

Thumb up
CodePudding user response:

CodePudding user response:

CodePudding user response:

CodePudding user response:
Praised, the building or an open source protocol is better!