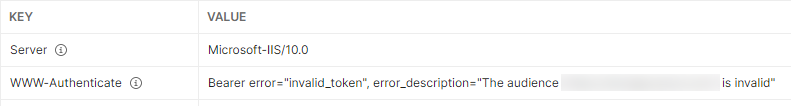
I'm authenticating with a service principal that was setup by another developer. I'm trying to authenticate against an internally developed API. The ASP is working when the other developer uses the SDK to authenticate. But when I try with Postman, I'm getting a 401 with this error.
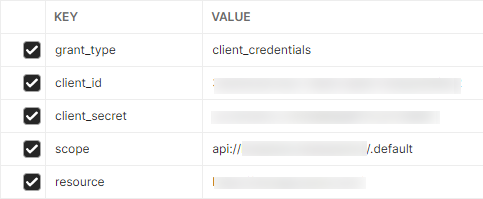
The issue is that I don't really know which resource to use. I believe the client ID, secret, and scope is correct. But I can't seem to find any info on the type of resource to use. Is there any way to determine this for an internally developed API? I've used a ton of publicly available ones. Just as testing, as I can't find any info. And leaving it blank does not work.
CodePudding user response:
Assuming you have two applications created in azure ad app registration, one representing the client application and the other representing the api application, (or in app registration you must have selected the required client application) and then you must be using the client application to call the Web api application. NOTE: When you call web API , make sure you are sending Access token (not Id token)
- you track the token you get in jwt.io . Azure AD audience must match the “aud” claim when. The Audience must equal the AppId or client id set for the application. Check iss value of token in jwt.io and see the version of login url. If it is v2 set manifest json in the app registration for the API to 2, as it may be by default be 2. "accessTokenAcceptedVersion": 2
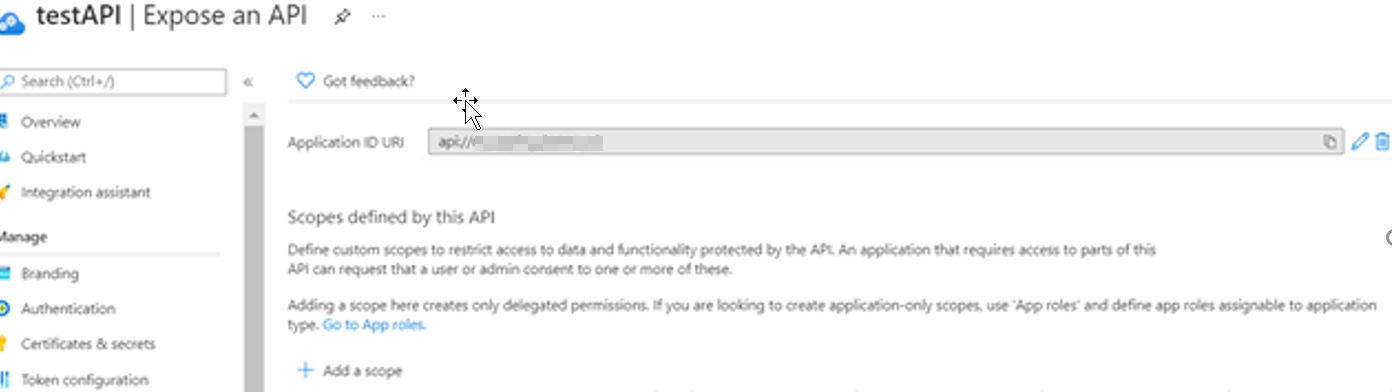
- In the app registration if your exposed api is something like : api://xxxx-xxx-xxx ,then the client id in appsettings.json of your app must be the same.
Note:Client id may be configured differently according to application. If above doesn't work try client ID : instead of api://
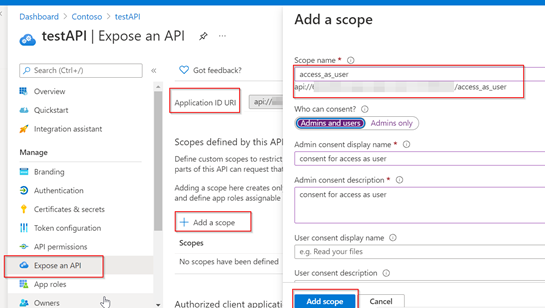
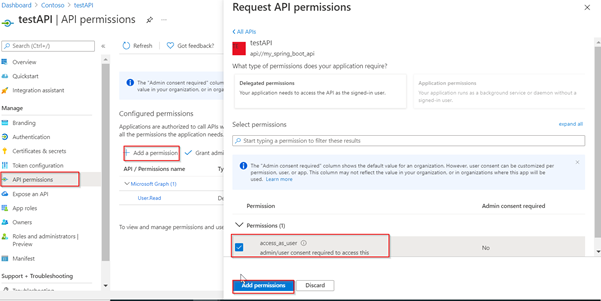
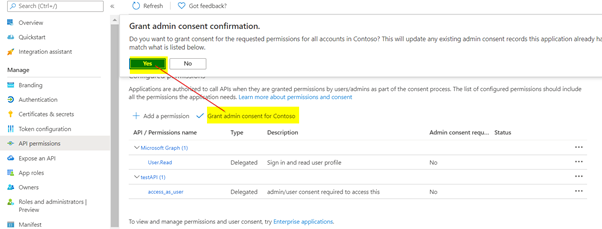
- You may need to grant application permissions to your client applications (this is the role permissions you define yourself, you can find it in My APIs when you add permissions).Then you need to click the admin consent button to grant administrator consent for this permission.
Here I exposed scope >> api://xxx-xxx-xxx/access_as_user. Make sure to use the same scope configured in portal is included in application configuration. The scope should include the exposing resource's identifier (the Application ID URI) in the code too. Here Ex: scopes: "api://xxxx-xxx-xxxx/access_as_user "
In postman Set Authorization header to refer a global variable 'Bearer {{bearerToken}}' and add the authorization data to Request Headers, If you are using postman call back uri , uncheck the authorize using browser for callbackurl in postman configuration.(see enable-azure-ad-authentication| csharpcorner )