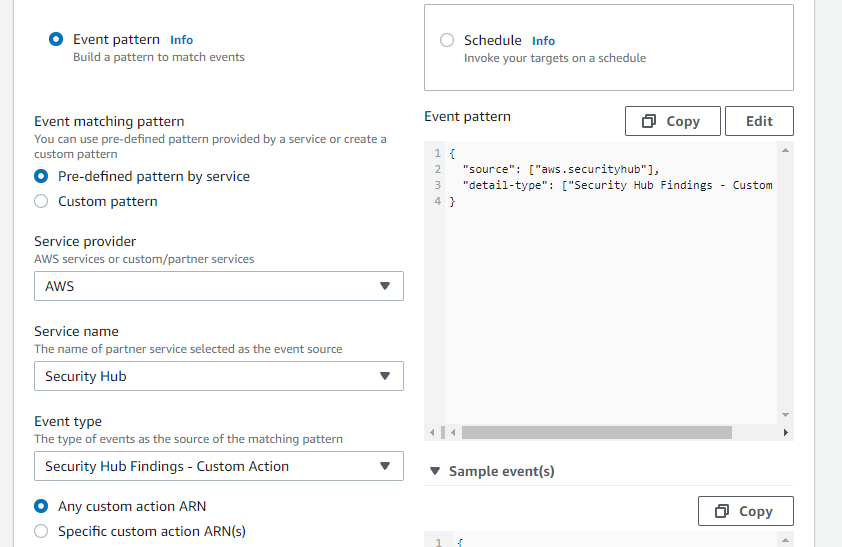
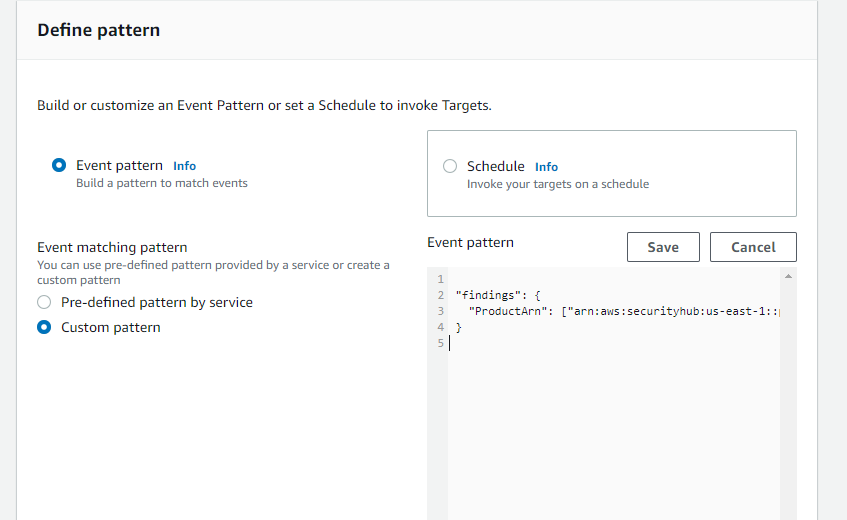
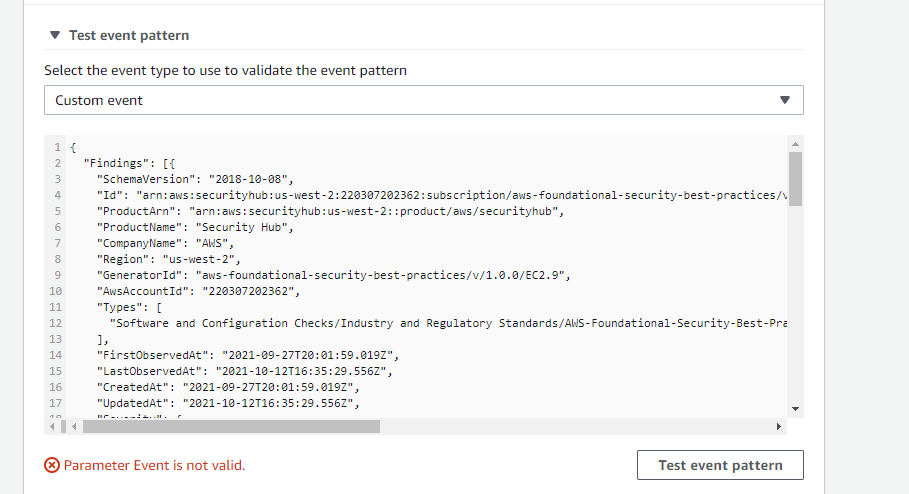
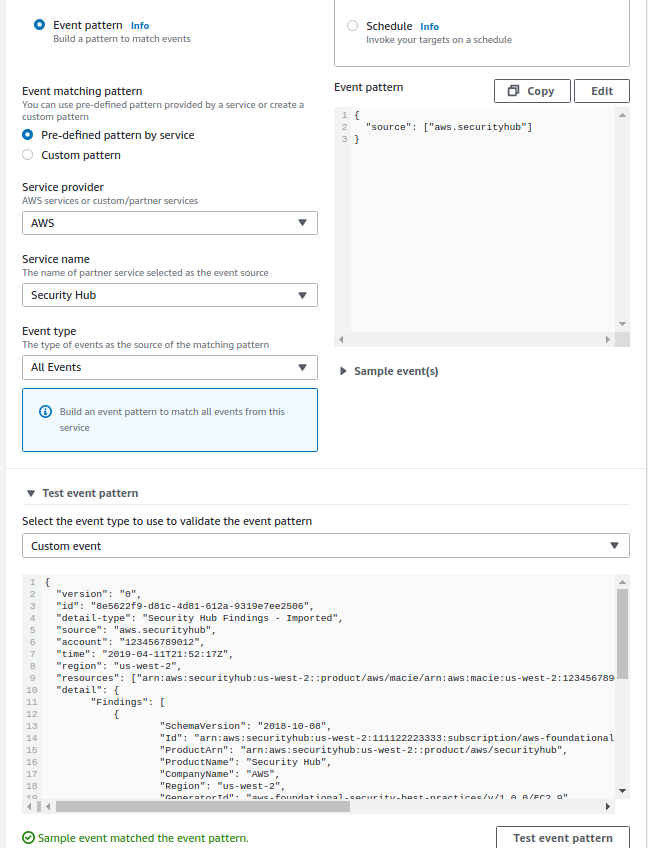
I am trying to create a EventBridge Rule for a "event" pattern as below :
My Json Structure :
{
"Findings": [
{
"SchemaVersion": "2018-10-08",
"Id": "arn:aws:securityhub:us-west-2:220307202362:subscription/aws-foundational-security-best-practices/v/1.0.0/EC2.9/finding/eeecfc8d-cb70-4686-8615-52d488f87959",
"ProductArn": "arn:aws:securityhub:us-west-2::product/aws/securityhub",
"ProductName": "Security Hub",
"CompanyName": "AWS",
"Region": "us-west-2",
"GeneratorId": "aws-foundational-security-best-practices/v/1.0.0/EC2.9",
"AwsAccountId": "220311111111",
"Types": [
"Software and Configuration Checks/Industry and Regulatory Standards/AWS-Foundational-Security-Best-Practices"
],
"FirstObservedAt": "2021-09-27T20:01:59.019Z",
"LastObservedAt": "2021-10-12T16:35:29.556Z",
"CreatedAt": "2021-09-27T20:01:59.019Z",
"UpdatedAt": "2021-10-12T16:35:29.556Z",
"Severity": {
"Product": 0,
"Label": "INFORMATIONAL",
"Normalized": 0,
"Original": "INFORMATIONAL"
},
"Title": "EC2.9 EC2 instances should not have a public IPv4 address"
}
]
}
My Json structure does not looks like Event pattern shown in above picture on right hand side so i thought of modifying the event pattern something like as per my json posted above.As soon as i Edit the event pattern the option on the left hand side changes to "custom pattern" as below :
When i try to test my above json it gives me error as below :
What I am missing here ? How I can configure my event Hub findings such that it is able to identify my above json and it go go to my target (Kinesis firehose) ?
CodePudding user response:
In test event pattern, you need write full event including items like version, id,...
Event pattern JSON is:
{
"version": "0",
"id": "8e5622f9-d81c-4d81-612a-9319e7ee2506",
"detail-type": "Security Hub Findings - Imported",
"source": "aws.securityhub",
"account": "123456789012",
"time": "2019-04-11T21:52:17Z",
"region": "us-west-2",
"resources": ["arn:aws:securityhub:us-west-2::product/aws/macie/arn:aws:macie:us-west-2:123456789012:integtest/trigger/6294d71b927c41cbab915159a8f326a3/alert/f2893b211841"],
"detail": {
"Findings": [{
"SchemaVersion": "2018-10-08",
"Id": "arn:aws:securityhub:us-west-2:111122223333:subscription/aws-foundational-security-best-practices/v/1.0.0/EC2.9/finding/eeecfc8d-cb70-4686-8615-52d488f87959",
"ProductArn": "arn:aws:securityhub:us-west-2::product/aws/securityhub",
"ProductName": "Security Hub",
"CompanyName": "AWS",
"Region": "us-west-2",
"GeneratorId": "aws-foundational-security-best-practices/v/1.0.0/EC2.9",
"AwsAccountId": "220311111111",
"Types": [
"Software and Configuration Checks/Industry and Regulatory Standards/AWS-Foundational-Security-Best-Practices"
],
"FirstObservedAt": "2021-09-27T20:01:59.019Z",
"LastObservedAt": "2021-10-12T16:35:29.556Z",
"CreatedAt": "2021-09-27T20:01:59.019Z",
"UpdatedAt": "2021-10-12T16:35:29.556Z",
"Severity": {
"Product": 0,
"Label": "INFORMATIONAL",
"Normalized": 0,
"Original": "INFORMATIONAL"
},
"Title": "EC2.9 EC2 instances should not have a public IPv4 address"
}]
}
}
You can now use Test Event.
It's confusing that Event pattern and Test Event pattern is too far. The attributes like source is treated in EventBridge automatically.
For detecting specific attribute, "Event type->Security Hub Findings-Imported" might be useful.