I'm trying to upload some api permission to my app registration in Azure, but I don't get why for some the process work and for others no. 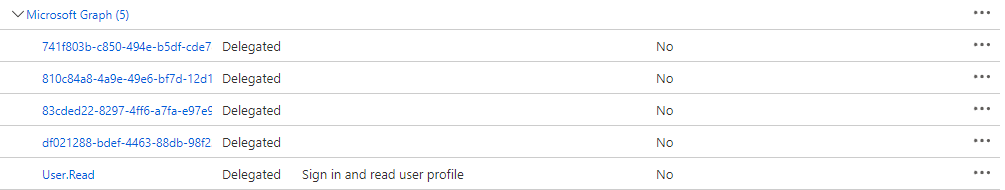
$svcGraph = Get-AzureADServicePrincipal -All $true | ? { $_.DisplayName -eq "Microsoft Graph" }
$Graph = New-Object -TypeName "Microsoft.Open.AzureAD.Model.RequiredResourceAccess"
$Graph.ResourceAppId = $svcGraph.AppId
$delPermission1 = New-Object -TypeName "Microsoft.Open.AzureAD.Model.ResourceAccess" -ArgumentList "df021288-bdef-4463-88db-98f22de89214","Scope"
$delPermission2 = New-Object -TypeName "Microsoft.Open.AzureAD.Model.ResourceAccess" -ArgumentList "e1fe6dd8-ba31-4d61-89e7-88639da4683d","Scope"
$Graph.ResourceAccess = $delPermission1, $delPermission2
Set-AzureADApplication -ObjectId $MyAppObjectId -RequiredResourceAccess $Graph
User.read (delPermission2) work, but User.Read.All (delPermission1) don't, and I don't understand why.
I tried multiple permission, but just User.read worked, here are the id and value:
741f803b-c850-494e-b5df-cde7c675a1ca User.ReadWrite.All
83cded22-8297-4ff6-a7fa-e97e9545a259 Presence.ReadWrite.All
810c84a8-4a9e-49e6-bf7d-12d183f40d01 Mail.Read
CodePudding user response:
As far as I know, the ID's you are using for User.Read.All, User.ReadWrite.All, Presence.ReadWrite.All and Mail.Read permissions are incorrect.
To find the correct ID's of those delegated permissions, make use of below cmdlet:
$svcGraph.Oauth2Permissions | FT ID, Value, UserConsentDisplayName
From that, note down the correct ID's of all those permissions:
User.Read.All - a154be20-db9c-4678-8ab7-66f6cc099a59
User.ReadWrite.All - 204e0828-b5ca-4ad8-b9f3-f32a958e7cc4
Presence.Read.All - 9c7a330d-35b3-4aa1-963d-cb2b9f927841
Presence.ReadWrite - 8d3c54a7-cf58-4773-bf81-c0cd6ad522bb
Mail.Read - 570282fd-fa5c-430d-a7fd-fc8dc98a9dca
The ID that you are using for User.Read is correct. That's why it worked.
User.Read - e1fe6dd8-ba31-4d61-89e7-88639da4683d
Make sure you have the role of Administrator and use the correct ID's by modifying the values.
For more reference, please find below reference if it is helpful.
