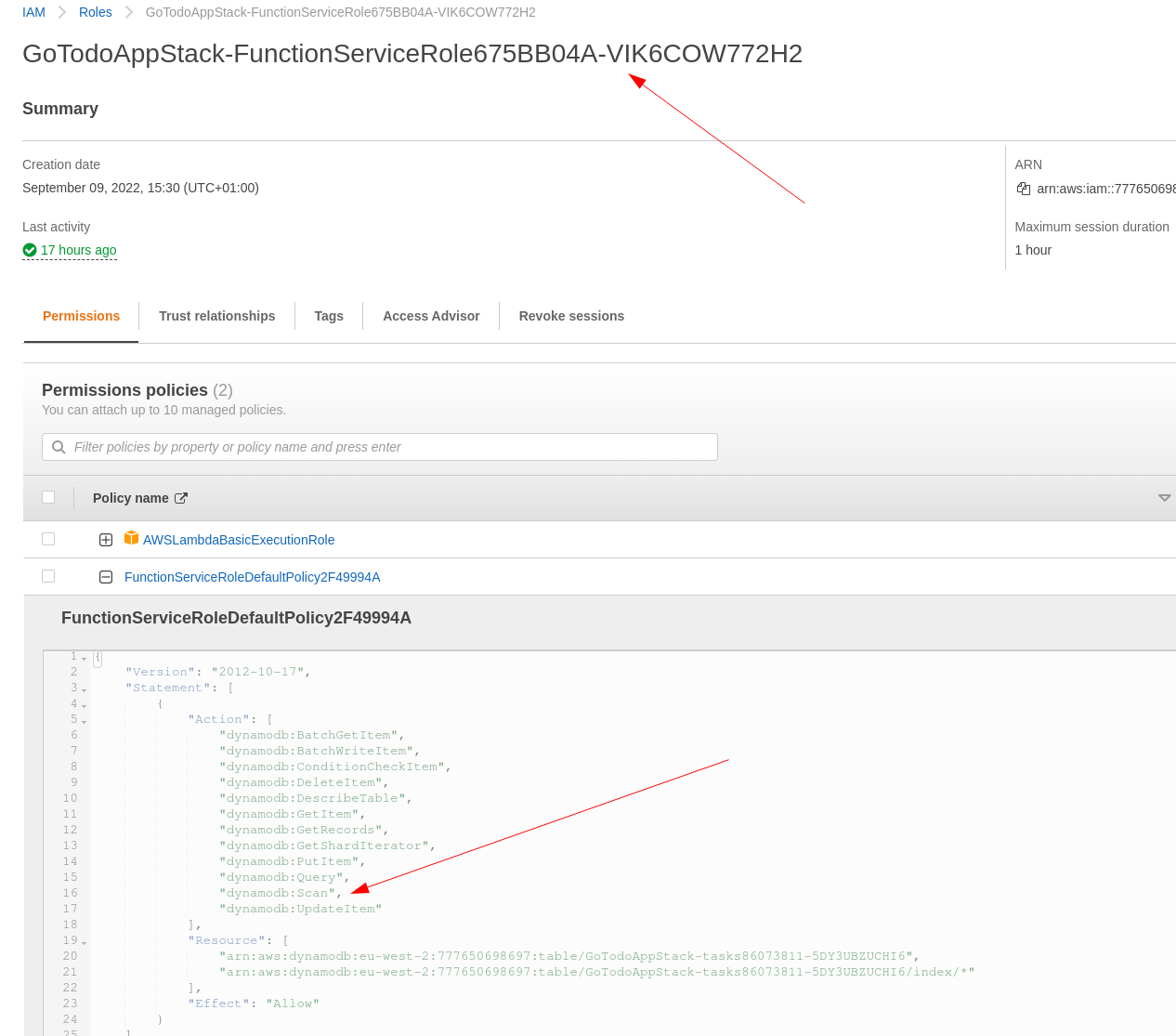
My whole solution (infrastructure code and the actual lambda) are all 
When I check the CloudWatch logs, I can see an error, and the error message says that my lambda does not have permissions to do a Scan on my DynamoDB table! At least that's my understanding of the error message:
2022/09/11 15:32:30 could not scan the dyanmodb table! error: operation error DynamoDB: Scan, https response error StatusCode: 400, RequestID: 8JTBR7LIJ6H6UERR0NSM1U28EBVV4KQNSO5AEMVJF66Q9ASUAAJG, api error AccessDeniedException: User: arn:aws:sts::777650698697:assumed-role/GoTodoAppStack-FunctionServiceRole675BB04A-VIK6COW772H2/GoTodoAppStack-Function76856677-333lC1zqdKCi is not authorized to perform: dynamodb:Scan on resource: arn:aws:dynamodb:us-west-2:777650698697:table/GoTodoAppStack-tasks86073811-5DY3UBZUCHI6 because no identity-based policy allows the dynamodb:Scan action
If you take a close look at the 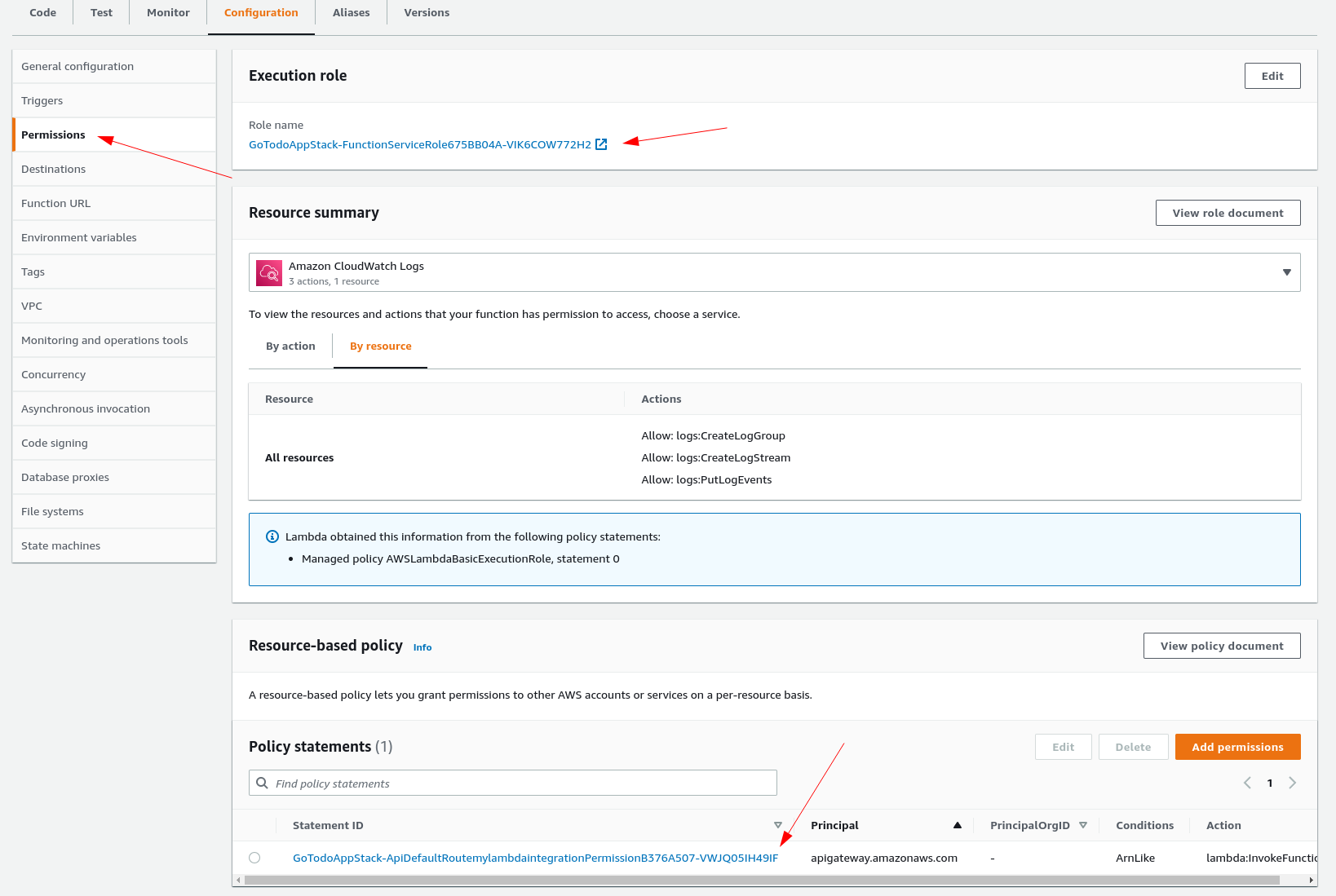
If I then click the link to the Execution Role associated with the Lambda, I get:
As you can see, it has the right permissions!
CodePudding user response:
The AWS region is different on the error log you provided and on the IAM role. The region on the error is us-west-2 but the region on the role permissions is eu-west-2.
It seems that you hardcoded the region on your lambda handler in /main/api/getitems/handler.go line 31.
CodePudding user response:
Try adding this policy to your lambda role (this is typescript):
handler.addToRolePolicy(new PolicyStatement({ resources: [table.tableArn], actions: ['dynamodb:Scan'] }));
or
table.grant(handler, ['dynamodb:Scan']);