I have an AKS kubernetes cluster provisioned with terraform. And I need to enable the azure-keyvault-secrets-provider add-on.
Using the azure CLI, I could enable it as follows:
az aks enable-addons --addons azure-keyvault-secrets-provider --name myAKSCluster --resource-group myResourceGroup
But, how can I do it with the terraform? I tried the documentation, but doesn't mention anything about a secret driver except only one block as follows:
resource "azurerm_kubernetes_cluster" "k8s_cluster" {
lifecycle {
ignore_changes = [
default_node_pool
]
prevent_destroy = false
}
key_vault_secrets_provider {
secret_rotation_enabled = true
}
...
}
Is the above key_vault_secrets_provider doing the same thing as the azure CLI command az aks enable-addons --addons azure-keyvault-secrets-provider --name myAKSCluster --resource-group myResourceGroup ?
Because according to the terraform documentation, this key_vault_secrets_provider block is only for rotating the keyvault secrets. But no mention about enabling the driver.
My requirement is to:
- Enable the secret provider driver
- Create a kubernetes Secret -> so it will provision the secret in azure
- Inject the secret to a kubernetes Deployment
CodePudding user response:
I have tried to check the same in my environment:
Code: Without key_vault_secrets_provider
main.tf:
resource "azurerm_kubernetes_cluster" "example" {
name = "kavyaexample-aks1"
location = data.azurerm_resource_group.example.location
resource_group_name = data.azurerm_resource_group.example.name
dns_prefix = "kavyaexampleaks1"
default_node_pool {
name = "default"
node_count = 1
vm_size = "Standard_D2_v2"
}
identity {
type = "SystemAssigned"
}
tags = {
Environment = "Production"
}
}
output "client_certificate" {
value = azurerm_kubernetes_cluster.example.kube_config.0.client_certificate
sensitive = true
}
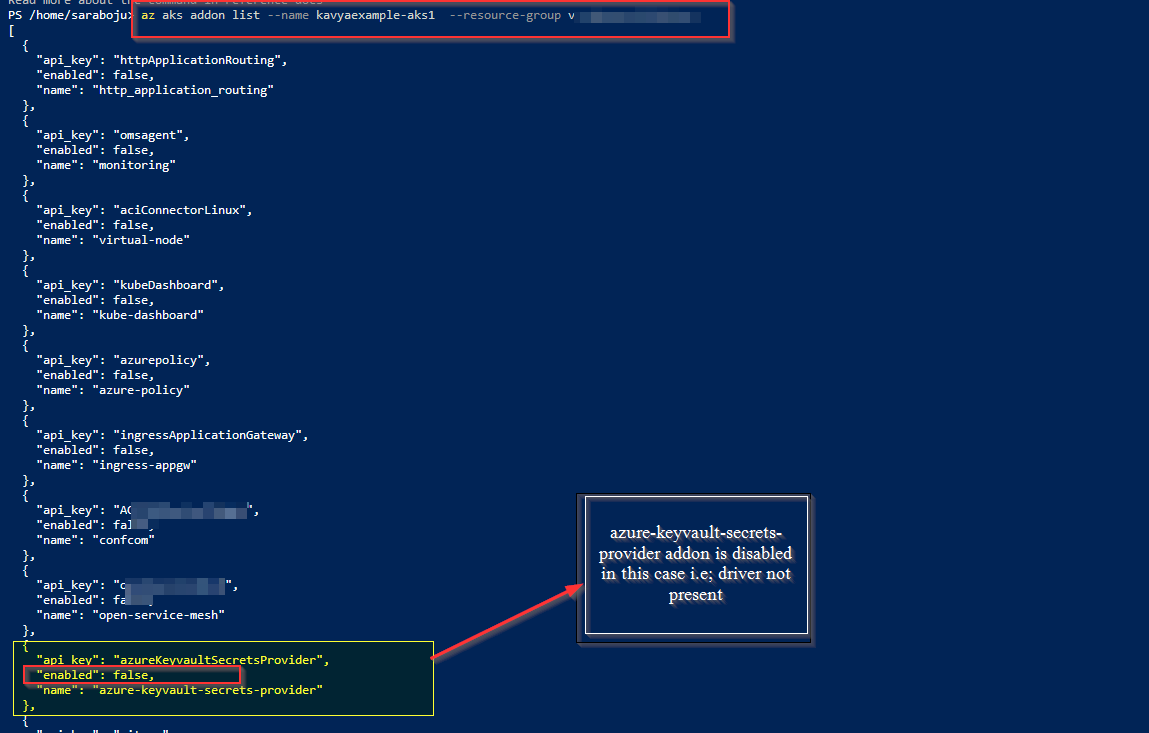
- When checked the available
Now checked after adding key_vault_secrets_provider block with secret rotation enabled. Main.tf:
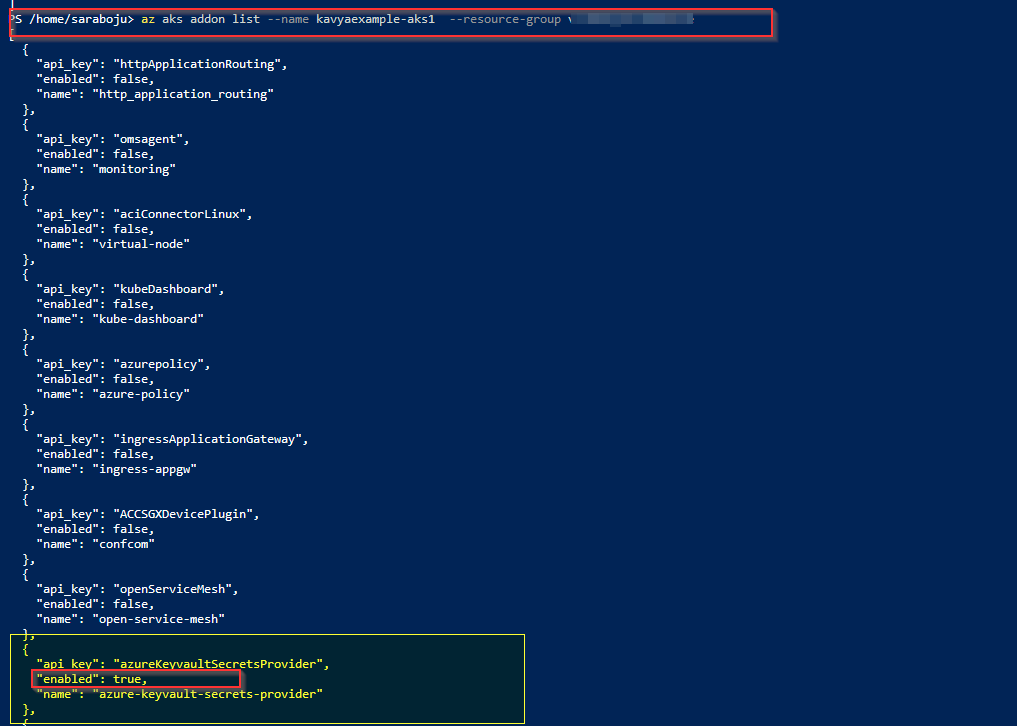
resource "azurerm_kubernetes_cluster" "example" { name = "kavyaexample-aks1" location = data.azurerm_resource_group.example.location resource_group_name = data.azurerm_resource_group.example.name dns_prefix = "cffggf" .... key_vault_secrets_provider { secret_rotation_enabled = true } default_node_pool { name = ”dfgdf” ... }When checked for addon list using the same command:
az aks addon list –name kavyaexample-aks1 --resource-group <myrg>The azure keyvault secret provider addon is being enabled.
which means adding key_vault_secrets_provider block with secret rotation enabled itself means , we are making use of the azure keyvault secret provider addon.
Also check this terraform-azurerm-aks issue on addon_profile being deprecated in latest terraform versions |github