I have the following subnets
- Subnet_1 = 10.2.3.0
- Subnet_1 = 10.2.4.0
I want to prevent subnet to subnet communication. As far as I see, it can be done using the Network Security Group. However I am not sure about the required change.
CodePudding user response:
I tried to reproduce the same in my environment to prevent communication between 2 Subnet
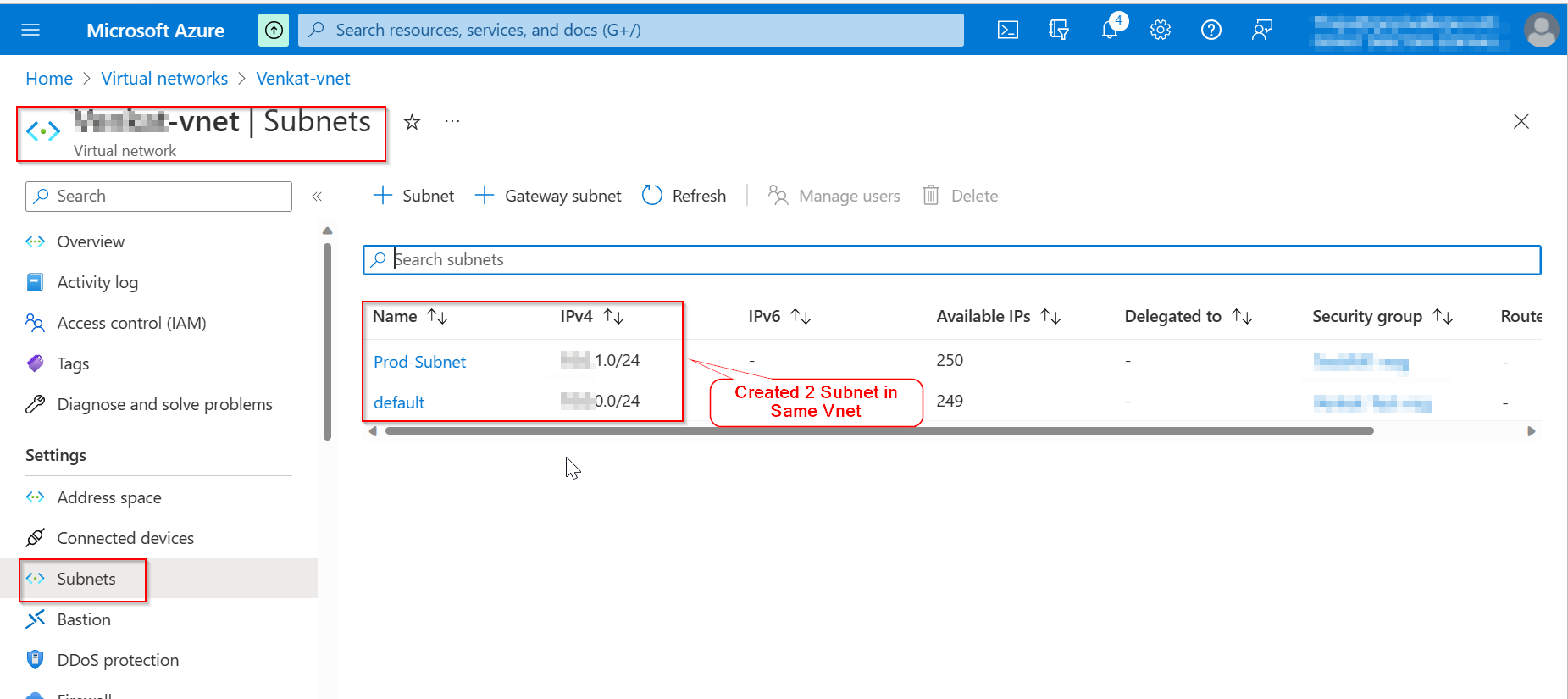
I have created 2 subnets in my Vnet, like below.
Subnet 1: Prod-Subnet (10.0.1.0/24)
Subnet 2: default (10.0.0.0/24)
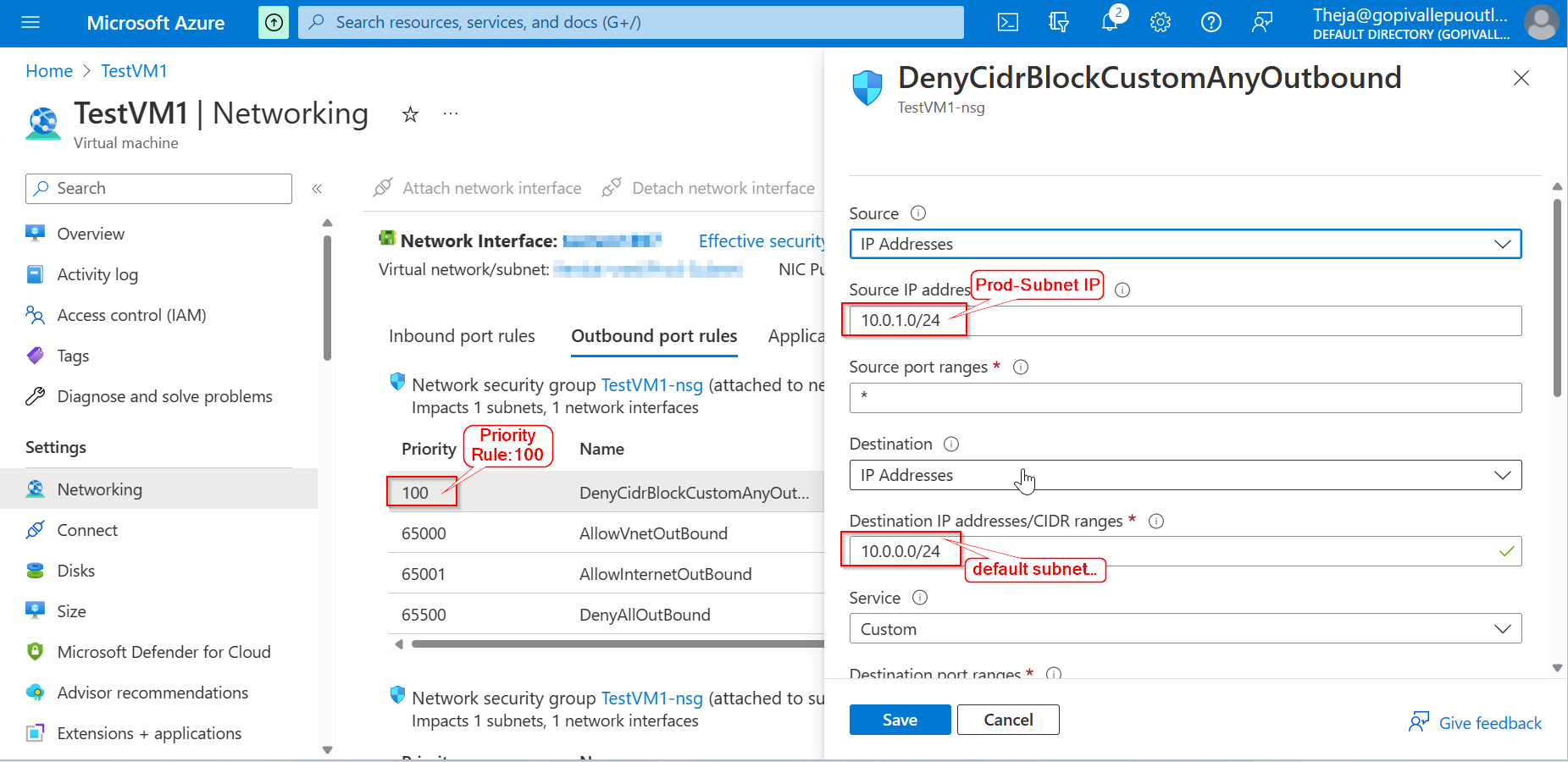
In order to prevent communication between both the VNet, you need to create an inbound and outbound rule in same NSG group, like below.
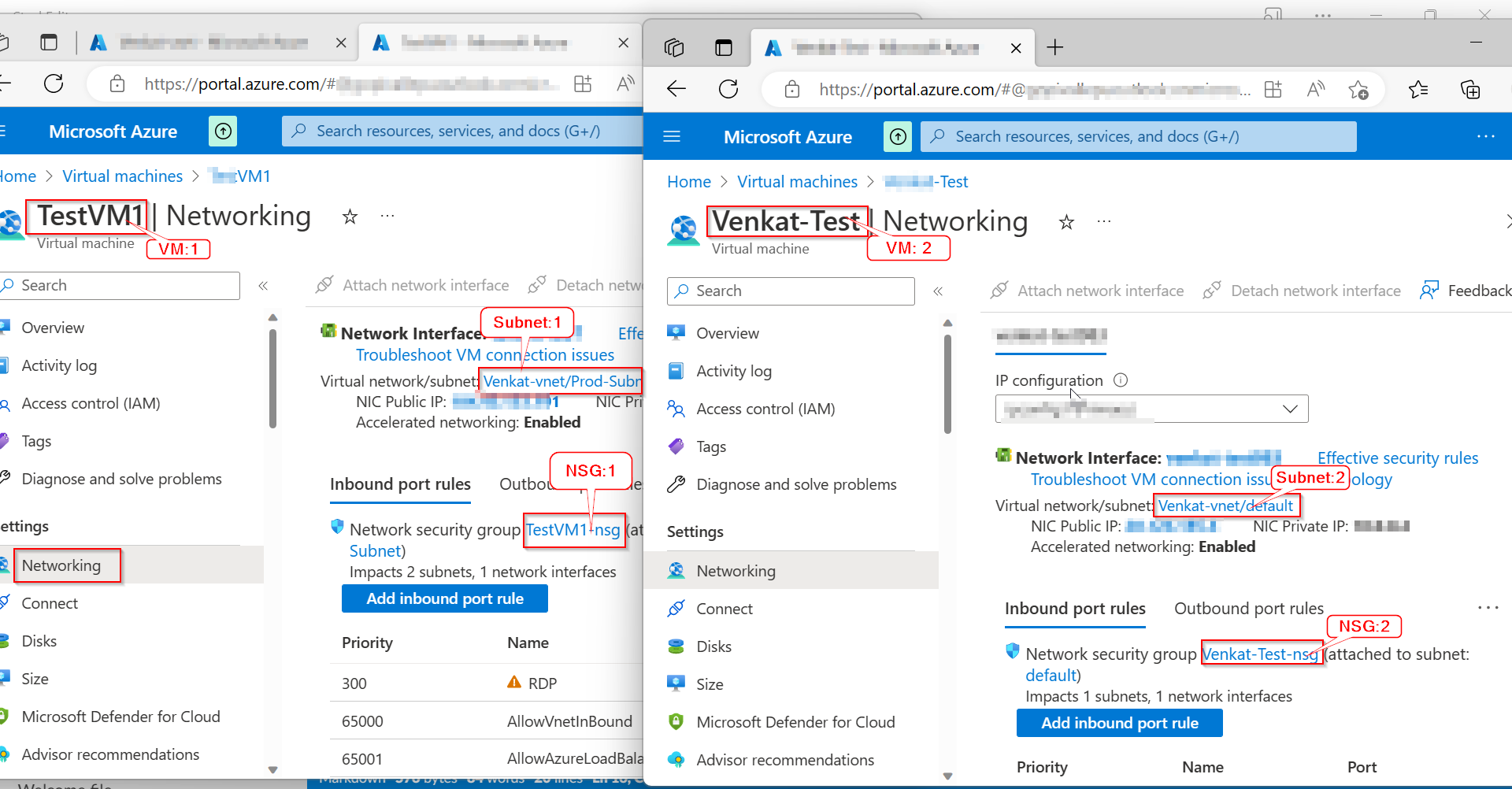
I have created 2 virtual machines and attached above subnets to 2 virtual machines, like below.
Prod-subnet attached to VM1 Default Subnet attached to VM2
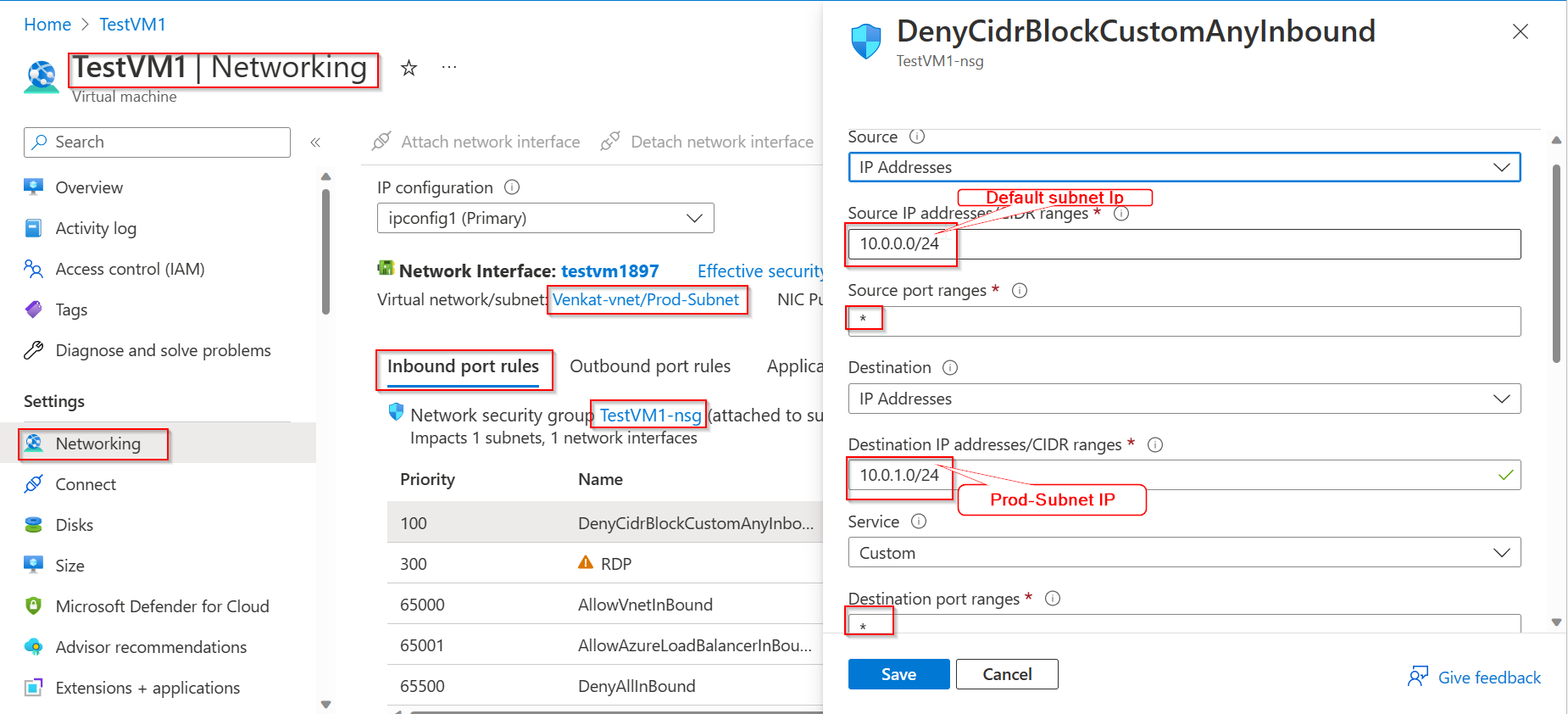
Create inbound and outbound rule in Network Security Group to block the communicatioin ,like below.
Inbound Rule:
Source IP: 10.0.0.9/24
Source Port: * ( for all)
Destination IP: 10.0.1.0/24
Destination Port: *( for all)
Service: custom
(Note: If you want block particular service and port, mention the port details and protocol type)
Outbound Rule:
Source IP: 10.0.1.0/24
Source Port: * ( for all)
Destination IP: 10.0.0.0/24
Destination Port: *( for all)
Service: custom
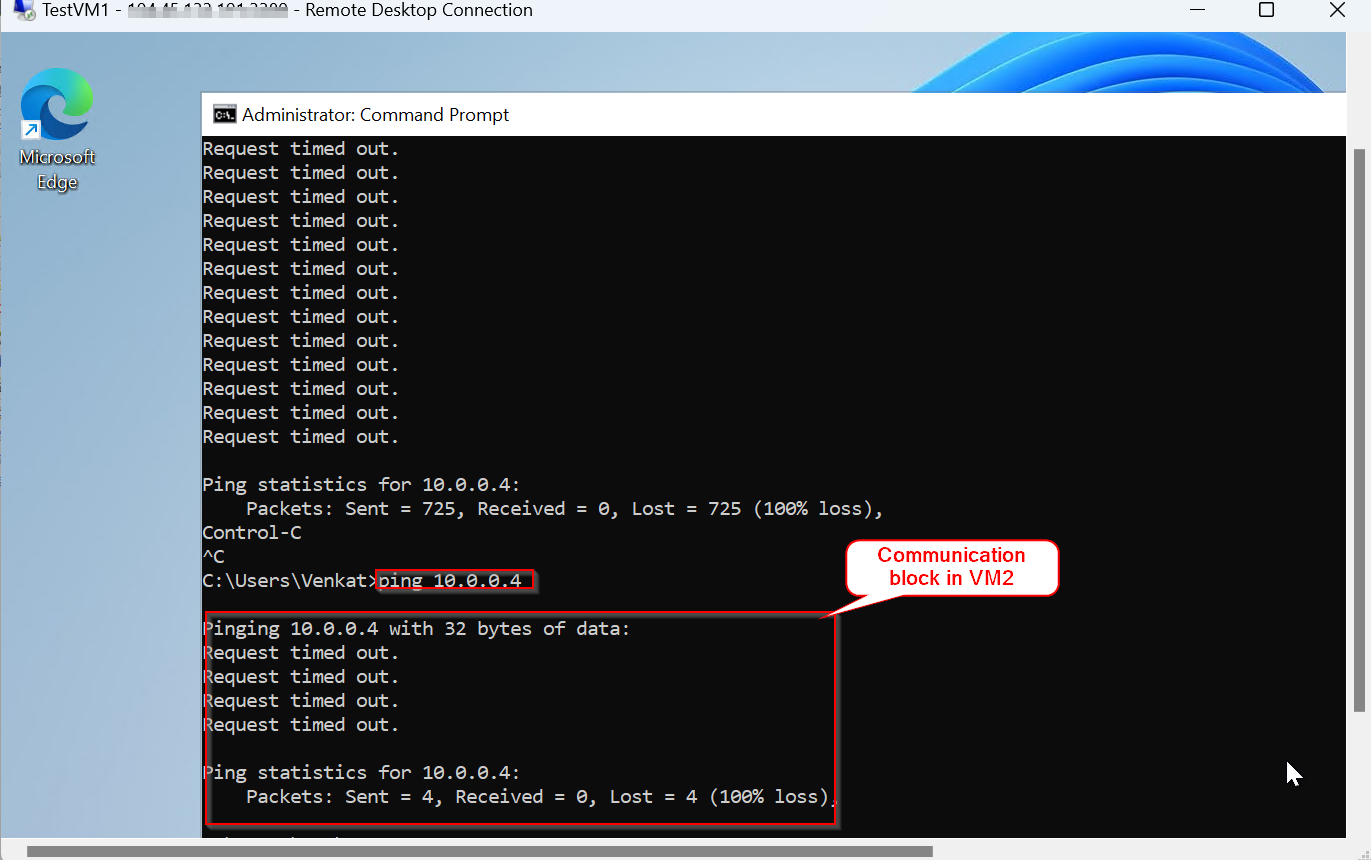
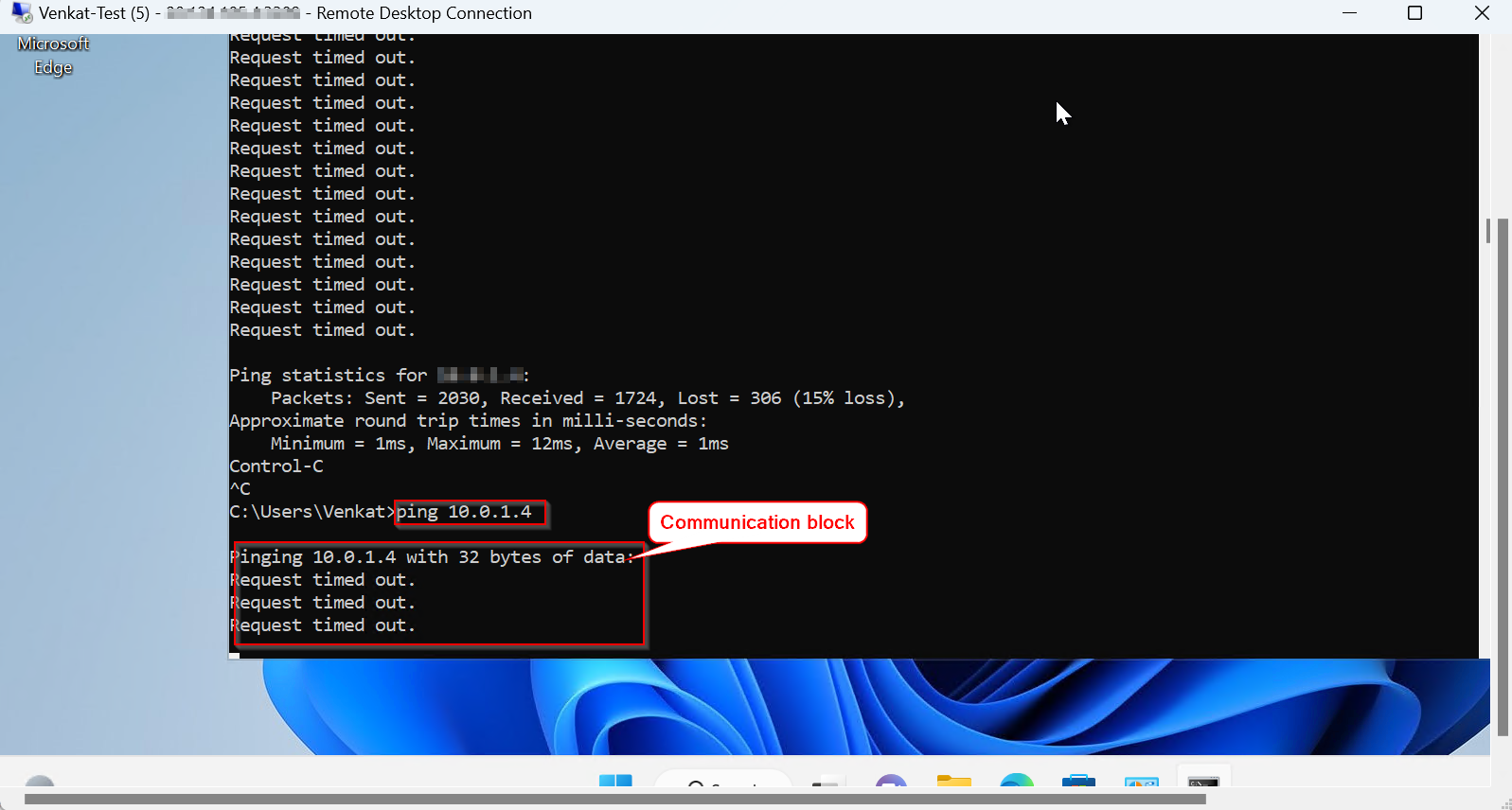
Tested communication and its getting denied from the subnets.
VM 1 Result
VM 2 Result