I have an automated script which reads the azure App Reg secrets expiry and creates a new secret based on the counter days. In the same PowerShell file from the pipeline, I am trying to add the new secret generated from the script to respective key vault.
I am able to create and add the secret to KV locally using PowerShell ISE with the same SP authentication.
From the Devops pipeline, I am able to create the client secret but when trying to add the new client secret to key vault secret, I am getting below error:
##[error]Operation returned an invalid status code 'Forbidden' Code: Forbidden Message: Client address is not authorized and caller is not a trusted service. Client address: 12.34.56.189 Caller: appid=xxx;oid=abcded-8855-3rfg-56gt-fdvtr;iss=https://sts.windows.net/abcded-8855-3rfg-56gt-fdvtr/ Vault: test-kv;location=eastus2
I am using below command to add the client secret to the KV.
Set-AzKeyVaultSecret -VaultName $VaultName -Name $SecretName -SecretValue $newpass
I am using a Service principal to authenticate/login to Azure AD and the same SP has Application administration permissions. The SP has almost all the permissions to the key vault as well.
CodePudding user response:
From your error message, it indicates the DevOps agent client is not using the trusted IP.
##[error]Operation returned an invalid status code 'Forbidden' Code: Forbidden Message: Client address is not authorized and caller is not a trusted service. Client address: 12.34.56.189 Caller: appid=xxx;oid=abcded-8855-3rfg-56gt-fdvtr;iss=https://sts.windows.net/abcded-8855-3rfg-56gt-fdvtr/ Vault: test-kv;location=eastus2
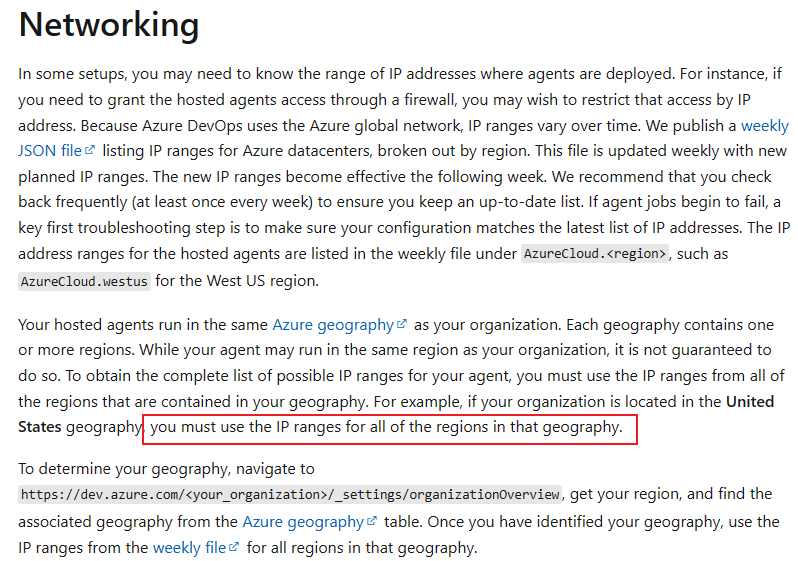
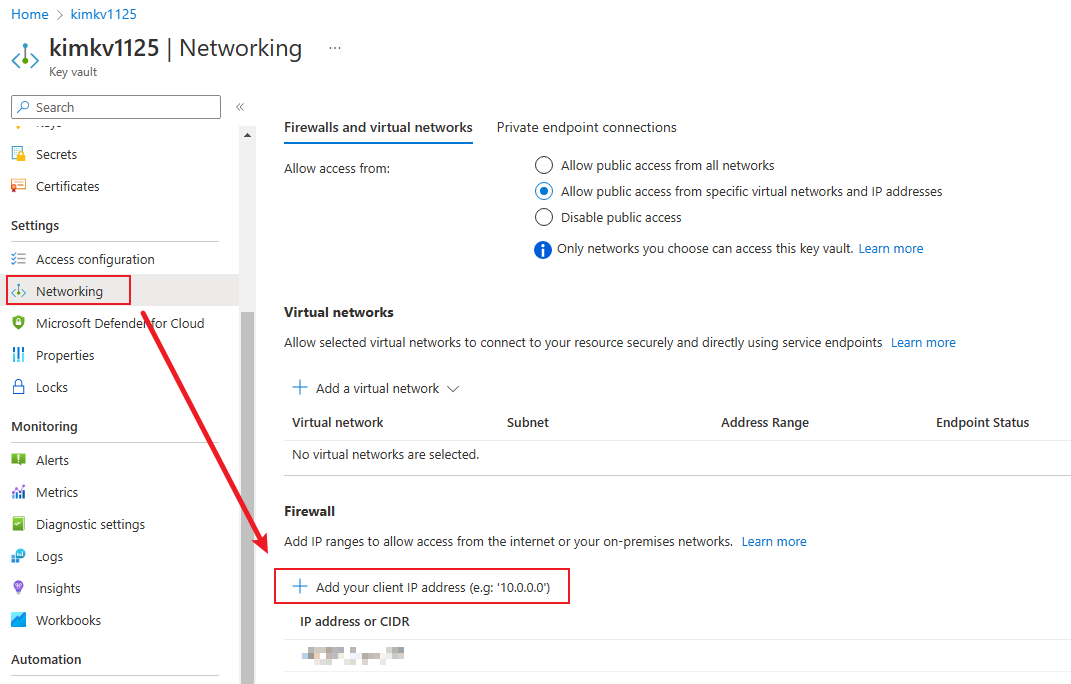
Please check your Azure Key Vault Networking Setting:
If you are using Self-hosted agent, make sure you have added the IP of your Self-hosted agent into Key Vault Firewall whitelist.
If you are using Microsoft-hosted agent, you could follow this official