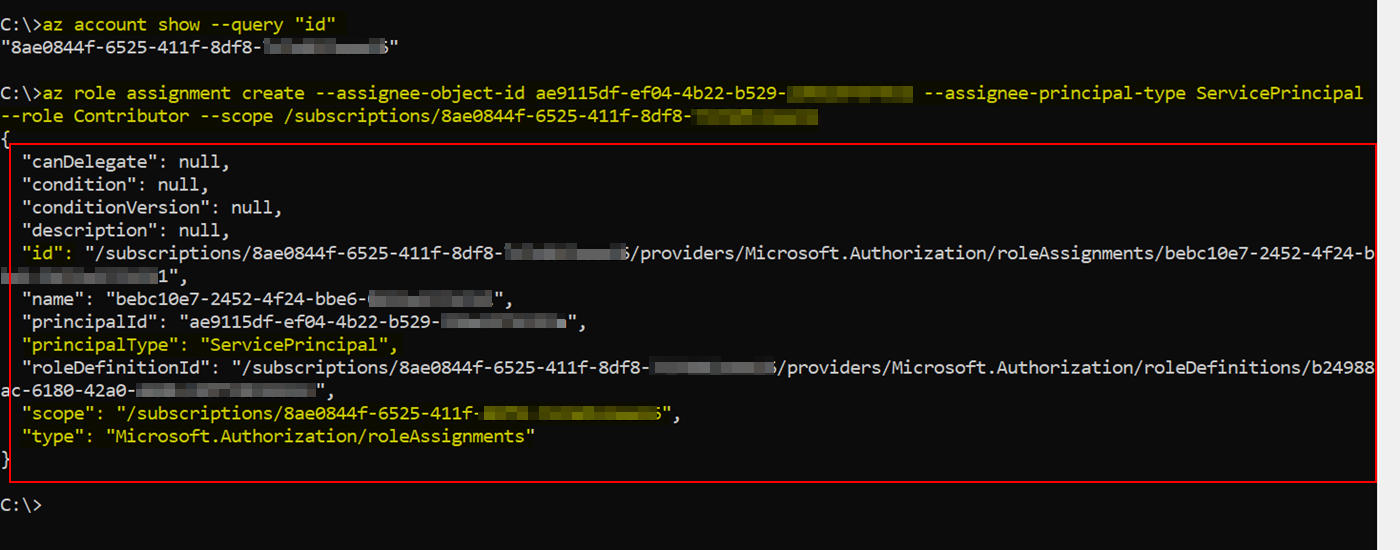
I try to grant permission for create resource group to service principal in my UWP C# project. I use Azure SDK for .NET to create confidential application registration and acquire access token. It is worked with my extension methods, to prevent platform check. But when I try to get role assignments for service principal, I receive Azure.RequestFailedException 0x80131500, "The subscription 'xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx' could not be found".
ResourceIdentifier scope = new ResourceIdentifier($"/subscriptions/{MyTenantId}");
ConfidentialClientCredential credential = new ConfidentialClientCredential(MyConfidentialClientApplication);
ArmClient armClient = new ArmClient(credential);
RoleAssignmentCollection roleAssignmentCollection = AuthorizationExtensions.GetRoleAssignments(armClient, scope);
IEnumerable<RoleAssignmentResource> roleAssignments = roleAssignmentCollection?.GetAll($"$filter=atScope() and assignedTo('{strServicePrincipalId}')");
if(roleAssignments != null)
{
AuthorizationRoleDefinitionResource roleDefinition = null;
foreach(RoleAssignmentResource curRoleAssignment in roleAssignments) // <-- exception throws there
{
if(curRoleAssignment?.HasData == true && !string.IsNullOrWhiteSpace(curRoleAssignment.Data.RoleDefinitionId?.Name))
{
roleDefinition = await AuthorizationExtensions.GetAuthorizationRoleDefinitionAsync(armClient, scope, curRoleAssignment.Data.RoleDefinitionId);
}
}
}
I'm using my tenant ID here as my subscription ID because it was returned by the Azure CLI command:
az account show --query "id"
I guess that AAD RBAC can be used for this purpose, but I haven't found suitable AD permission.
Is there any way to grant permission for create resource group in my case?
CodePudding user response:
Note that, subscription ID is different from tenant ID. If you don't have subscription, you can neither create resource group nor assign RBAC role to service principal.
If there are no subscriptions, you will get tenant ID in response when you run az account show --query "id" command.
I tried to reproduce the same in my environment via CLI and got below results:
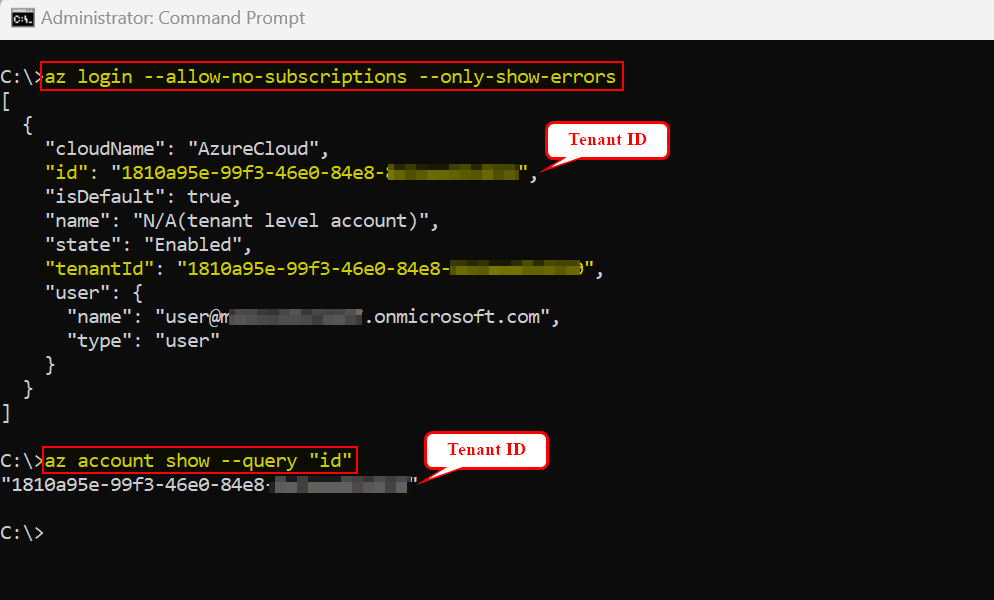
When I ran below commands, I got tenant ID in my response as I don't have subscriptions like below:
az login --allow-no-subscriptions --only-show-errors
az account show --query "id"
Response:
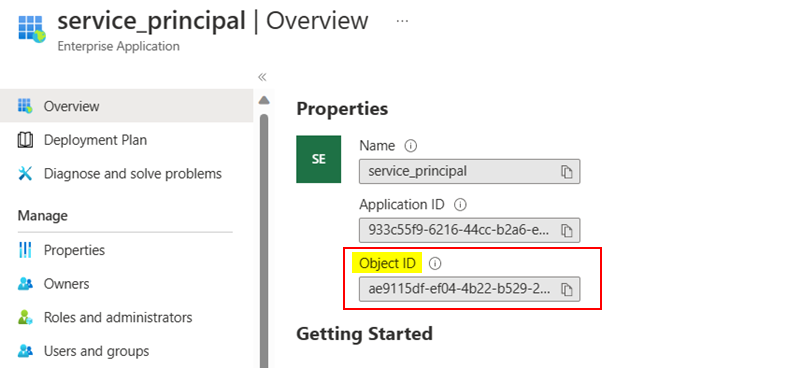
I have one service principal in my tenant like below:
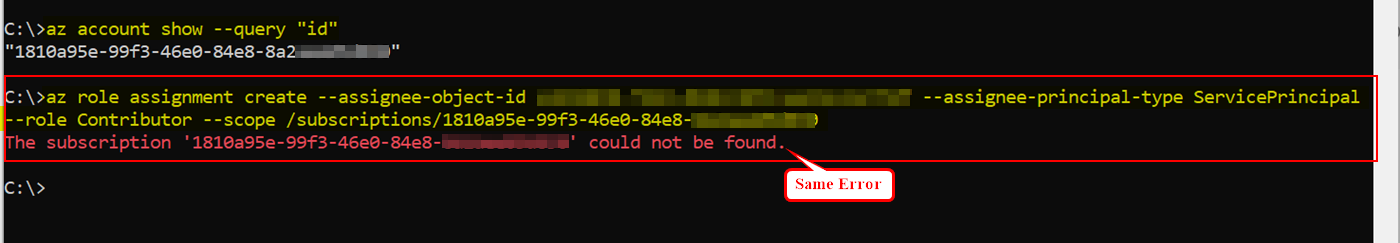
When I tried to assign role to the above service principal using below CLI command by giving tenantID as subscriptionID, I got same error as you like this:
az role assignment create --assignee-object-id <sp_objectID> --assignee-principal-type ServicePrincipal --role Contributor --scope /subscriptions/<tenant ID>
Response:
Without subscription, you can only perform directory-level operations like managing Azure AD users, groups, app registration etc...
You definitely need subscription to manage Azure resources like resource groups, virtual machines, storage accounts, role assignments etc...
To resolve the error, make sure to have at least one subscription linked to your tenant and login again like below:
az login --allow-no-subscriptions --only-show-errors
az account show --query "id"
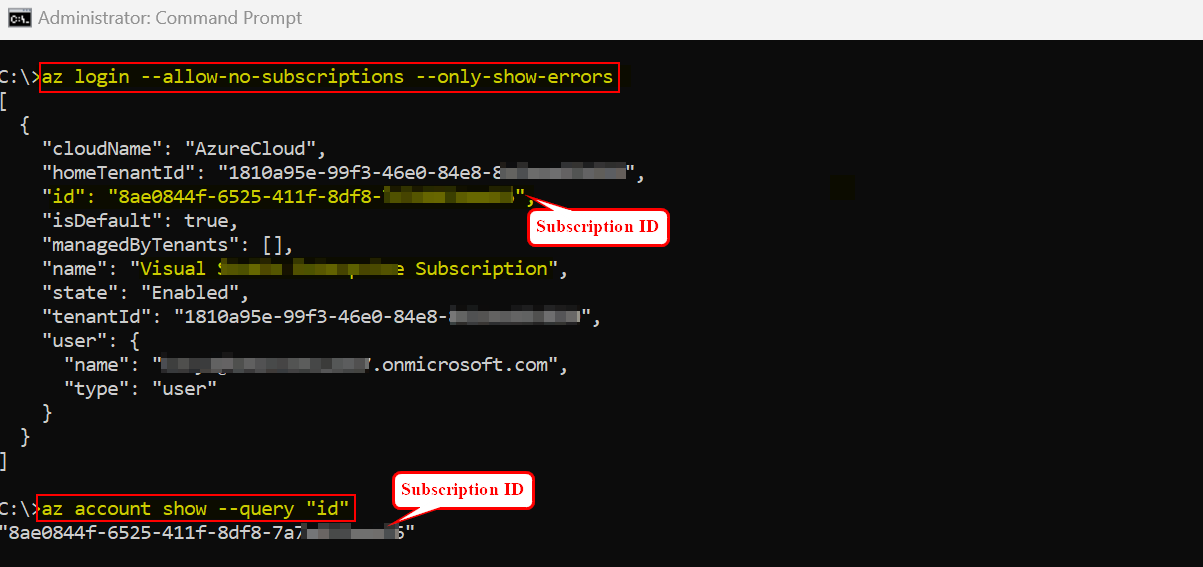
When I ran the below CLI command again by including above subscriptionID, role assignment created successfully like below:
az role assignment create --assignee-object-id <sp_objectID> --assignee-principal-type ServicePrincipal --role Contributor --scope /subscriptions/<subscription ID>
Response: