I'm trying to read and write over a newly created azure table, but I kept getting 403 errors. I'm using the same account that I used to create the table. I also added the account to the contributors group. I've tested multiple scopes thinking does might be the issue, such as:
- https://storage.azure.com/user_impersonation
- https://storage.azure.com/.default
- https://osnapdbexamsonthecloud.table.core.windows.net/.default
- https://osnapdbexamsonthecloud.table.core.windows.net/user_impersonation
but always got the same error
Here is the requeset I'm sending:
PUT https://osnapdbexamsonthecloud.table.core.windows.net/exams(PartitionKey='Osnap',RowKey='test')
Accept: application/json;odata=fullmetadata
Accept-Encoding: gzip, deflate, br
Accept-Language: en-US,en;q=0.5
authorization: Bearer CENSORED
Connection: keep-alive
Content-Length: 27
content-type: application/json
Host: osnapdbexamsonthecloud.table.core.windows.net
Origin: http://localhost:3000
Referer: http://localhost:3000/
Sec-Fetch-Dest: empty
Sec-Fetch-Mode: cors
Sec-Fetch-Site: cross-site
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/109.0
x-ms-version: 2019-02-02
{"id":"test","temp":"test"}
And this is the response I get with status code 403:
{"odata.error":{"code":"AuthorizationPermissionMismatch","message":{"lang":"en-US","value":"This request is not authorized to perform this operation using this permission.\nRequestId:b3310a10-b002-0026-5cf5-3364d8000000\nTime:2023-01-29T15:22:15.9056626Z"}}}
Do you have any idea what I'm doing wrong?
CodePudding user response:
I agree with @Gaurav Mantri, you need to assign Storage Table Data Contributor role to your Service Principal on that storage account.
I tried to reproduce the same in my environment and got the below results:
I have one storage account in which I created a table named exams like below:
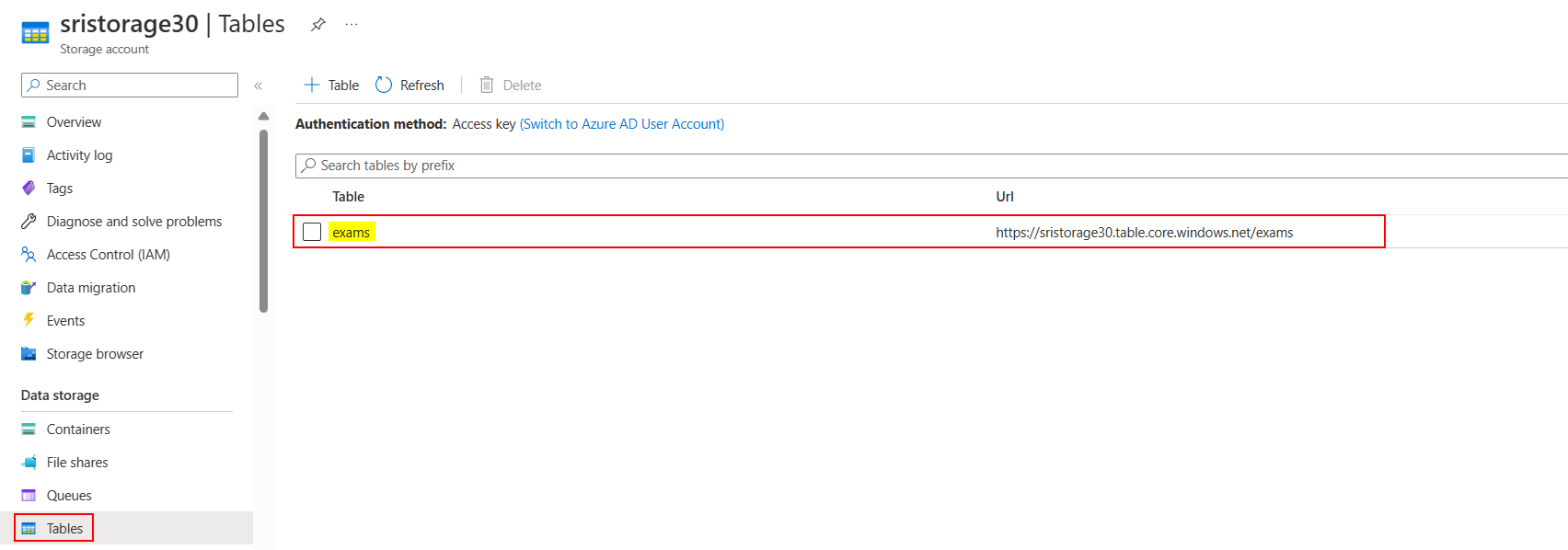
Now, I generated an access token via Postman with the below parameters:
POST https://login.microsoftonline.com/<tenantID>/oauth2/v2.0/token
client_id: <appID>
client_secret: <secret>
grant_type:client_credentials
scope: https://storage.azure.com/.default
Response:
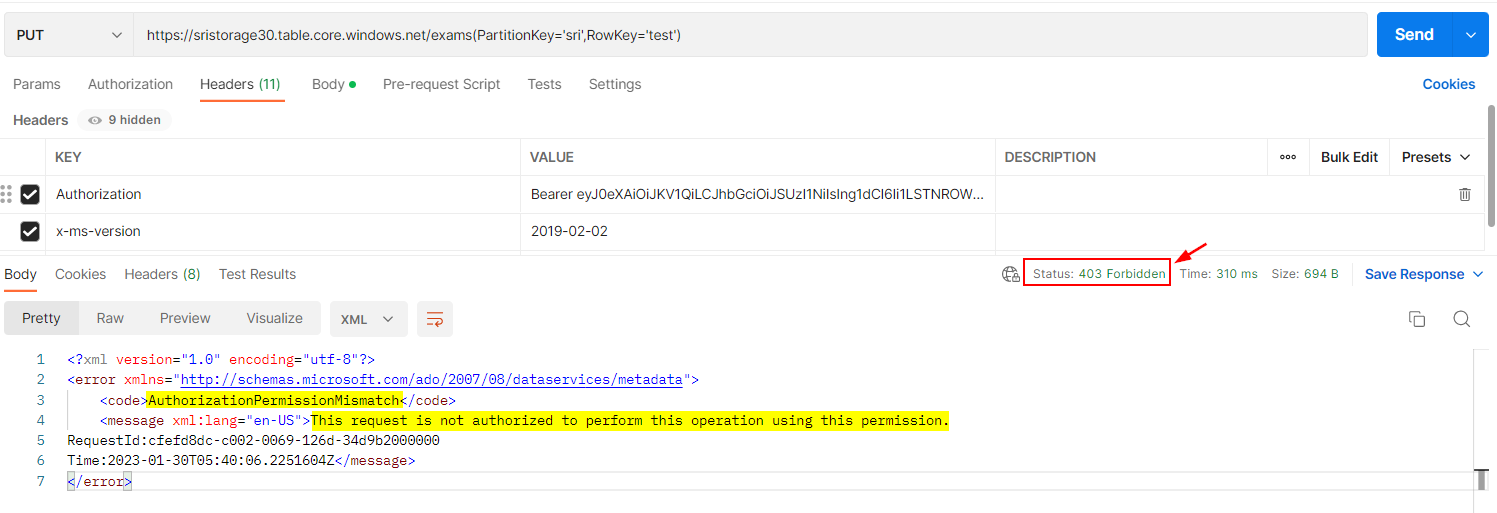
When I used the above token to perform the below operation, I got same error as you like this:
PUT https://sristorage30.table.core.windows.net/exams(PartitionKey='sri',RowKey='test')
Authorization: Bearer <token>
x-ms-version: 2019-02-02
{
"id":"test",
"temp":"test"
}
Response:
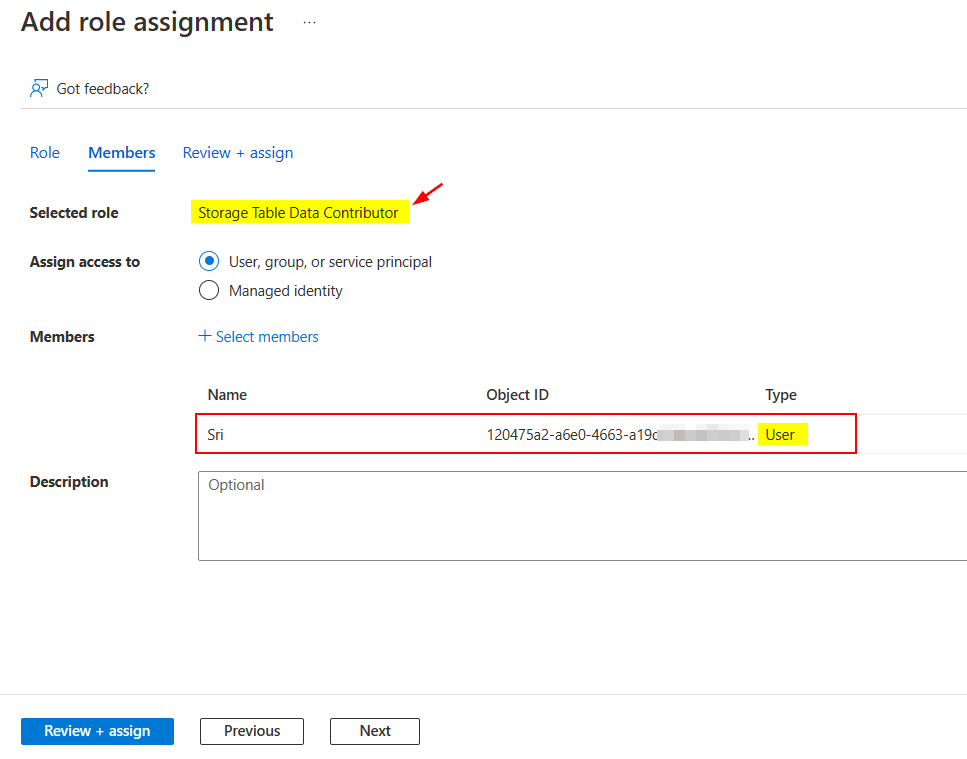
To resolve the error, try assigning Storage Table Data Contributor role to your service principal that can be your user account or Azure AD application.
In my case, I assigned that role to the service principal of App type like below:
Go to Azure Portal -> Storage accounts -> Your storage account -> Access control (IAM) -> Add role assignment
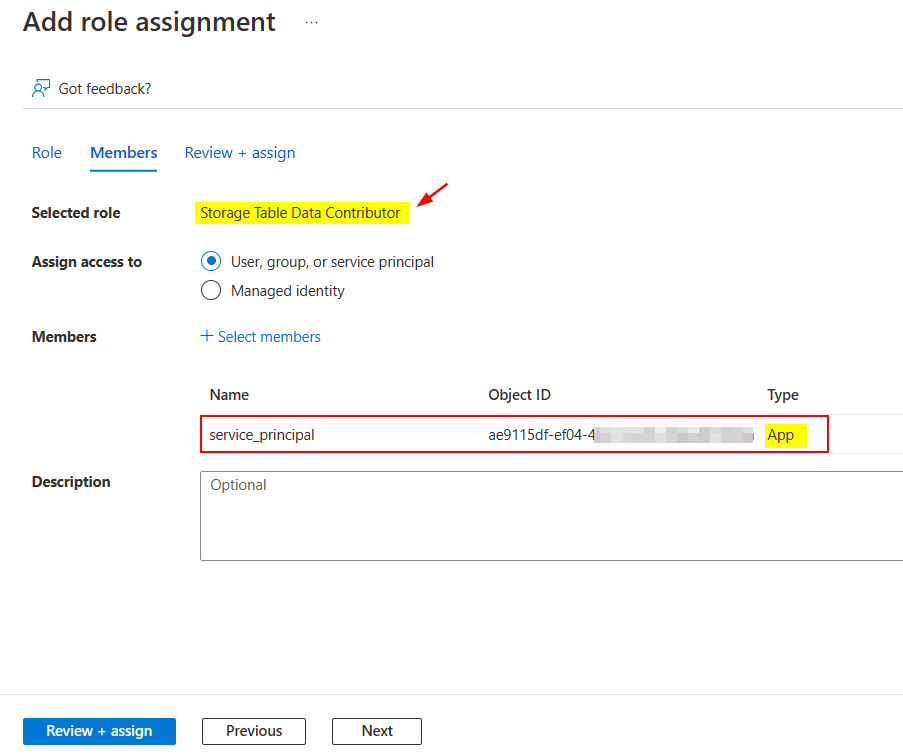
If you are performing the operation from your user account, assign that role to the service principal of User type like below: