I am trying to create a Client_secret for My service principal using the below code :
data "azuread_service_principal" "existing_SP" {
display_name = "TestAppRegistration"
}
resource "azuread_service_principal_password" "Client_Secret" {
service_principal_id = data.azuread_service_principal.existing_SP.object_id
}
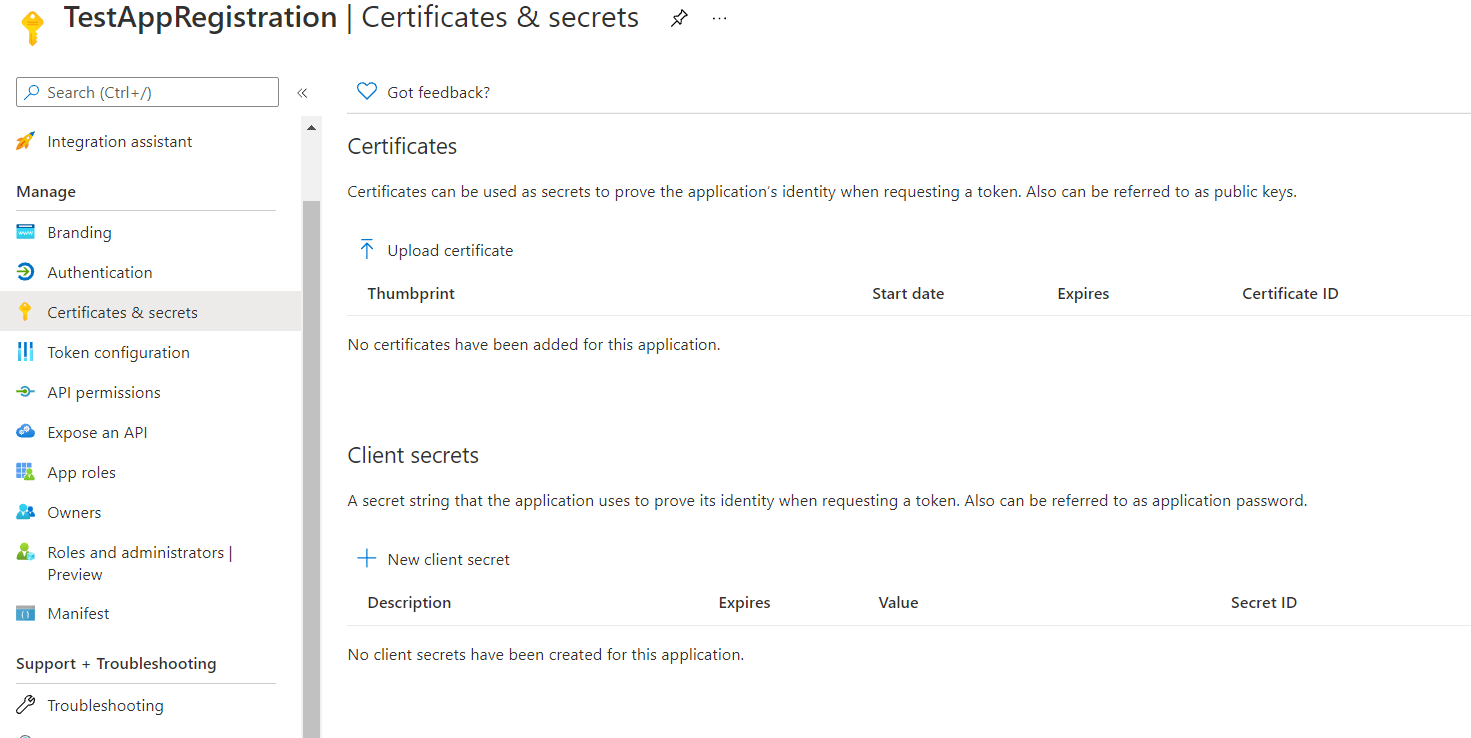
Doing a terraform-apply it get successfully created but I don't see it in the Secrets and certificates section of the app registration:
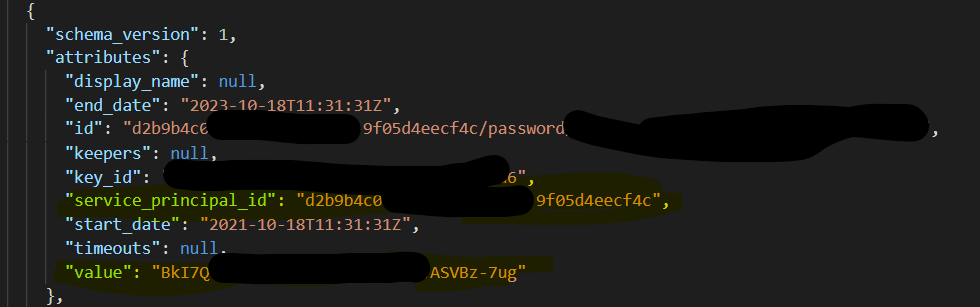
But when I check the tfstate , it shows the value there created for the service principal but the object Id is same as the enterprise application present for the same app registration:
So, My question:
- How can I create a client secret using terraform, is there something I am doing wrong ?
- If I am doing correct then where is the secret generated can be found in portal?
CodePudding user response:
How can I create a client secret using terraform, is there something I am doing wrong ?
Yes , You are doing everything correctly.
But to clear the confusion here , as you may already know there are 2 types of azure ad application i.e. app registrations and enterprise application. In terraform or powershell or cli the App Registration is know as Azure AD application and the Enterprise Application for the same app registration is know as Service Principal. So , if you have created from Portal by going to app registration blade , then bydefault a service principal is created for it , but its not the same if you create a app registration from Powershell or Terraform.
And By default you will be not be able to see the secret or certificate created for service principal from portal but you will be defintely able to use it with the client-id for authentication purpose .
For example :
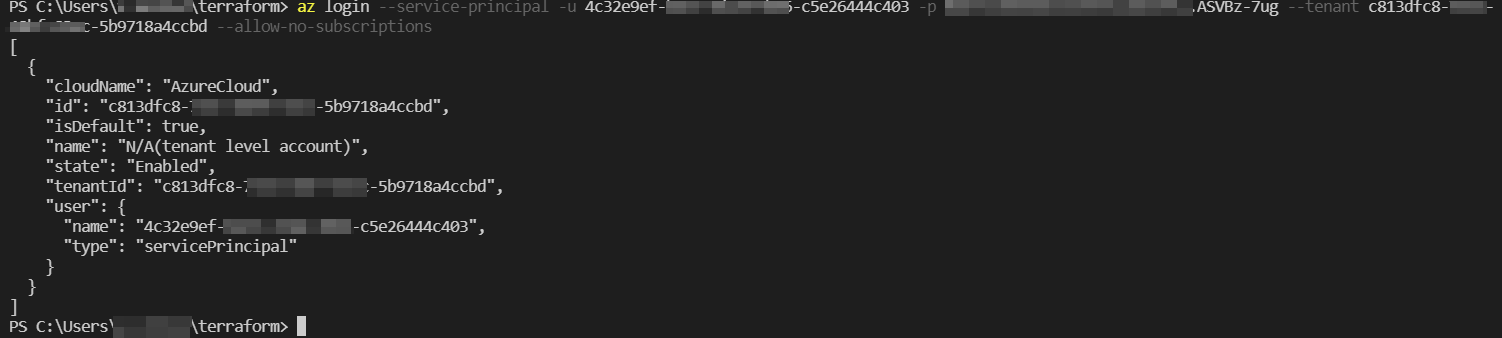
I tested this on my environment using your code and I took the value of password present in tfstate file and used it to do az login:
Note: Its safe to use terraform for creating a service principal password as it will be stored in the tfstate file so, you won't face difficulty in searching for it .
If I am doing correct then where is the secret generated can be found in portal?
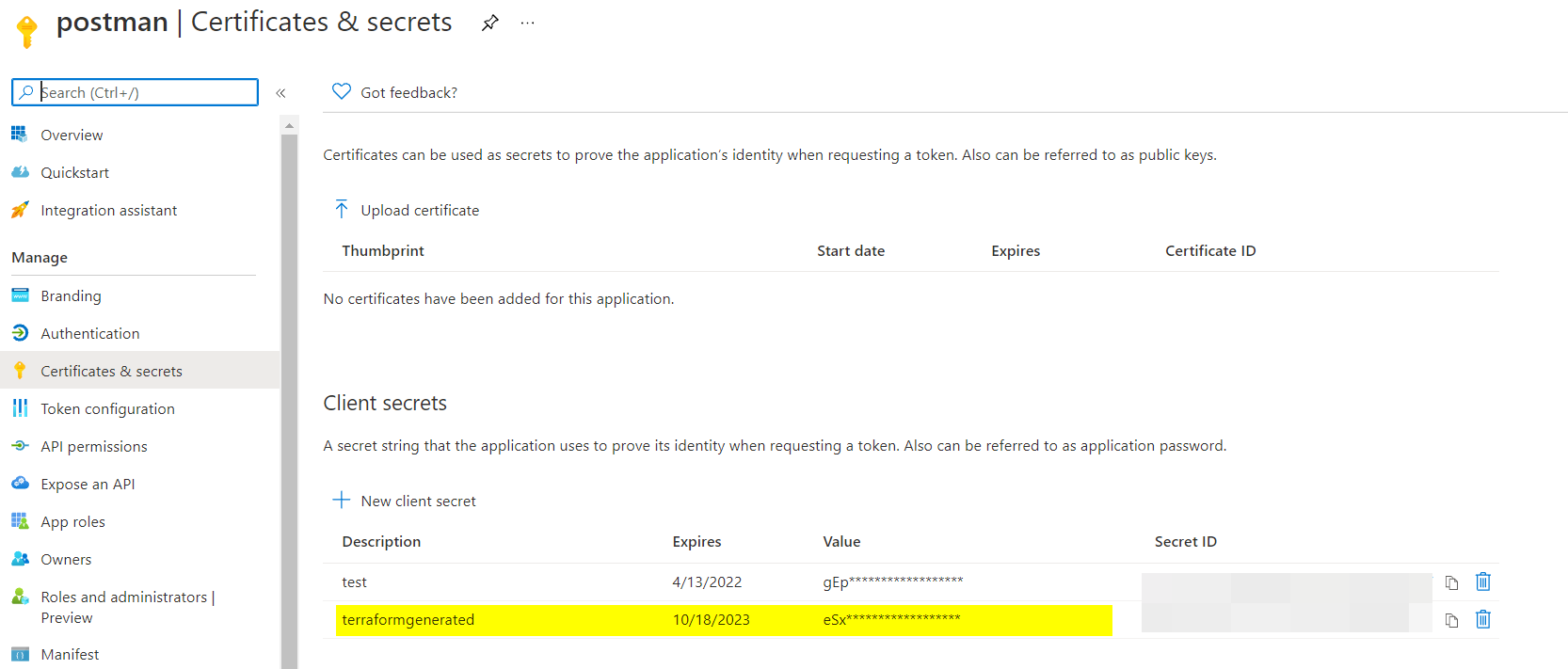
But if you are trying to look for the secret from portal , then I will suggest you to use azuread_application:
data "azuread_application" "example" {
display_name = "postman"
}
resource "azuread_application_password" "example" {
display_name = "terraformgenerated"
application_object_id = data.azuread_application.example.object_id
}