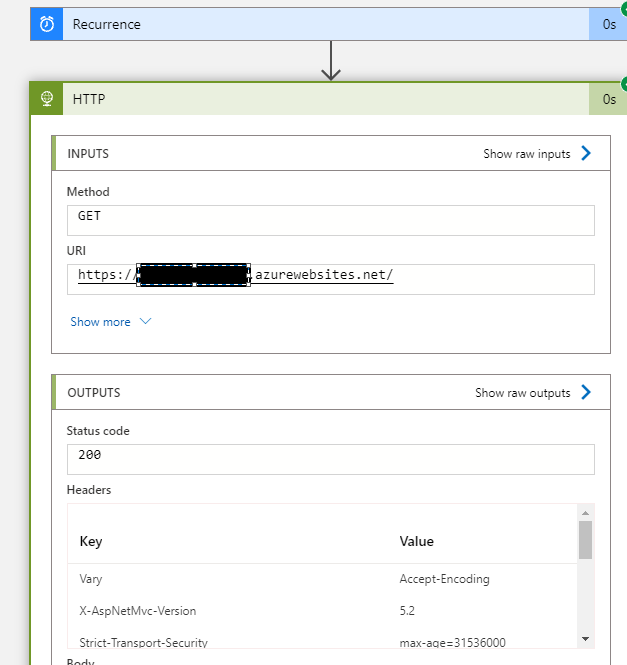
I want to access the endpoints that exists within my app that was uploaded to an App Service by calling them using a Logic App. I've enabled Authorization/Authentication but i cannot see to figure out how to correctly to create a valid autheticated request. I guess I'm missing something here, please look at the pictures below.
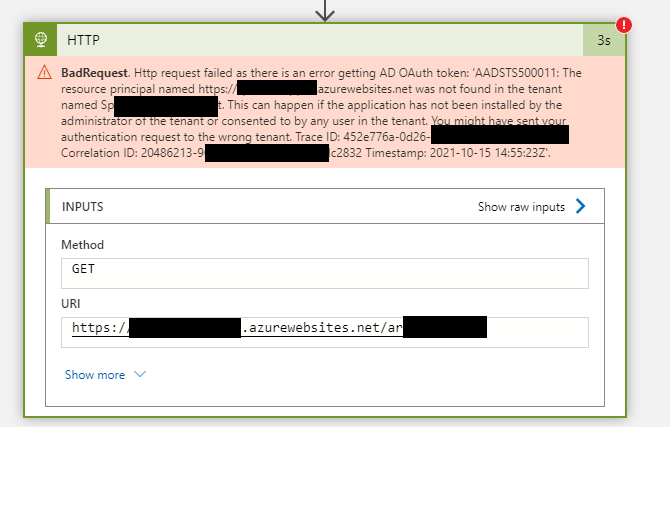
Im getting this error message: Http request failed as there is an error getting AD OAuth token: 'AADSTS500011: The resource principal named '' was not found in the tenant named ''. This can happen if the application has not been installed by the administrator of the tenant or consented to by any user in the tenant. You might have sent your authentication request to the wrong tenant.
Im sure the tenant id is correct and I've consented like a billion times i think :D. I provide all of the pictures that i can think of that could help finding out the issue here.
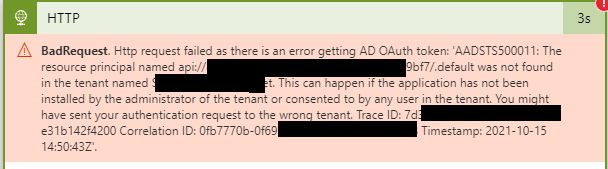
I also tried with another audience the api://...
Still no success:
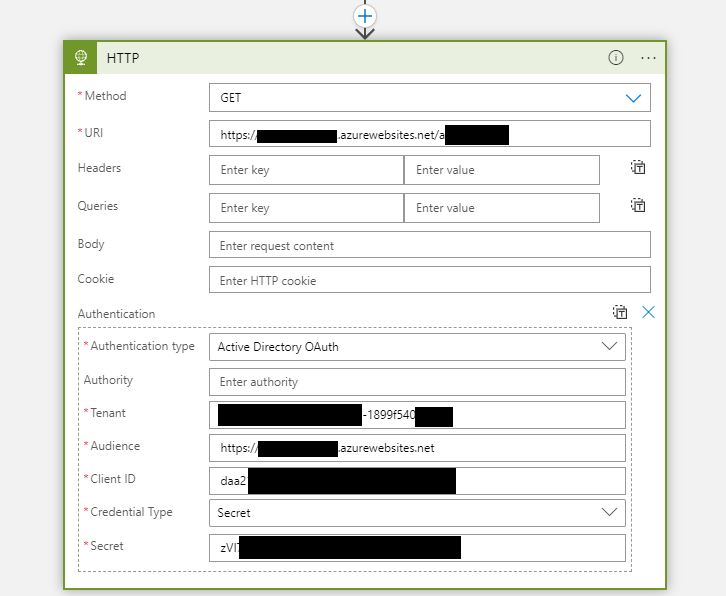
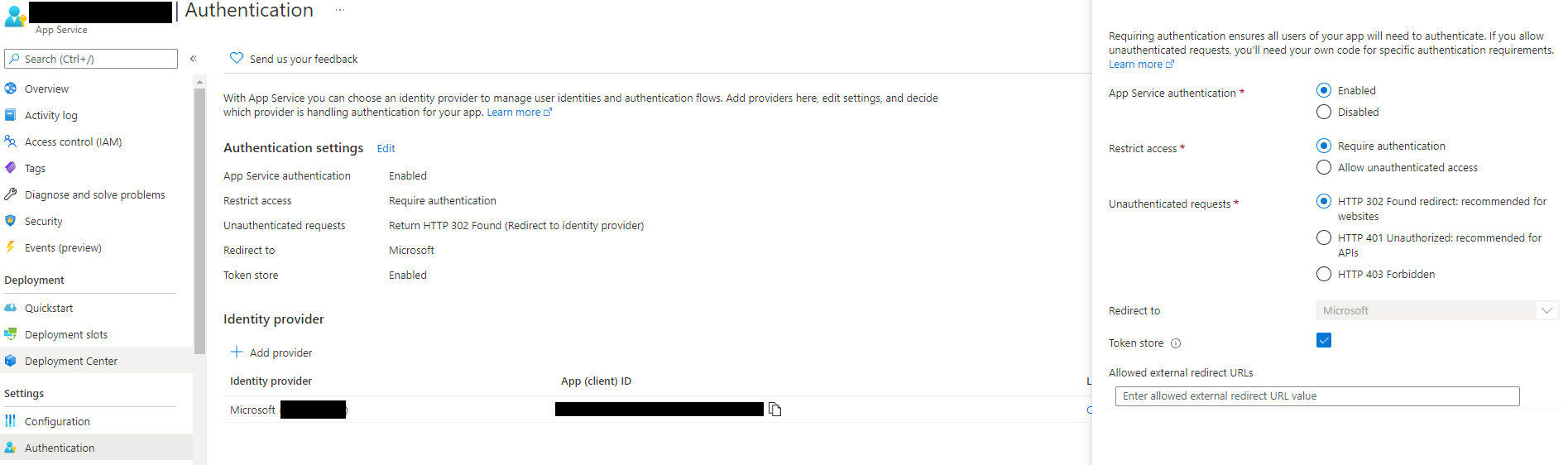
Here's my app service Auth section setup:
All I can think of is that i check the Allow unauthenticated access but that will leave me to code more in my app right? and I then need to restrict each individual endpoint. Instead id like to maybe have either a endpoint without the authorization or be able to send a authorized request through like a Logic App, Postman, doesnt matter in this case.
Any suggestions?
CodePudding user response:
There are two possible reason as per the error message, either the AD app is not present in the tenant or the AD tenant itself is not correct.
In either of the case you just need to check in AAD-->App registration-->Search with clientID (which you used above)
If not found then you either AAD is incorrect or you have not created AD app in this AAD.
Also check for application permissions .
Check following post for more insight
Result:
Works like a charm now :D
Research:
So i will also share how i figured out how to understand the error message and what was wrong. So my first complaint is the error message is missleading IMO, that the message said: ... getting AD OAuth token: 'AADSTS500011: The resource principal named '' was not ...
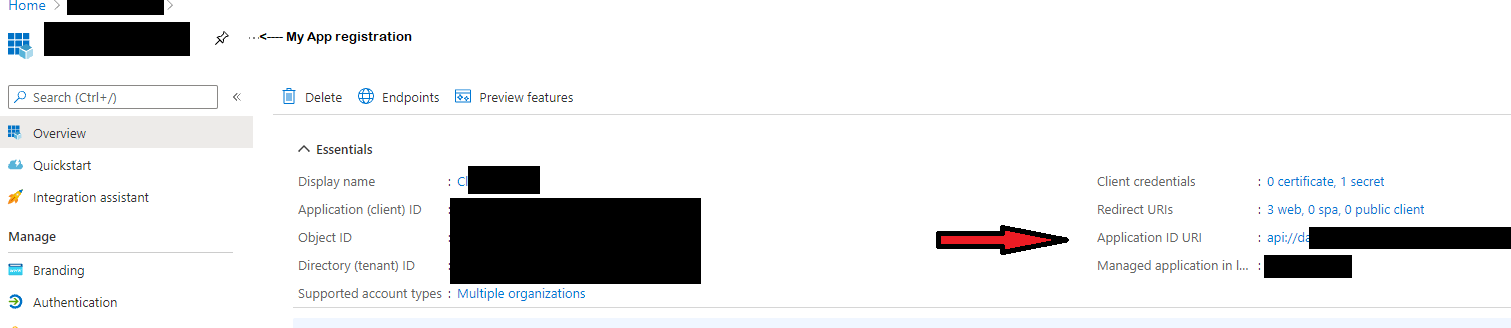
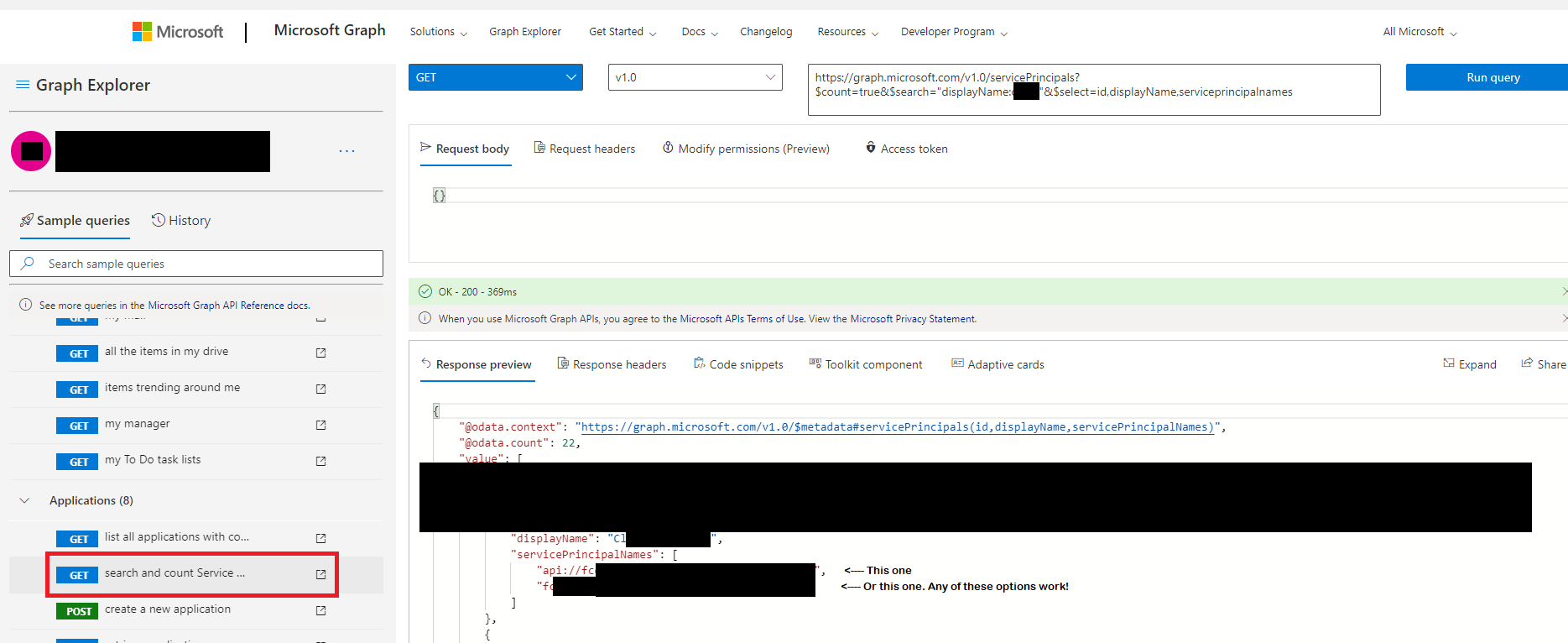
When I Google resource principal i only get alot of answers how to view Service principals which i thought could be something else. But it seem that thats the thing i should be searching for within my app registration. And the first Audience example i was trying out, is obviously not the correct value to match the principal with. The correct value, in this case, can be seen atleast in 3 locations that i found worked for me.
- The app registration Application ID URI
- MS Graph Explorer, list your service principals and perhaps filter by your name of the app registration to narrow down your search results
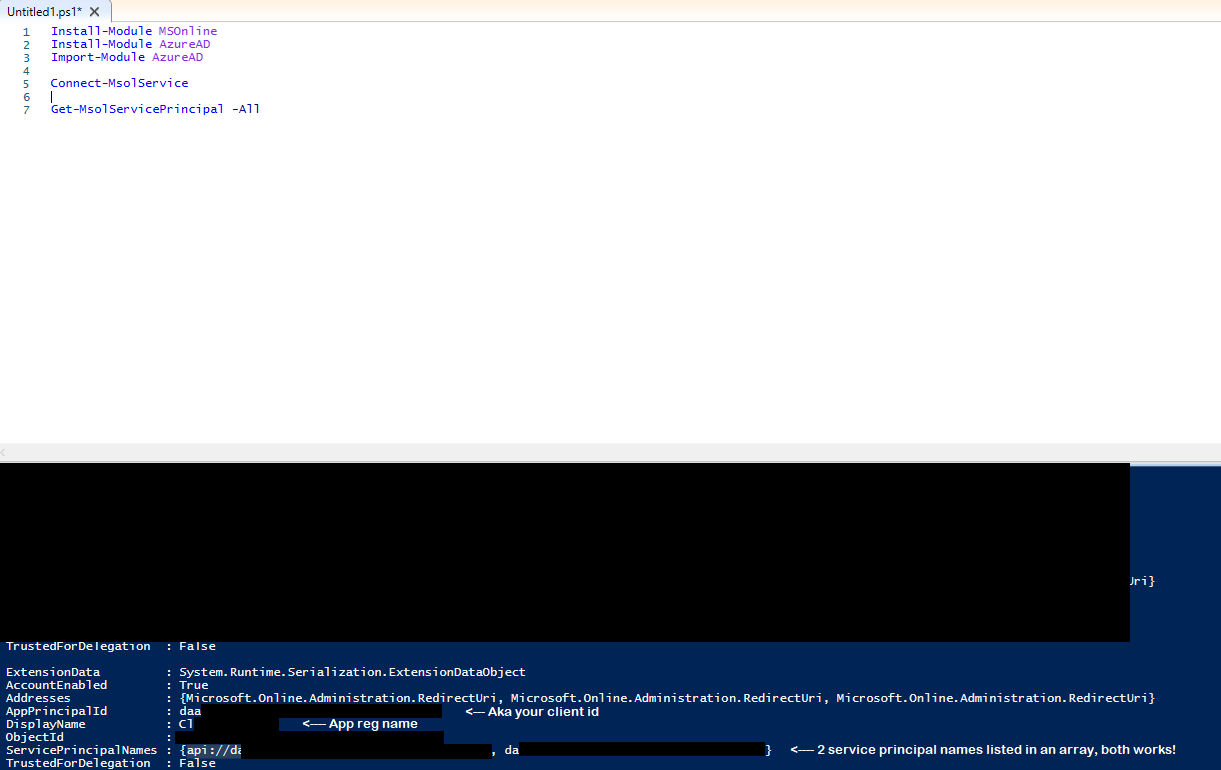
- Powershell, same as option 2, might be another "endpoint" but should do the same work still.
Third option: Make sure you have both Install-Module MSOnline and Install-Module AzureAD installed to your powershell tool. I used Windows PowerShell ISE in order for it to work (the x86 didnt work for me). -> Import the Module for AzureAD -> Then connect with the same acc as Azure-> Run this command: Get-MsolServicePrincipal I also added the -All parameter to get all principals. You could also narrow it down im guessing here, but not important in my case :).
So these where the solutions ive found.
But i also have that other complaint why isnt the error message something like: The Audience does not exist on Tenant X. Please check the name of the Service principal matches with Audience parameter and that the principal exists within the given tenant. //Something like this idk
That would make it so much easier to understand what the error actually is.
Any Azure gurus can definiently give me a lesson of why im wrong if so, im happy to learn the core/fundamentals :)