I have created a basic Bicep template to deploy Azure Automation Acount. It contains a Runbook with the Powershell script and the linked Schedule. So far so good. The problem is to assign the Azure Role (Owner, Contributor, Reader) to the Managed Identity of this AA. I have all the needed values but have no idea how to put them together. To assign Azure Role via Bicep Template you should get the principalId of your Managed Identity of this AA which is pretty easy:
resource autaccount 'Microsoft.Automation/automationAccounts@2021-06-22'
**************************************************************************
output AutAccountPrincipalId string = autaccount.identity.principalId
My idea was to pass the value from this output to the parameter or variable and then use it in the next resource block. It turned out I can not pass the output as the parameter to the next resource block. Can someone assist me with this? The question is - how to use the value from one Bicep resource block in the other resource block?
This is the Bicep template to create Automation Account:
@description('Specifies the location for all resources.')
param location string = resourceGroup().location
var accountname = 'Snapshot'
var runbookname = 'CreateSnapshot'
var schedulename = 'SnapshotHourly'
resource autaccount 'Microsoft.Automation/automationAccounts@2021-06-22' = {
name: accountname
location: location
tags: {
test: 'true'
}
identity: {
type: 'SystemAssigned'
}
properties: {
disableLocalAuth: false
encryption: {
identity: {
}
keySource: 'Microsoft.Automation'
}
publicNetworkAccess: false
sku: {
capacity: null
family: null
name: 'Basic'
}
}
}
resource runbook1 'Microsoft.Automation/automationAccounts/runbooks@2019-06-01' = {
parent: autaccount
name: runbookname
location: location
properties: {
runbookType: 'PowerShell'
logVerbose: false
logProgress: false
logActivityTrace: 0
publishContentLink: {
uri: 'https://raw.githubusercontent.com/................'
}
}
}
resource schedule1 'Microsoft.Automation/automationAccounts/schedules@2020-01-13-preview' = {
parent: autaccount
name: schedulename
properties: {
startTime: '23:30'
expiryTime: ''
interval: 1
frequency: 'Hour'
timeZone: 'Europe/Riga'
}
}
resource link 'Microsoft.Automation/automationAccounts/jobSchedules@2020-01-13-preview' = {
name: guid('xxx05')
parent: autaccount
dependsOn: [
runbook1
]
properties: {
parameters: {}
runbook: {
name: runbookname
}
schedule: {
name: schedulename
}
}
}
output AutAccountPrincipalId string = autaccount.identity.principalId
The last resource block which actually assigns the Azure Role to MI is as follows:
@description('The principal to assign the role to')
param principalId string = 'abc897c3-ac9a-42e6-bc3f-xxxxxxxxxxxx'
@description('Built-in role to assign')
@allowed([
'Owner'
'Contributor'
'Reader'
])
//param builtInRoleType string = 'Owner'
@description('A new GUID used to identify the role assignment')
param roleNameGuid string = newGuid()
var Owner = '/subscriptions/${subscription().subscriptionId}/providers/Microsoft.Authorization/roleDefinitions/8e3af657-a8ff-443c-a75c-2fe8c4bcb635'
//var Contributor = '/subscriptions/${subscription().subscriptionId}/providers/Microsoft.Authorization/roleDefinitions/b24988ac-6180-42a0-ab88-20f7382dd24c'
//var Reader = '/subscriptions/${subscription().subscriptionId}/providers/Microsoft.Authorization/roleDefinitions/acdd72a7-3385-48ef-bd42-f606fba81ae7'
resource roleassignment 'Microsoft.Authorization/roleAssignments@2020-08-01-preview' = {
name: roleNameGuid
properties: {
principalId: principalId
roleDefinitionId: Owner
}
}
I acquired the principalID value manually from Portal but to automate the thing need it to pass from the blocks above, from output above or by some other way. Can someone assist with that? Thank you in advance!
The updated code is:
@description('Specifies the location for all resources.')
param location string = resourceGroup().location
var accountname = 'SnapshotMgmtv11'
var runbookname = 'Create11'
var schedulename = 'SnapshotHourly11'
resource autaccount 'Microsoft.Automation/automationAccounts@2021-06-22' = {
name: accountname
location: location
tags: {
test: 'true'
}
identity: {
type: 'SystemAssigned'
}
properties: {
disableLocalAuth: false
encryption: {
identity: {
}
keySource: 'Microsoft.Automation'
}
publicNetworkAccess: false
sku: {
capacity: null
family: null
name: 'Basic'
}
}
}
resource runbook1 'Microsoft.Automation/automationAccounts/runbooks@2019-06-01' = {
parent: autaccount
name: runbookname
location: location
properties: {
runbookType: 'PowerShell'
logVerbose: false
logProgress: false
logActivityTrace: 0
publishContentLink: {
uri: 'https://raw.githubusercontent.com/..................'
}
}
}
resource schedule1 'Microsoft.Automation/automationAccounts/schedules@2020-01-13-preview' = {
parent: autaccount
name: schedulename
properties: {
startTime: '08:30'
expiryTime: ''
interval: 1
frequency: 'Hour'
timeZone: 'Europe/Riga'
}
}
resource link 'Microsoft.Automation/automationAccounts/jobSchedules@2020-01-13-preview' = {
name: guid('riniv011')
parent: autaccount
dependsOn: [
runbook1
]
properties: {
parameters: {}
runbook: {
name: runbookname
}
schedule: {
name: schedulename
}
}
}
@description('A new GUID used to identify the role assignment')
param roleNameGuid string = newGuid()
//var Owner = '/subscriptions/${subscription().subscriptionId}/providers/Microsoft.Authorization/roleDefinitions/8e3af657-a8ff-443c-a75c-2fe8c4bcb635'
var Contributor = '/subscriptions/${subscription().subscriptionId}/providers/Microsoft.Authorization/roleDefinitions/b24988ac-6180-42a0-ab88-20f7382dd24c'
//var Reader = '/subscriptions/${subscription().subscriptionId}/providers/Microsoft.Authorization/roleDefinitions/acdd72a7-3385-48ef-bd42-f606fba81ae7'
resource roleassignment 'Microsoft.Authorization/roleAssignments@2020-08-01-preview' = {
name: roleNameGuid
dependsOn: [
autaccount
]
properties: {
principalId: autaccount.identity.principalId
roleDefinitionId: Contributor
}
}
CodePudding user response:
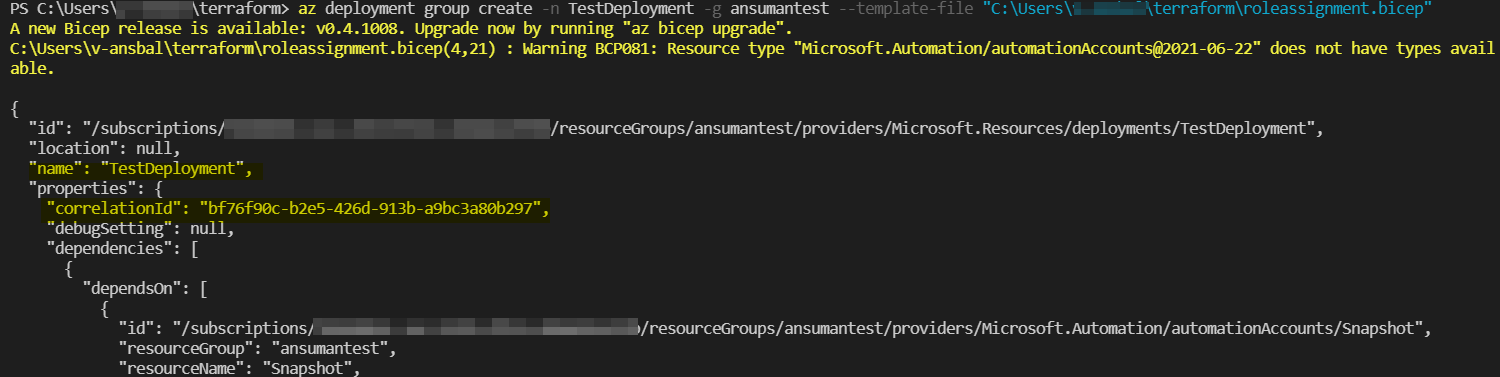
If you are deploying role assignement for resource group scope then you can use the something like below:
I tested it for creating only automation account and assigning the owner role at resource group for the system assigned identity of the automation account.
param location string = resourceGroup().location
var accountname = 'Snapshot'
resource autaccount 'Microsoft.Automation/automationAccounts@2021-06-22' = {
name: accountname
location: location
tags: {
test: 'true'
}
identity: {
type: 'SystemAssigned'
}
properties: {
disableLocalAuth: false
encryption: {
identity: {
}
keySource: 'Microsoft.Automation'
}
publicNetworkAccess: false
sku: {
capacity: null
family: null
name: 'Basic'
}
}
}
param roleNameGuid string = guid('Owner')
var Owner = '/subscriptions/${subscription().subscriptionId}/providers/Microsoft.Authorization/roleDefinitions/8e3af657-a8ff-443c-a75c-2fe8c4bcb635'
resource roleassignment 'Microsoft.Authorization/roleAssignments@2020-08-01-preview' = {
name: roleNameGuid
properties: {
principalId: autaccount.identity.principalId
roleDefinitionId: Owner
principalType:'ServicePrincipal'
}
}
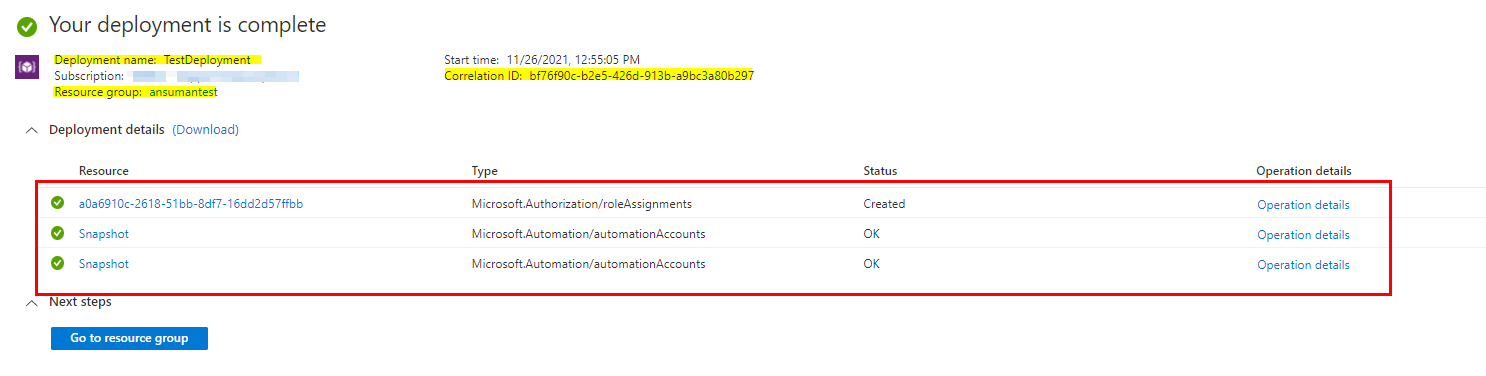
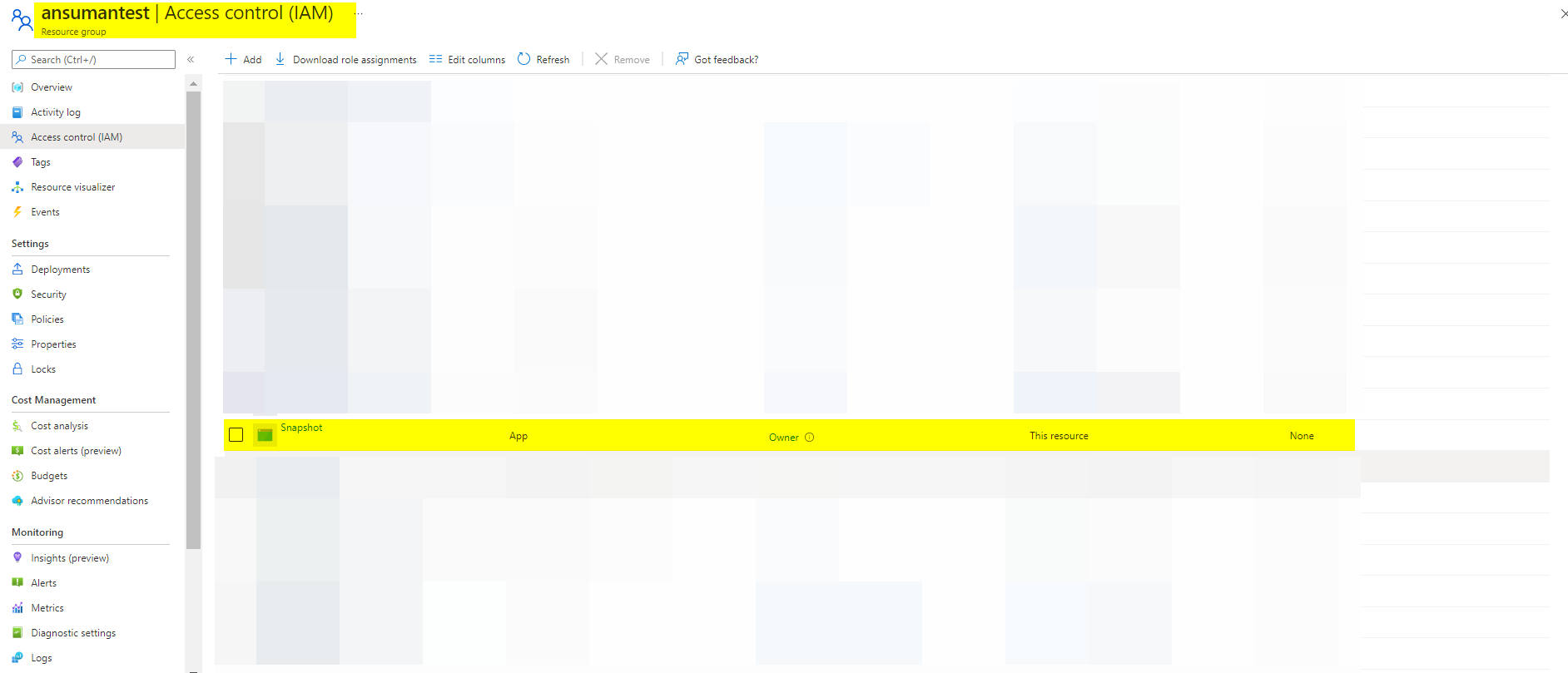
Output:
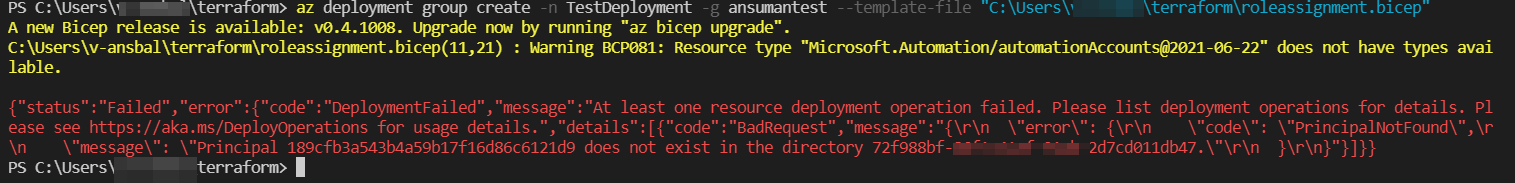
Update:
For the below error :
Please add the principalType:'ServicePrincipal' in the role assignment block , as I have updated in the above code.