I hope I could explain, sorry for my english
Proto Local Address Foreign Address State PID
TCP 0.0.0.0:135 0.0.0.0:0 LISTENING 1160
TCP 0.0.0.0:445 0.0.0.0:0 LISTENING 4
TCP 0.0.0.0:5040 0.0.0.0:0 LISTENING 8864
TCP 0.0.0.0:5357 0.0.0.0:0 LISTENING 4
TCP 0.0.0.0:7680 0.0.0.0:0 LISTENING 14052
TCP 0.0.0.0:49664 0.0.0.0:0 LISTENING 964
TCP 0.0.0.0:49665 0.0.0.0:0 LISTENING 872
TCP 0.0.0.0:49666 0.0.0.0:0 LISTENING 1696
TCP 0.0.0.0:49667 0.0.0.0:0 LISTENING 1448
TCP 0.0.0.0:49668 0.0.0.0:0 LISTENING 3380
TCP 0.0.0.0:49710 0.0.0.0:0 LISTENING 944
but what i want
Local Address
135
445
5040
5357
7680
49664
49665
49666
49667
49668
49710
Also, how can I show this on the screen with what code?
CodePudding user response:
Get-NetTCPConnection is the powershell-equivalent of netstat, and it helpfully separates out the port numbers you're looking for. For example, here's what it looks like normally:
Get-NetTCPConnection -LocalAddress 0.0.0.0 -State Listen
LocalAddress LocalPort RemoteAddress RemotePort State AppliedSetting OwningProcess
------------ --------- ------------- ---------- ----- -------------- -------------
0.0.0.0 58369 0.0.0.0 0 Listen 3892
0.0.0.0 49677 0.0.0.0 0 Listen 792
0.0.0.0 49672 0.0.0.0 0 Listen 3900
And then to display just the port numbers:
Get-NetTCPConnection -LocalAddress 0.0.0.0 -State Listen |
Select-Object -ExpandProperty LocalPort
58369
49677
49672
CodePudding user response:
If the string output is acceptable, then one of the easiest ways to achieve your desired result is to simply remove the unwanted string with regex. However it will mess up the formatting.
(netstat -ano) -replace '0\.0\.0\.0:'
Proto Local Address Foreign Address State PID
TCP 135 0 LISTENING 868
TCP 445 0 LISTENING 4
TCP 5040 0 LISTENING 7288
TCP 5357 0 LISTENING 4
TCP 5985 0 LISTENING 4
TCP 6783 0 LISTENING 5128
TCP 47001 0 LISTENING 4
TCP 49664 0 LISTENING 976
TCP 127.0.0.1:6463 0 LISTENING 14660
TCP 127.0.0.1:6800 0 LISTENING 7468
TCP 127.0.0.1:8094 0 LISTENING 4348
This is a huge drawback from Powershell's object based output. You could try to correct the alignment manually if you so desire..
(netstat -ano) -replace '0\.0\.0\.0:(\d )','$1 '
Proto Local Address Foreign Address State PID
TCP 135 0 LISTENING 868
TCP 445 0 LISTENING 4
TCP 5040 0 LISTENING 7288
TCP 5357 0 LISTENING 4
TCP 5985 0 LISTENING 4
TCP 6783 0 LISTENING 5128
TCP 47001 0 LISTENING 4
TCP 127.0.0.1:8094 0 LISTENING 4348
TCP 127.0.0.1:8763 0 LISTENING 5128
TCP 127.0.0.1:9527 0 LISTENING 5128
TCP 127.0.0.1:37014 0 LISTENING 4576
Again, these examples really only benefit the user viewing it. If you want to use the data later on, you'd have to parse it. At this point you really should look at the powershell alternatives such as 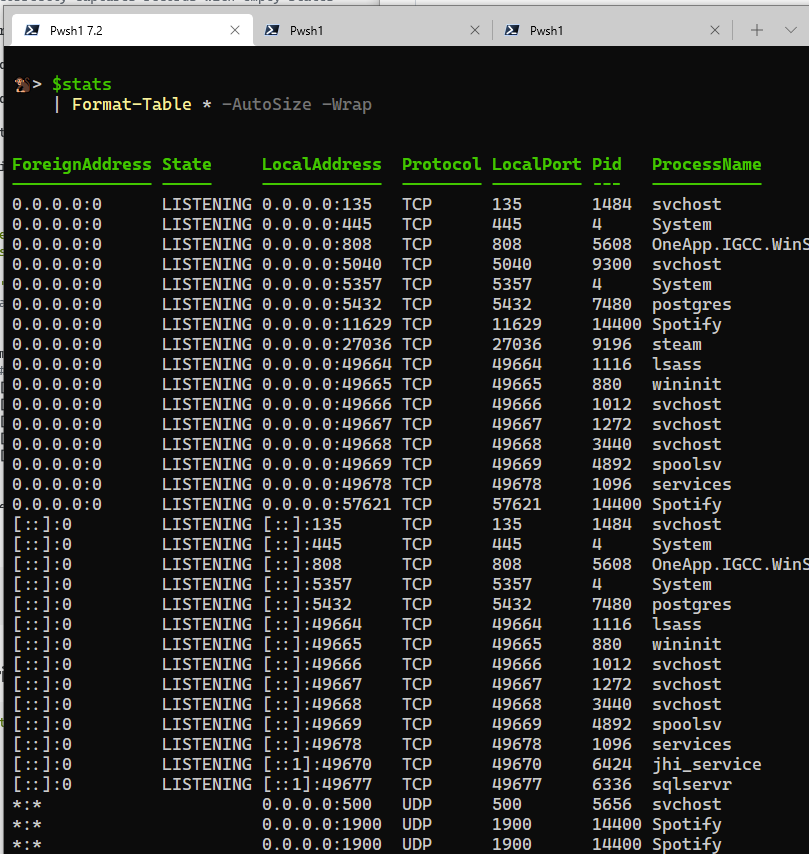
Objects are Created Automatically from a Regex's Capture Group Names
$RegexNetstat = @'
(?x)
# parse output from: "netstat -a -n -o
# you do not need to skip or filter lines like: "| Select-Object -Skip 4"
# because this correctly captures records with empty States
^\s
(?<Protocol>\S )
\s
(?<LocalAddress>\S )
\s
(?<ForeignAddress>\S )
\s
(?<State>\S{0,})?
\s
(?<Pid>\S )$
'@
if (! $NetstatStdout) {
$NetstatStdout = & netstat -a -n -o
}
# If you're on Pwsh7 you can simplify it using null-*-operators
# $NetstatStdout ??= & netstat -a -n -o
function Format-NetStat {
param(
# stdin
[Parameter(Mandatory, ValueFromPipeline)]
[AllowEmptyString()]
[AllowNull()]
[Alias('Stdin')]
[string]$Text
)
process {
if ($Text -match $RegexNetstat) {
$Matches.Remove(0)
$hash = $Matches
$hash['Process'] = Get-Process -Id $hash.Pid
$hash['ProcessName'] = $hash['Process'].ProcessName
$hash['LocalPort'] = $hash['LocalAddress'] -split ':' | select -last 1
[pscustomobject]$Matches
}
}
}
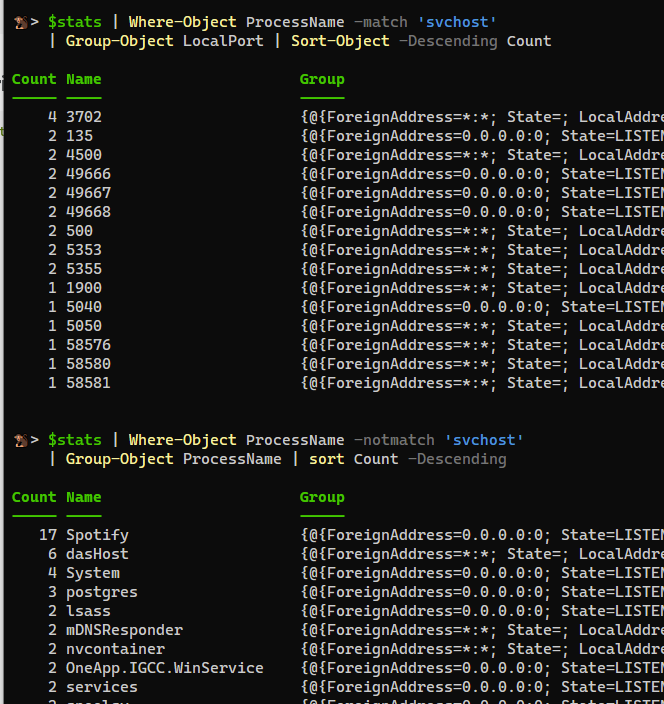
Piping Results
They are true objects, so you can pipe, filter, group, etc. as normal. (I cached Stdout for this demo, so you can compare output of the same results)
usage:
$Stats = $NetstatStdout | Format-NetStat
$stats | Format-Table
Your Original Column Layout
PS> $stats | Ft -AutoSize Protocol, LocalPort, ForeignAddress, State, PID
Protocol LocalPort ForeignAddress State Pid
-------- --------- -------------- ----- ---
TCP 135 0.0.0.0:0 LISTENING 1484
TCP 445 0.0.0.0:0 LISTENING 4
TCP 808 0.0.0.0:0 LISTENING 5608
TCP 5040 0.0.0.0:0 LISTENING 9300
TCP 5357 0.0.0.0:0 LISTENING 4
TCP 5432 0.0.0.0:0 LISTENING 7480
TCP 11629 0.0.0.0:0 LISTENING 14400
TCP 27036 0.0.0.0:0 LISTENING 9196
TCP 49664 0.0.0.0:0 LISTENING 1116
TCP 49665 0.0.0.0:0 LISTENING 880
TCP 49666 0.0.0.0:0 LISTENING 1012
TCP 49667 0.0.0.0:0 LISTENING 1272
TCP 49668 0.0.0.0:0 LISTENING 3440
TCP 49669 0.0.0.0:0 LISTENING 4892
TCP 49678 0.0.0.0:0 LISTENING 1096
TCP 57621 0.0.0.0:0 LISTENING 14400
TCP 1053 127.0.0.1:1054 ESTABLISHED 22328
TCP 1054 127.0.0.1:1053 ESTABLISHED 22328
TCP 5354 0.0.0.0:0 LISTENING 5556
TCP 5354 127.0.0.1:49671 ESTABLISHED 5556
TCP 5354 127.0.0.1:49672 ESTABLISHED 5556
TCP 6463 0.0.0.0:0 LISTENING 16780
TCP 7659 127.0.0.1:7660 ESTABLISHED 18428
TCP 7660 127.0.0.1:7659 ESTABLISHED 18428
TCP 7661 127.0.0.1:7662 ESTABLISHED 4792
TCP 7662 127.0.0.1:7661 ESTABLISHED 4792
TCP 7665 127.0.0.1:7666 ESTABLISHED 1340
TCP 7666 127.0.0.1:7665 ESTABLISHED 1340
TCP 7667 127.0.0.1:7668 ESTABLISHED 11212
TCP 7668 127.0.0.1:7667 ESTABLISHED 11212
Originally from: Parsing Native Apps/Invoke-Netstat