with the confidentiality, integrity, authentication, four features, not enough people communication on both sides of the security is guaranteed, is the real security,
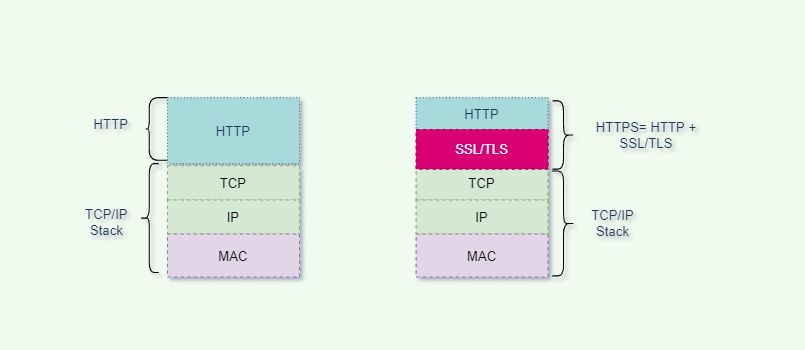
the HTTPS protocol
specifies the new agreement, the default port number 443, what other request - response model, message structure, request method, URI, header fields, connection management, and so on are completely using HTTP, but different port and remove the clear transmission,
s between the TCP/IP and HTTP increased the TLS/SSL security protocol, from the original HTTP over TCP/IP into HTTP over SSL/TLS, let the HTTP operation on the security of SSL/TLS protocol,
SSL Secure Sockets Layer (Secure Sockets Layer)
is a very good security communication protocol,
the TLS (Transport Layer Security, Transport Layer Security)
the TLS record protocol, handshake protocol, warning protocols, change password specification agreement, extension protocol such as of several sub agreement , comprehensive use of the symmetric encryption, asymmetric encryption, identity authentication etc. many cutting-edge technologies, cryptography this combination encryption algorithm called cipher suite (cipher suite) , named suite is very regular,
Such as "ECDHE - the RSA - AES256 - GCM - SHA384", according to the key exchange algorithm + signature algorithm + + the symmetric encryption algorithm algorithm consisting of:
"The meaning of this suite is: use the key exchange ECDHE algorithm, using the RSA signature and authentication, shaking hands after using AES symmetric encryption, a 256 - bit key length, grouping pattern GCM, message authentication and random Numbers generated using the algorithm SHA384
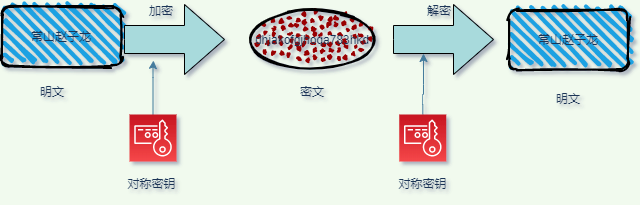
symmetric encryption
use of encryption and decryption keys are the same, is a "symmetry" , as long as both sides pledged not to reveal that others know this key, the communication is confidential, common with RC4 symmetric encryption algorithm, DES, 3 DES, AES, ChaCha20 etc., but before the three algorithms are considered to be unsafe, usually it is prohibited to use, the current commonly used only AES and ChaCha20, AES means "of" Advanced Encryption Standard (Advanced Encryption Standard) , the key length can be 128192 or 256, it is a replacement for the DES algorithm, security intensity is high, the performance is also very good, and some hardware will do a special optimization, so very popular, is the most widely used symmetric Encryption algorithm,
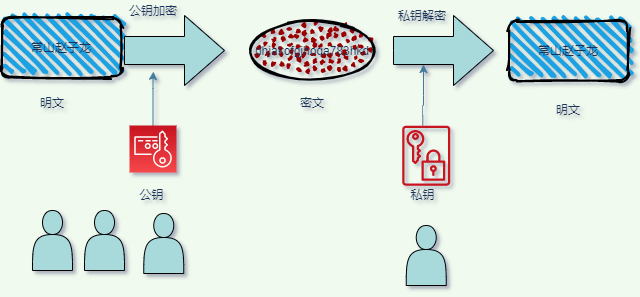
asymmetric encryption
Is composed of two keys, respectively is the public key (public key), and "private key (private key) ", two keys are different, this also is the origin of asymmetric, using the public key can be anyone, the private key is secret, public and private keys can be used to encrypt decrypt, public-key encryption cipher can only use the decrypted, and vice versa,
The TLS in common encryption algorithms are DH, RSA, ECC, DSA, etc., where RSA , it's security based on integer factorization "mathematical problems , use the product of two large prime Numbers as the material to generate the key, want from the public key is very difficult to calculate the private key,
ECC (Elliptic Curve Cryptography) "rising star" in the asymmetric encryption, it based on the mathematical problem of elliptic curve discrete logarithm , using a specific curve equation and bp generate a public key and a private key, ECDHE son algorithm used for key exchange, ECDSA is used for digital signatures,
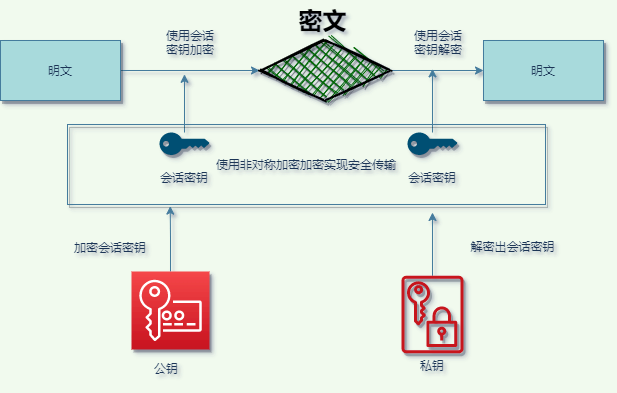
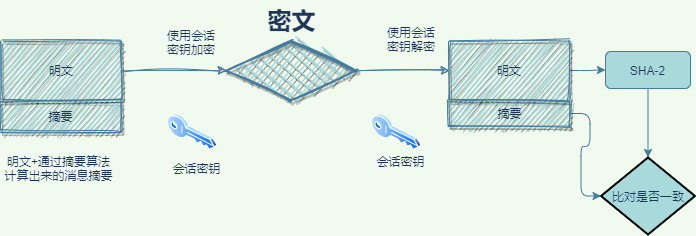
symmetric encryption and asymmetric encryption mode:
the encryption process is as follows:
First create a random number of symmetric encryption key, the session key (the session key);
Need to transport the plaintext message, to use the session key encryption for symmetric encryption performance is good, then use asymmetric encryption public-key encrypt session key, because the session key is very short, usually only 16 bytes or 32 bytes, so the encryption also not too slow, here is mainly solve the problem of the performance of asymmetric encryption, at the same time realize the secret session key exchange,
After the other party receives the ciphertext using asymmetric encryption private key to decrypt the step on the encrypted session key, then USES the session key to decrypt the encrypted message clear,
the algorithm
the algorithm's main purpose is to realize the integrity, through the common hash function, the hash function, at the same time, the algorithm is a one-way encryption algorithm, there is no key, also cannot decrypt the encrypted data, which is not is derived from "the" clear, for example, we have heard or used the MD5 (Message Digest 5) , SHA - 1 (Secure Hash Algorithm (1), they are the two most commonly used Algorithm, this paper can generate the number of 16 bytes and 20 bytes the
integrity or to be built on confidentiality, we mixed encryption used in combination with the aforementioned "session key to encrypt plaintext message + summary, so that hackers won't be able to get clear, can't do change, there's a term called" hash message authentication code (HMAC) ",
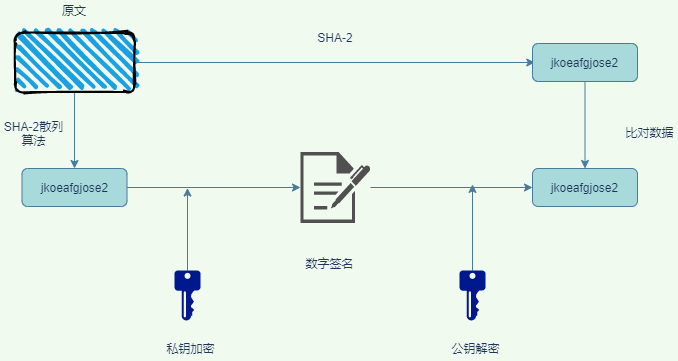
digital signature
using asymmetric encryption "private key" encryption of the original, the other is the use of asymmetric encryption public key to decrypt the, again than to decrypt the original text through the algorithm calculation in this paper, and the decryption of the comparison are consistent, like sign papers so you can prove that the message is, indeed, send you,
CA
CA also be format to a public key signature certification, not simply to bind public key holders in just a matter of identity, but also contains the serial number, purpose, issuer, valid time, etc., put these into a package signed again, fully proved that the public key associated with a variety of information, the formation of "digital Certificate (Certificate),"
