For an S3 bucket is there a way to allow public get access but restrict public uploads? i.e. everyone can view the files but only my server (IAM credentials) can upload.
My bucket policy looks like this:
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "PrivatePut",
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::123:user/Access"
},
"Action": [
"s3:PutObject"
],
"Resource": "arn:aws:s3:::foo/*"
},
{
"Sid": "PublicGet",
"Effect": "Allow",
"Principal": "*",
"Action": [
"s3:GetObject"
],
"Resource": "arn:aws:s3:::foo/*"
}
]
}
But when I try save this bucket policy I get an access denied error
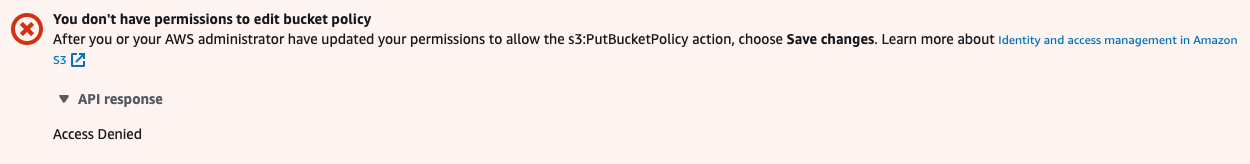
My CORS policy:
[
{
"AllowedHeaders": [
"*"
],
"AllowedMethods": [
"GET",
"PUT",
"POST",
"DELETE",
"HEAD"
],
"AllowedOrigins": [
"http://localhost:3000"
],
"ExposeHeaders": []
},
{
"AllowedHeaders": [
"*"
],
"AllowedMethods": [
"GET",
"PUT",
"POST",
"DELETE",
"HEAD"
],
"AllowedOrigins": [
"https://example.com"
],
"ExposeHeaders": []
}
]
Not sure what to de/select for the Block public access settings
Currently they're all checked except for Block public and cross-account access to buckets and objects through any public bucket or access point policies
Also, adding "AllowedOrigins": ["http://localhost:3000"] to the CORS policy seems suss.
CodePudding user response:
When adding a Bucket Policy to an Amazon S3 bucket, turn off both "Block public access" options that mention "public bucket or access point policies". This should be sufficient to fix your issue.
Generally, granting public access is done via a bucket policy:
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "PublicGet",
"Effect": "Allow",
"Principal": "*",
"Action": [
"s3:GetObject"
],
"Resource": "arn:aws:s3:::foo/*"
}
]
}
Granting access to a specific user is best done as a policy on the IAM User themselves rather than the bucket policy:
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "PrivatePut",
"Effect": "Allow",
"Action": "s3:PutObject",
"Resource": "arn:aws:s3:::foo/*"
}
]
}
There is no need to modify CORS settings unless you are experiencing a specific error that mentions CORS.
