I need to obtain the addresses (absolute) of all functions that call the below function. Can this be done in Windbg ?
The function that I would like to find all callers of is KeBugCheckEx
lkd> uf nt!KeBugCheckEx
CodePudding user response:
That cannot be a realistic requirement
KeBugCheckEx is an exported Function as such it can be called by AnyOne who wants to call it
dumpbin /exports c:\Windows\System32\ntoskrnl.exe | findstr "KeBugCheckEx"
1114 442 003F8FA0 KeBugCheckEx
over and above as commented by Raymond chen indirect calls are not resolvable statically
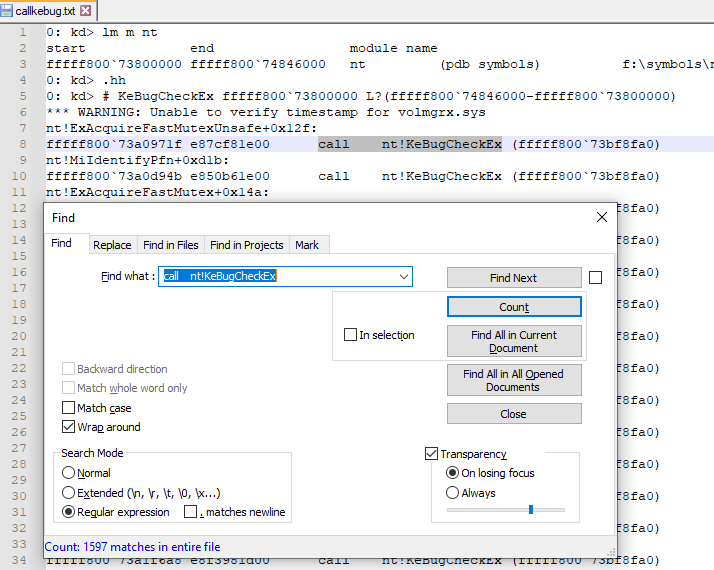
still if you want to go ahead try this
this may scrap around 50% hopefully :)
0: kd> lm m nt
start end module name
fffff800`73800000 fffff800`74846000 nt (pdb symbols) f:\symbols\ntkrnlmp.pdb\68A17FAF3012B7846079AEECDBE0A5831\ntkrnlmp.pdb
0: kd> .hh
0: kd> # KeBugCheckEx fffff800`73800000 L?(fffff800`74846000-fffff800`73800000)
*** WARNING: Unable to verify timestamp for volmgrx.sys
nt!ExAcquireFastMutexUnsafe 0x12f:
fffff800`73a0971f e87cf81e00 call nt!KeBugCheckEx (fffff800`73bf8fa0)
nt!MiIdentifyPfn 0xd1b:
fffff800`73a0d94b e850b61e00 call nt!KeBugCheckEx (fffff800`73bf8fa0)
nt!ExAcquireFastMutex 0x14a:
fffff800`73a0dbaa e8f1b31e00 call nt!KeBugCheckEx (fffff800`73bf8fa0)
nt!ExAcquireCacheAwarePushLockSharedEx 0x14a:
fffff800`73a0df1a e881b01e00 call nt!KeBugCheckEx (fffff800`73bf8fa0)
nt!ExAcquirePushLockExclusiveEx 0x146:
fffff800`73a0e4b6 e8e5aa1e00 call nt!KeBugCheckEx (fffff800`73bf8fa0)
nt!ExAcquirePushLockSharedEx 0x13d:
fffff800`73a0e66d e82ea91e00 call nt!KeBugCheckEx (fffff800`73bf8fa0)
nt!ExReleaseResourceLite 0x18d:
fffff800`73a0ef7d e81ea01e00 call nt!KeBugCheckEx (fffff800`73bf8fa0)
nt!ExAcquireResourceExclusiveLite 0x2eb:
:>python -c print(len((open('callkebug.txt','r')).readlines())) 3224