Rukmini, the SP has contributor role on the subscription not sure why it is erroring and it worked after ading it in a Reader role?
Here is a snapshot
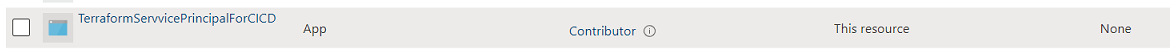
I am trying some operations from az cli(terraform commands) getting the following error:
The client '87c92100-.....' with object id '87c92100....' does not have authorization to perform action 'Microsoft.Resources/subscriptions/resourcegroups/read' over scope '/subscriptions/f151ee3f-4725-......../resourcegroups/tfmainrg' or the scope is invalid
I searched everywhere, RG, AAD, storage account....not able to find where this object or client resdes. Can you please tell me how can I find what object is this? Thanks
CodePudding user response:
I tried to reproduce the same in my environment and got the same error as below:
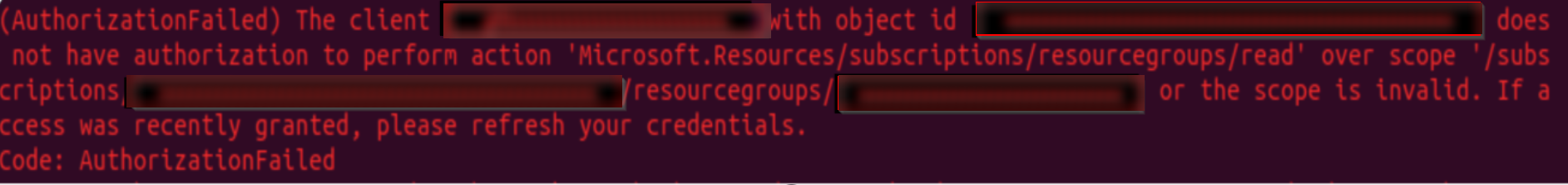
The error "Authorization Failed" usually occurs if the user does not have access/role to read the resource group.
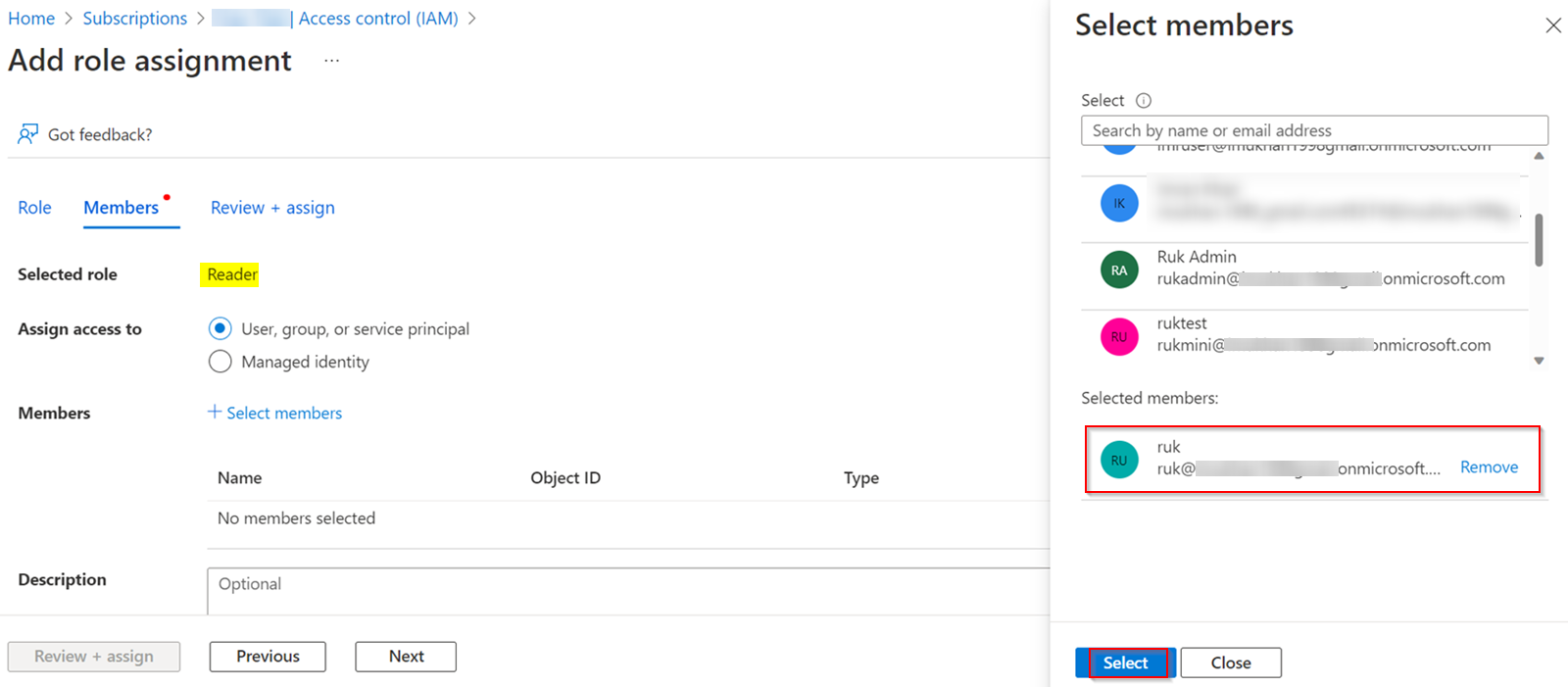
To resolve the error, make sure to assign Reader role to the user in the subscription level like below:
Go to Azure Portal -> Subscriptions -> Select your subscription -> Access control (IAM) -> Add role assignment -> Select Reader
You can also use az cli to assign the Reader role to the user by using below command:
The Owner or User administrator role is required to assign any role. So, use another tenant level Owner to assign the role.
az role assignment create --assignee-object-id UserObjectID --scope subscriptions/SubscriptionID --role reader
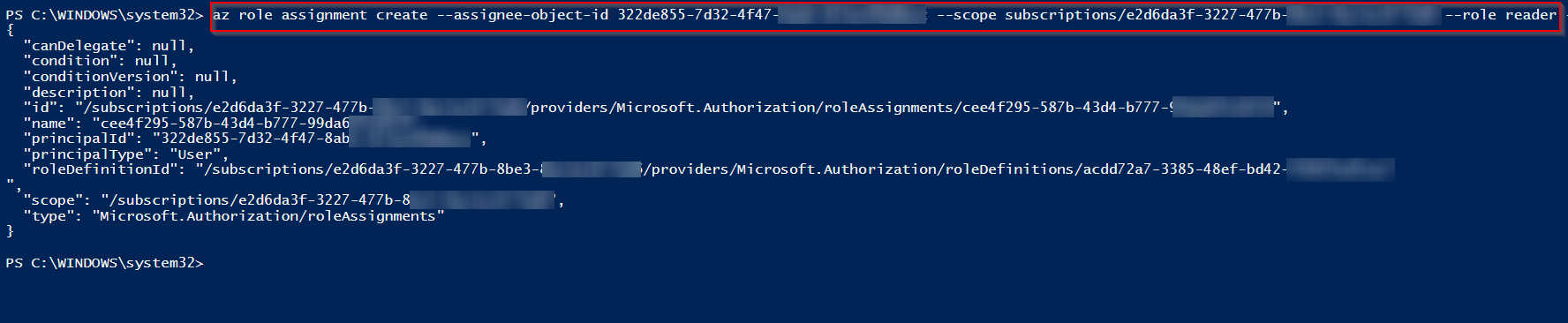
The reader role successfully granted to the user like below:
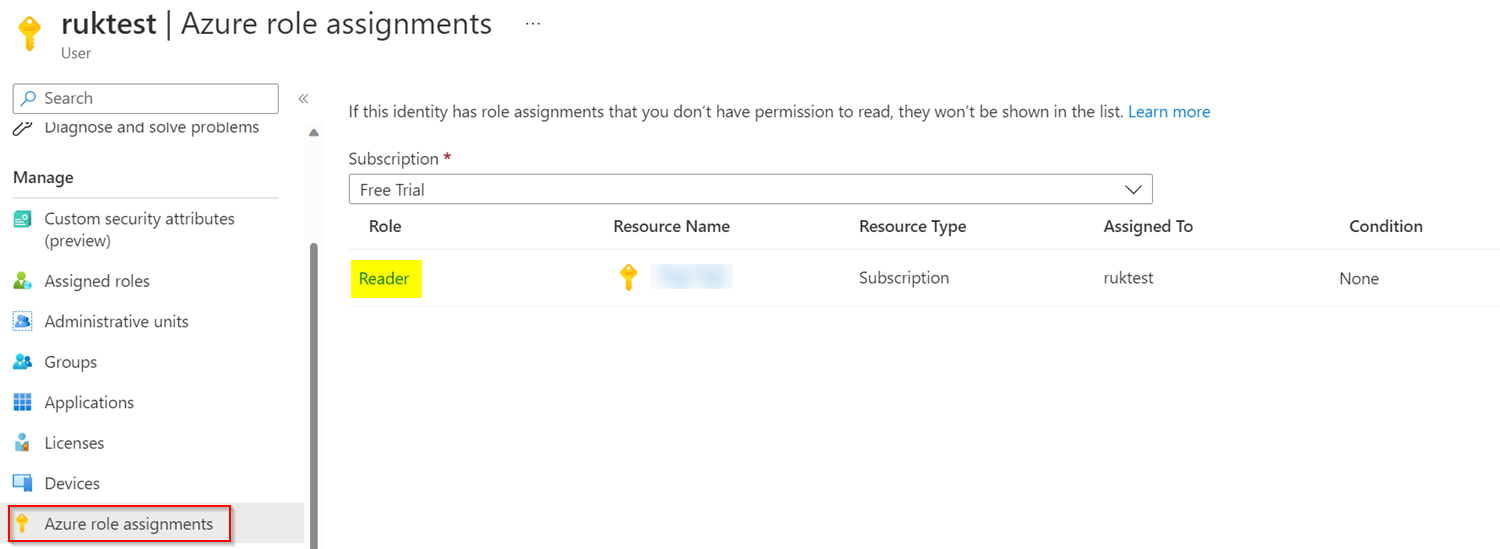
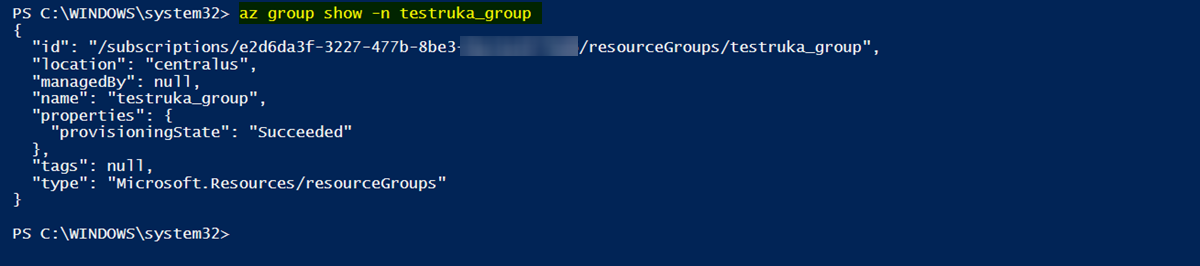
After assigning the role, I am able to read the resource group successfully:
az group show -n ResourceGroupName
Based on your further requirement you can assign the roles by referring to the below MsDoc:
