I would like to create a client on Keycloak with parameters defined when running the curl API.
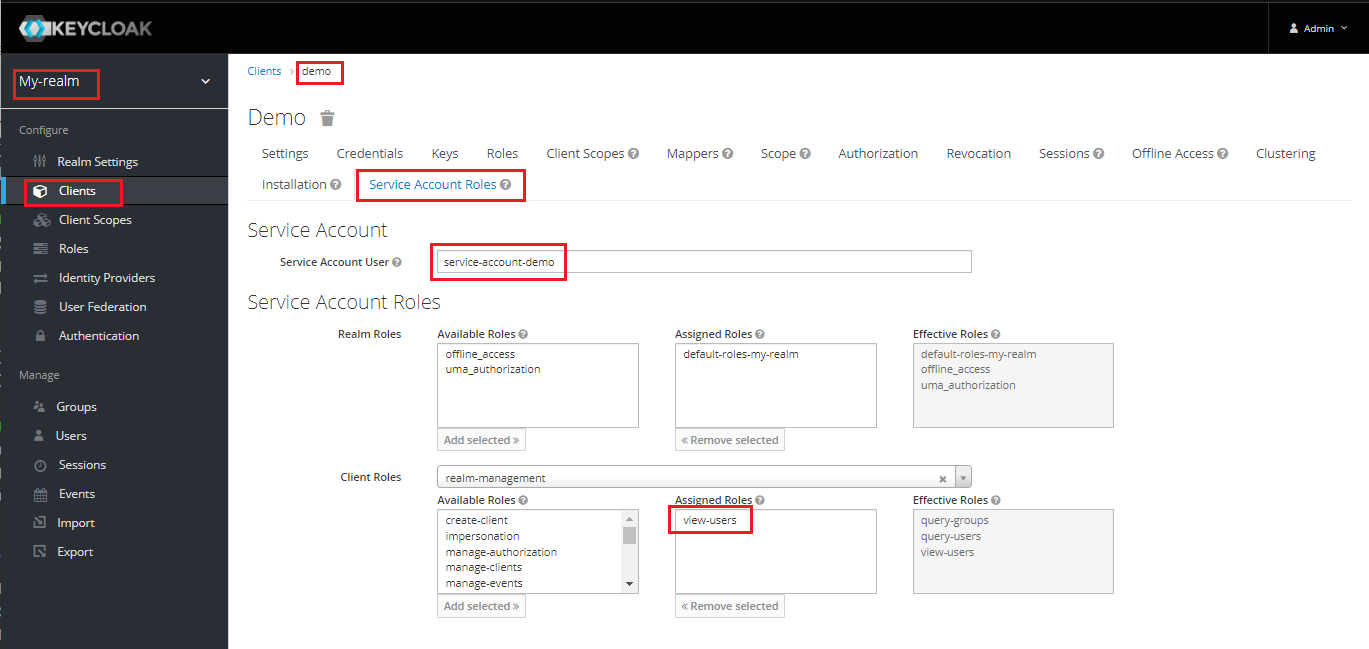
Among the defined parameters I would like to add to the client the "view_users" role, which is found in the "Client Roles" entitled "realm-management".
I would like to reproduce this action with API curl :
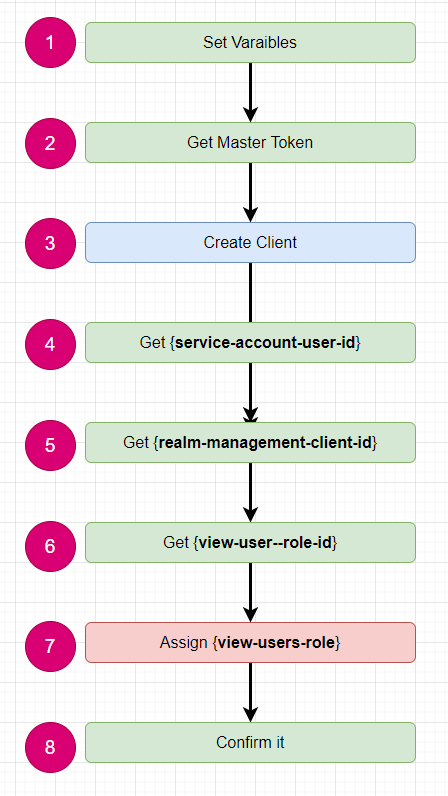
I will demo all of API call by curl
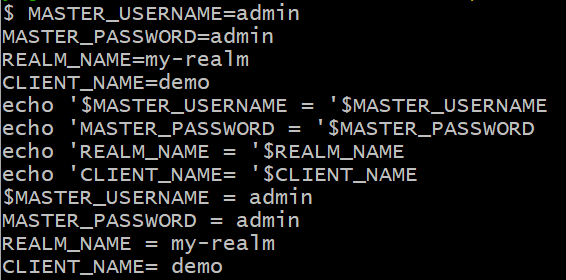
#1 Set {credential, client name, realm name}
MASTER_USERNAME=admin
MASTER_PASSWORD=admin
REALM_NAME=my-realm
CLIENT_NAME=demo
echo '$MASTER_USERNAME = '$MASTER_USERNAME
echo 'MASTER_PASSWORD = '$MASTER_PASSWORD
echo 'REALM_NAME = '$REALM_NAME
echo 'CLIENT_NAME= '$CLIENT_NAME
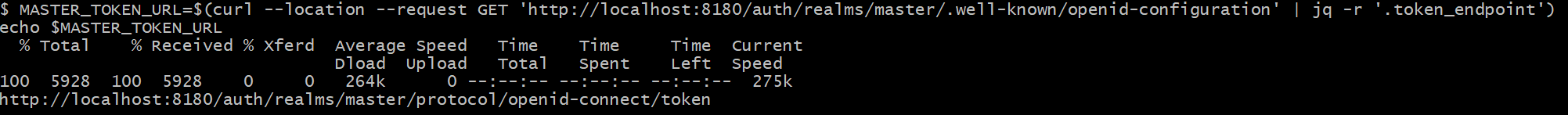
#2 Get master token
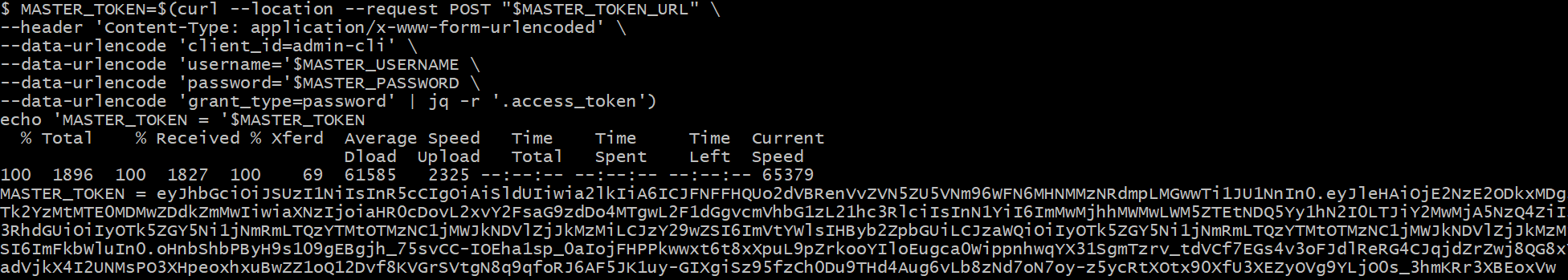
MASTER_TOKEN=$(curl --location --request POST "$MASTER_TOKEN_URL" \
--header 'Content-Type: application/x-www-form-urlencoded' \
--data-urlencode 'client_id=admin-cli' \
--data-urlencode 'username='$MASTER_USERNAME \
--data-urlencode 'password='$MASTER_PASSWORD \
--data-urlencode 'grant_type=password' | jq -r '.access_token')
echo 'MASTER_TOKEN = '$MASTER_TOKEN
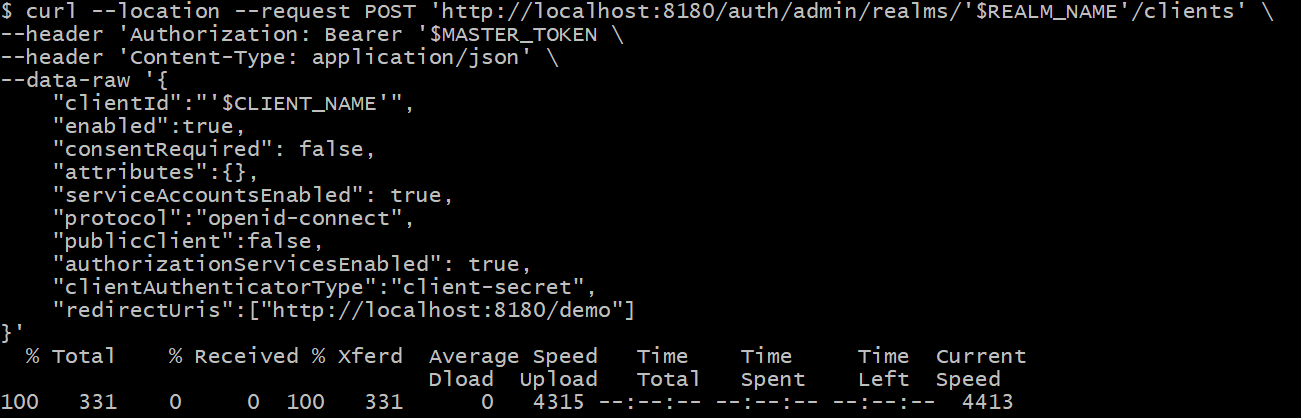
#3 Create client
curl --location --request POST 'http://localhost:8180/auth/admin/realms/'$REALM_NAME'/clients' \
--header 'Authorization: Bearer '$MASTER_TOKEN \
--header 'Content-Type: application/json' \
--data-raw '{
"clientId":"'$CLIENT_NAME'",
"enabled":true,
"consentRequired": false,
"attributes":{},
"serviceAccountsEnabled": true,
"protocol":"openid-connect",
"publicClient":false,
"authorizationServicesEnabled": true,
"clientAuthenticatorType":"client-secret",
"redirectUris":["http://localhost:8180/demo"]
}'
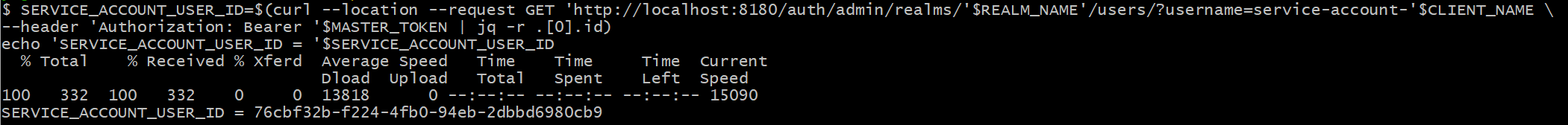
#4 Get {service-account-user-id}
SERVICE_ACCOUNT_USER_ID=$(curl --location --request GET 'http://localhost:8180/auth/admin/realms/'$REALM_NAME'/users/?username=service-account-'$CLIENT_NAME \
--header 'Authorization: Bearer '$MASTER_TOKEN | jq -r .[0].id)
echo 'SERVICE_ACCOUNT_USER_ID = '$SERVICE_ACCOUNT_USER_ID
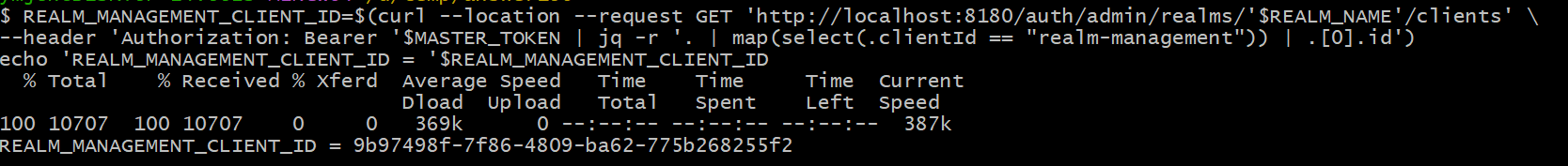
#5 Get {realm-management-client-id}
REALM_MANAGEMENT_CLIENT_ID=$(curl --location --request GET 'http://localhost:8180/auth/admin/realms/'$REALM_NAME'/clients' \
--header 'Authorization: Bearer '$MASTER_TOKEN | jq -r '. | map(select(.clientId == "realm-management")) | .[0].id')
echo 'REALM_MANAGEMENT_CLIENT_ID = '$REALM_MANAGEMENT_CLIENT_ID
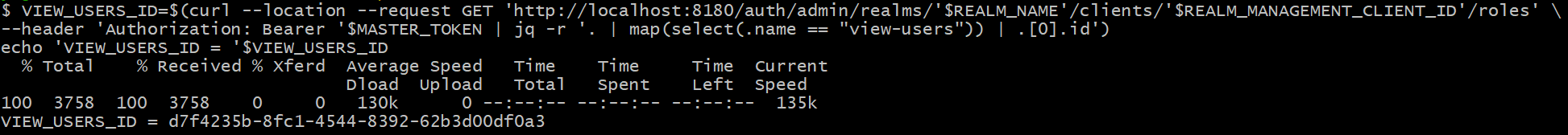
#6 Get {view_user_role_id}
VIEW_USERS_ID=$(curl --location --request GET 'http://localhost:8180/auth/admin/realms/'$REALM_NAME'/clients/'$REALM_MANAGEMENT_CLIENT_ID'/roles' \
--header 'Authorization: Bearer '$MASTER_TOKEN | jq -r '. | map(select(.name == "view-users")) | .[0].id')
echo 'VIEW_USERS_ID = '$VIEW_USERS_ID
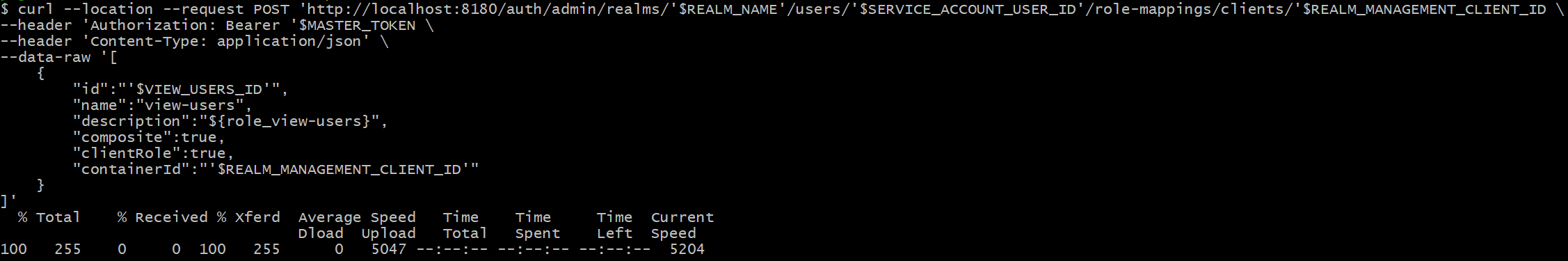
#7 Assign view-users role to client
curl --location --request POST 'http://localhost:8180/auth/admin/realms/'$REALM_NAME'/users/'$SERVICE_ACCOUNT_USER_ID'/role-mappings/clients/'$REALM_MANAGEMENT_CLIENT_ID \
--header 'Authorization: Bearer '$MASTER_TOKEN \
--header 'Content-Type: application/json' \
--data-raw '[
{
"id":"'$VIEW_USERS_ID'",
"name":"view-users",
"description":"${role_view-users}",
"composite":true,
"clientRole":true,
"containerId":"'$REALM_MANAGEMENT_CLIENT_ID'"
}
]'
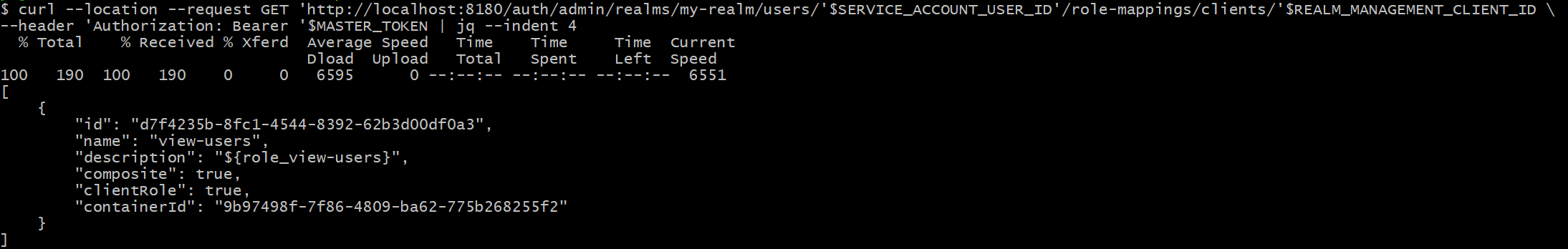
#8 confirm it
Finally, you can confirm it by curl or UI
curl --location --request GET 'http://localhost:8180/auth/admin/realms/my-realm/users/'$SERVICE_ACCOUNT_USER_ID'/role-mappings/clients/'$REALM_MANAGEMENT_CLIENT_ID \
--header 'Authorization: Bearer '$MASTER_TOKEN | jq --indent 4