a, the common Web attacks
1. SQL injection -- -- -- -- -- - common security issues,
Solution: the front page to check the user input data (limit user input type, scope, format, length), you can't just rely on the backend to check the user data, which can improve the efficiency of the back-end processing, and can improve the safety of the back-end data,
Backend don't dynamic SQL statements, use stored procedures query, restrict user access rights to the database, the back-end accept front end data to filter some special characters (such as: "-" character)
The backend if abnormal, want to use a custom error page, prevent users from the default error page to find the server server vulnerabilities,
2. XSS attacks -- -- -- -- -- - relatively complex security problems
Based on DOM XSS attacks, namely, through the browser to run directly js script, do not need to submit the server, the client code,
Such as: is actually sent a legal address add your own scripts, such as: www.xxx.com/search? Wd=... Victims to click www.xxx.com/search? Wd=... Browse the web link, and then the victim's join the malicious code,
Stored XSS attacks is submitted by the input box js script or upload files to the server, from the website of database attack,
Reflected XSS attacks is via the url submission js script to the server, the cause of attack by the victim's request,
3. CSRF attacks -- -- -- -- -- - more dangerous than XSS attacks security problems
Attack way: victims to open the web site A, landing site, A site A save some cookies on the local (not close the browser), the victim and open the web site B, site B save some malicious cookies, and send the victim's request to the web site A B using attack victims website (web site),
4. DoS attacks -- -- -- -- -- - common destructive security issues (if is distributed attacks is the DDos attacks)
Attacks: Ping Flood attack it is using the Ping command packets sent to the server,
5. DNS cache pollution -- -- -- -- -- - a common site inaccessible problem
Attacks: a third party trusted some DNS domain name server cache, but being made some fake domain name server) packet fouling
Dye, pointing in the wrong url,
6. ARP cheating -- -- -- -- -- - common stealing information security problems
Attacks: using the ARP deception, forged into the gateway, let the victim's data after the attacker's computer, so as to grab someone else's user information,
7. The middle attack (session hijacking) -- -- -- -- -- steal information from common security problems
Attacks: hijacked session cookies, the victims victims (A) and (B) communication between after the attacker computer, (common in online chat system)
8. The back door the common software vulnerabilities of -- -- -- -- --
The back door is a bypass security access control and obtain the program or system, the method of the software development phase, the programmers often created within the software defect in the back door so that you can modify the program, if the back door by other people know,
Or not delete before publishing software, so it became a potential safety hazard, common in some hot patch update software,
Attack: use webshell submit malicious dynamic web pages to the web server, and then execute malicious dynamic pages (such as: www.XXX.xom/malicious pages. JSP),
2, Web development compatibility problems
Compatibility problems mainly include the CSS compatibility, js compatible

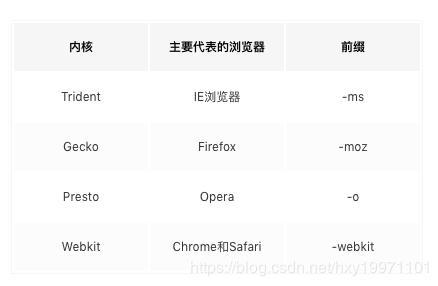
Different browsers default styles:
For some styles need by adding a prefix to solve
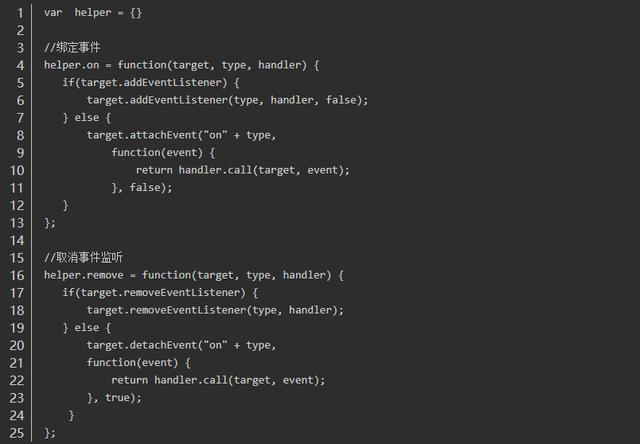
Event compatibility issues, we usually need to encapsulate an adapter, the method of filtering events handle binding, remove, bubbling block and the default event processing
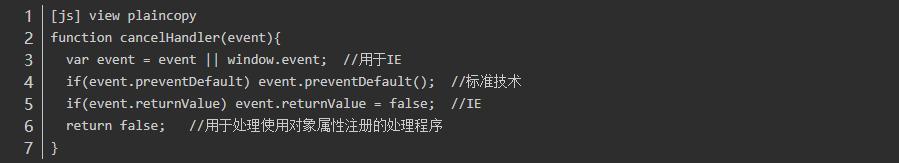
To prevent the default behavior:
The w3c is e.p reventDefault (), IE is used "e.r eturnValue=https://bbs.csdn.net/topics/false;
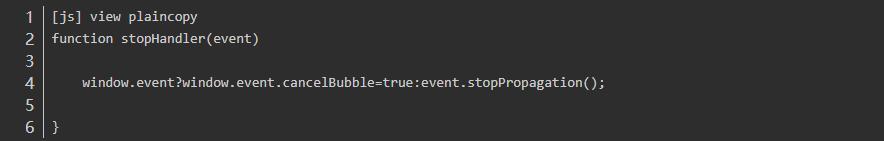
Stop the event bubbling:
The w3c is e.s topPropagation (), IE is the use of e.c. with our fabrication: ancelBubble=true
CodePudding user response:

CodePudding user response:
The original poster can be a blog, but first rather than to write blog post