I'm hoping some AWS policy expert may be able to help me decode what's going on here.
I've been playing with IAM and resource policies in AWS. According to AWS's own documentation, unless there are any explicit denies in all of the policies, the resource policy should take precedence over the IAM policy. See the attached link showing AWS's policy evaluation logic. If the resource policy is an 'allow', then the IAM policy shouldn't be evaluated.
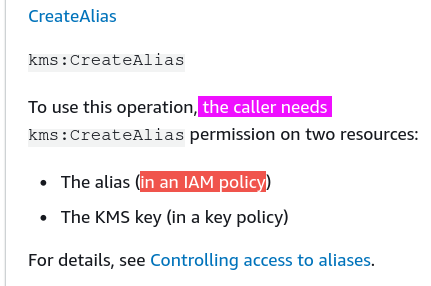
This means that KMS key policies apply only to keys, not aliases.
CodePudding user response:
I believe that the culprit could be that you are missing the kms:DescribeKey in both the IAM and the resource policy. It is listed as required in Controlling access to Aliases document.
- kms:CreateAlias for the KMS key. This permission must be provided in a key policy or in an IAM policy that is delegated from the key policy.
{
"Sid": "Key policy for 1234abcd-12ab-34cd-56ef-1234567890ab",
"Effect": "Allow",
"Principal": {"AWS": "arn:aws:iam::111122223333:user/KMSAdminUser"},
"Action": [
"kms:CreateAlias",
"kms:DescribeKey"
],
"Resource": "*"
}