I have an AWS EC2 load balancer that is in two availability zones. I am using the load balancer to front an apache server on an ec2 instance and I am using Cognito for authentication to the application.
For now, I have identified the private IP addresses of the load balancer network interfaces and created firewall rules on my backend ec2 instance to only allow traffic from the load balancer's private IP addresses. However those private IP addresses are constantly changing.
What is the best practice for setting up firewall rules on my backend ec2 instance to only allowed HTTP requests which are essentially proxied by the load balancer and then authenticated by Cognito?
CodePudding user response:
It is not really clear for me if by firewall you understand Security Groups, because in AWS Security Groups are considered to be stateful firewalls.
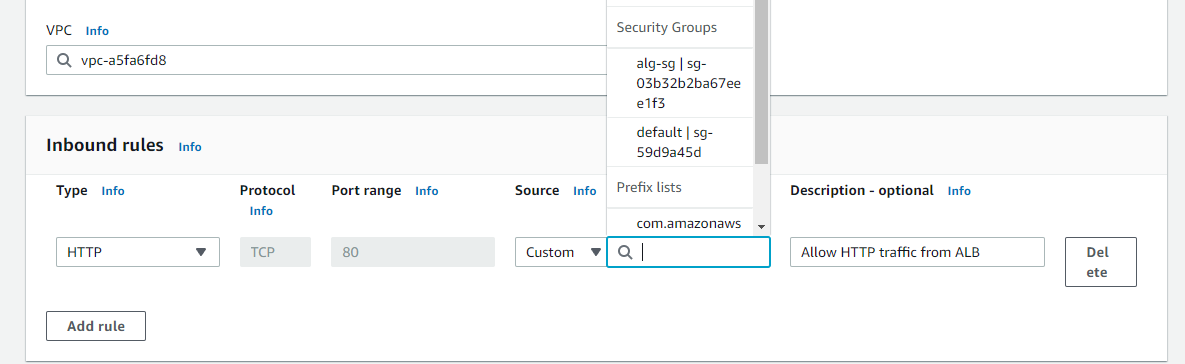
You would not want to directly reference the IP address of the load balancers (I assume you are using Application Load Balancer), because that might change. The solution is to have a Security Group assigned to the load balancer and another one the EC2 instance running the application. The Security Group from the EC2 instance can allow traffic on port 80 from the Security Group attached to the load balancer.
Example of specifying an inbound rule for the Security Group of an instance referencing the Security Group of the Application Load Balancer:
Since you are using Cognito, the authentication should happen before the load balancer, as it is described in the docs. Essentially your clients request a token from Cognito which can be used to authenticate them in your application. You may allow outgoing traffic from your VPC/EC2 instance to Cognito using a NAT or and interface endpoint.