Background Information
I have two separate PowerShell scripts. One uses an ARM template to deploy a function app, along with storage accounts etc. It runs under the context of a security principle we have set up specifically for the function app. I'm using the same security principle to run a second Powershell script that creates an AD Application registration. I've managed to do everything except:
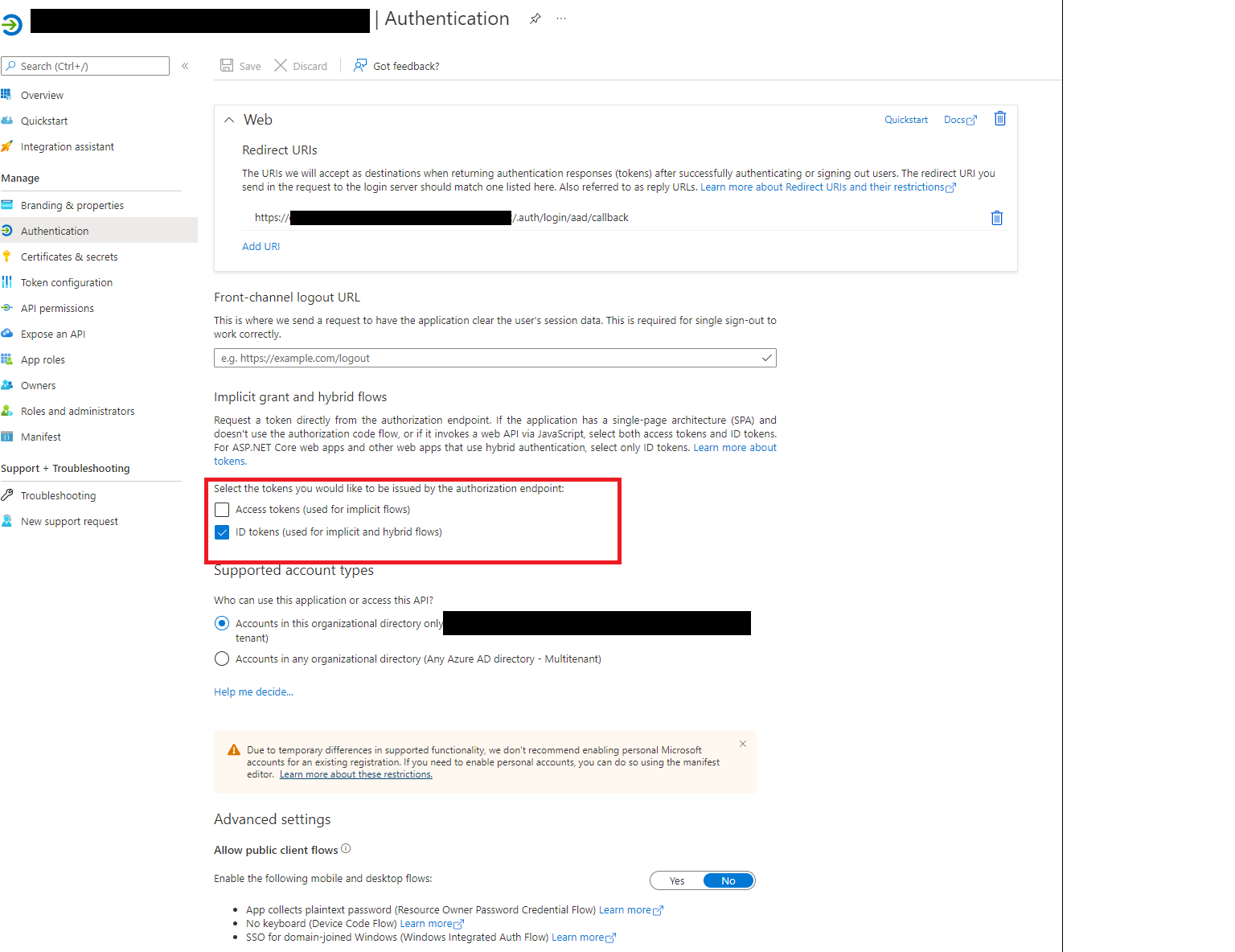
- set up the application so it uses ID Tokens
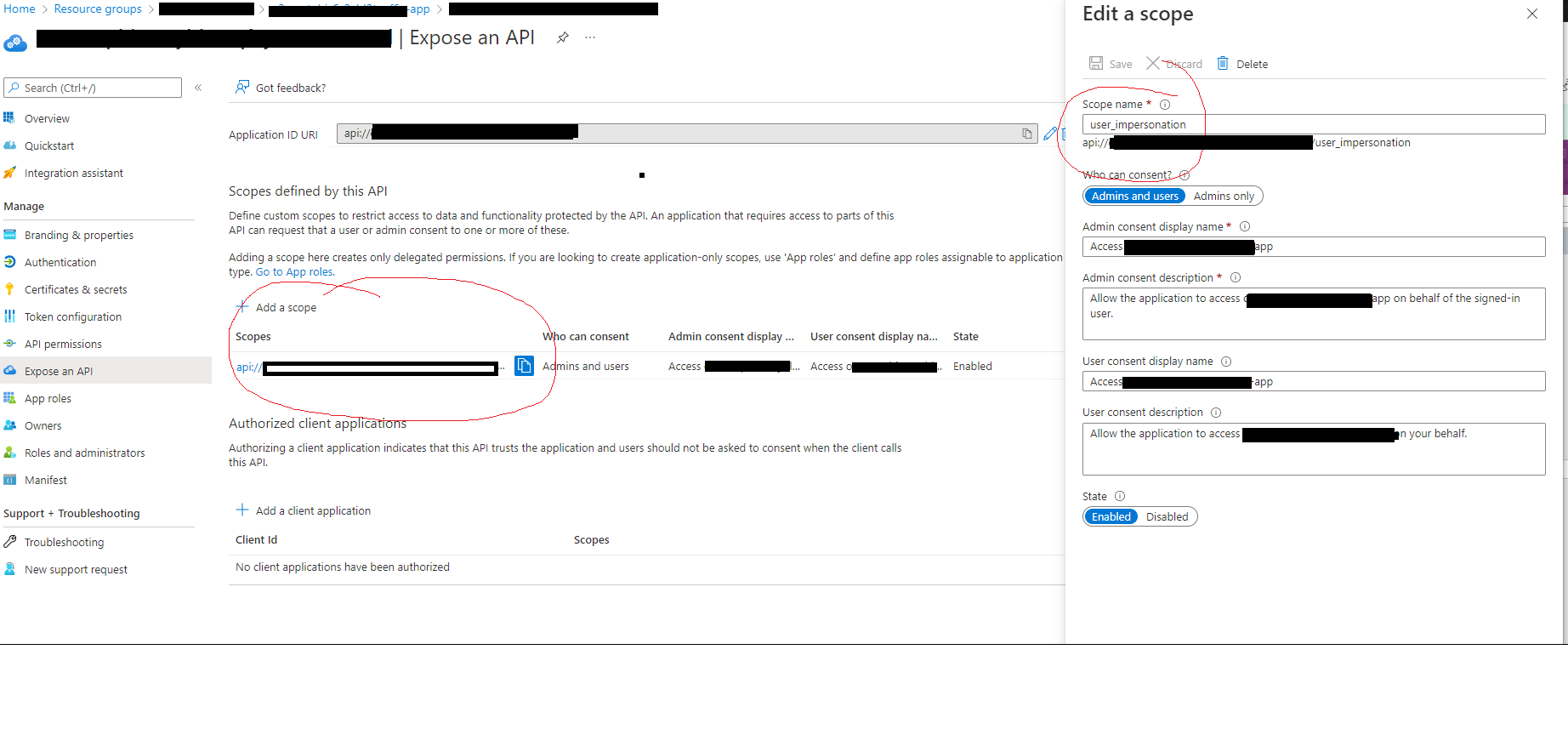
- add scope
- associate the AD application registration as the identity provider for my function app.
This question is specifically about an error I'm running into while try to set up ID tokens. but I'm sharing additional information about what has/hasn't been done yet in case it's relevant.
Problem
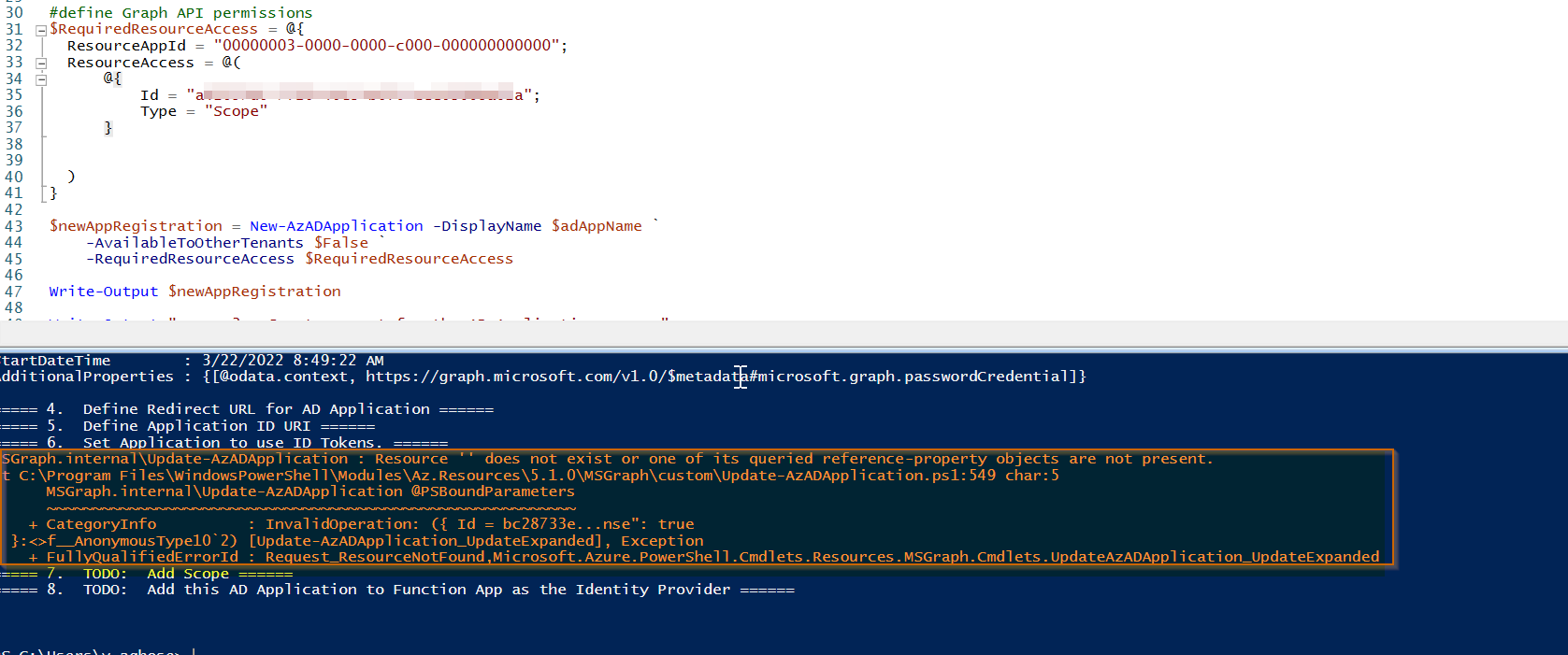
The error that comes up when i try to run my second powershell script is this:
===== 6. Set Application to use ID Tokens ======
Update-AzADApplication_UpdateExpanded: C:\Users\me\Documents\PowerShell\Modules\Az.Resources\5.4.0\MSGraph.Autorest\custom\Update-AzADApplication.ps1:549:5
Line |
549 | Az.MSGraph.internal\Update-AzADApplication @PSBoundParameters
| ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
| Resource '' does not exist or one of its queried reference-property objects are not present.
Here's the code:
Connect-AzAccount -ServicePrincipal -TenantId $AZ_TENANT_ID -Credential $Credential
Set-Azcontext -Subscription $AZ_SUBSCRIPTION_ID -Tenant $AZ_TENANT_ID
#What's the function app name?
$AZ_FUNCTION_APP = az functionapp list `
-g $AZ_RESOURCE_GROUP_NAME `
-o json | ConvertFrom-Json
Write-output $AZ_FUNCTION_APP.Name
Write-Output "===== 1. Query for AZ Fun Details ======"
#Collect Data about the Function app which we need
$appDeets = Get-AzWebApp -ResourceGroupName $AZ_RESOURCE_GROUP_NAME -Name $AZ_FUNCTION_APP.Name
Write-Output $appDeets
$appURL = $appDeets.DefaultHostName
Write-Output "===== 2. Create New basic AD Application Registration ======"
#Create a New AD Application Registration
$adAppName = $AZ_FUNCTION_APP.Name "-AdApp"
#define Graph API permissions
$RequiredResourceAccess = @{
ResourceAppId = "00000003-0000-0000-c000-000000000000";
ResourceAccess = @(
@{
Id = "guid";
Type = "Scope"
},
@{
Id = "guid";
Type = "Scope"
},
@{
Id = "guid";
Type = "Role"
}
)
}
$newAppRegistration = New-AzADApplication -DisplayName $adAppName `
-AvailableToOtherTenants $False `
-RequiredResourceAccess $RequiredResourceAccess
Write-Output $newAppRegistration
Write-Output "===== 3. Create secret for the AD Application ======"
#Create a secret for the new application
$startDate = Get-Date
$endDate= $startDate.AddYears(3)
$newSecret = New-AzADAppCredential -ApplicationId $newAppRegistration.AppId -StartDate $startDate -EndDate $endDate
Write-Output $newSecret
Write-Output "===== 4. Define Redirect URL for AD Application ======"
$redirectURL = "https://$appURL/.auth/login/aad/callback"
Update-AzADApplication -ApplicationId $newAppRegistration.AppId -ReplyUrl $redirectURL | Out-Null
Write-Output "===== 5. Define Application ID URI ======"
#Add Application ID URI
$appIdentifierUri = "api://" $newAppRegistration.AppId
Update-AzADApplication -ApplicationId $newAppRegistration.AppId -IdentifierUri $appIdentifierUri | Out-Null
Write-Output "===== 6. Set Application to use ID Tokens. ======"
Update-AzADApplication -ApplicationId $newAppRegistration.AppId -Oauth2RequirePostResponse
Write-Output "===== 7. TODO: Add Scope ======"
Write-Output "===== 8. TODO: Add this AD Application to Function App as the Identity Provider ======"
Screenshots
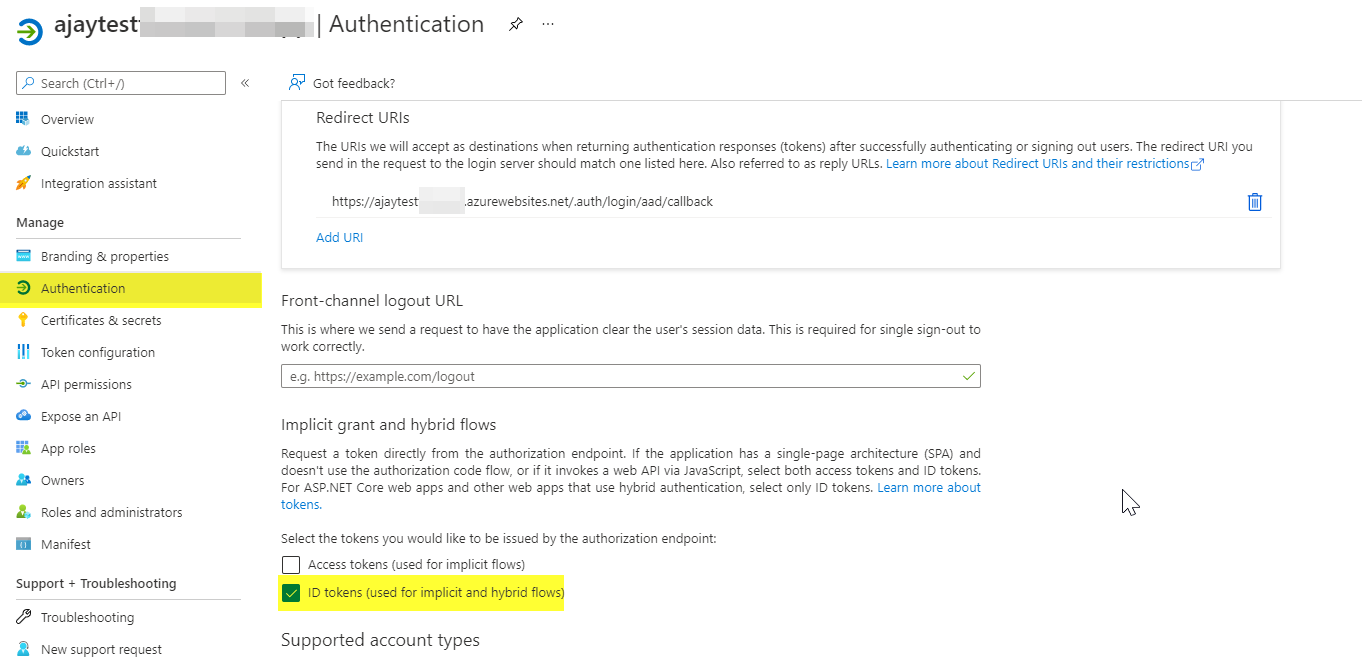
Here are two screenshots showing what i'm after / how I do it when I set up the app auth manually:
This is what the scope looks like when I create it manually:
Any tips would be appreciated.
EDIT 1
What I've done so far:
I've downloaded a copy of the AD Application Registration manifest file before and after enabling the Id Tokens. The only difference I can see is the one field:
"oauth2AllowIdTokenImplicitFlow": false,
The difference btwn when I do this manually via the GUI and when I do this with the Powershell script is the login / user that's being used.
When I sign in manually to azure portal to create the registration for the function app, the login account has the following roles assigned under the specific subscription:
Owner
User Access Administrator
This is different from the security principle that's being used by Powershell. Its been added to the subscription as a
contributor
Clearly, we don't want to add owner status to this application security principle. But is there a specific set of permissions needed for a security principle to be able to create another AD application registration? So far, I've been ok to create and update the AD App reg as you can see from the script. But I thought I'd ask / table all the info ... in case it helps.
EDIT 2
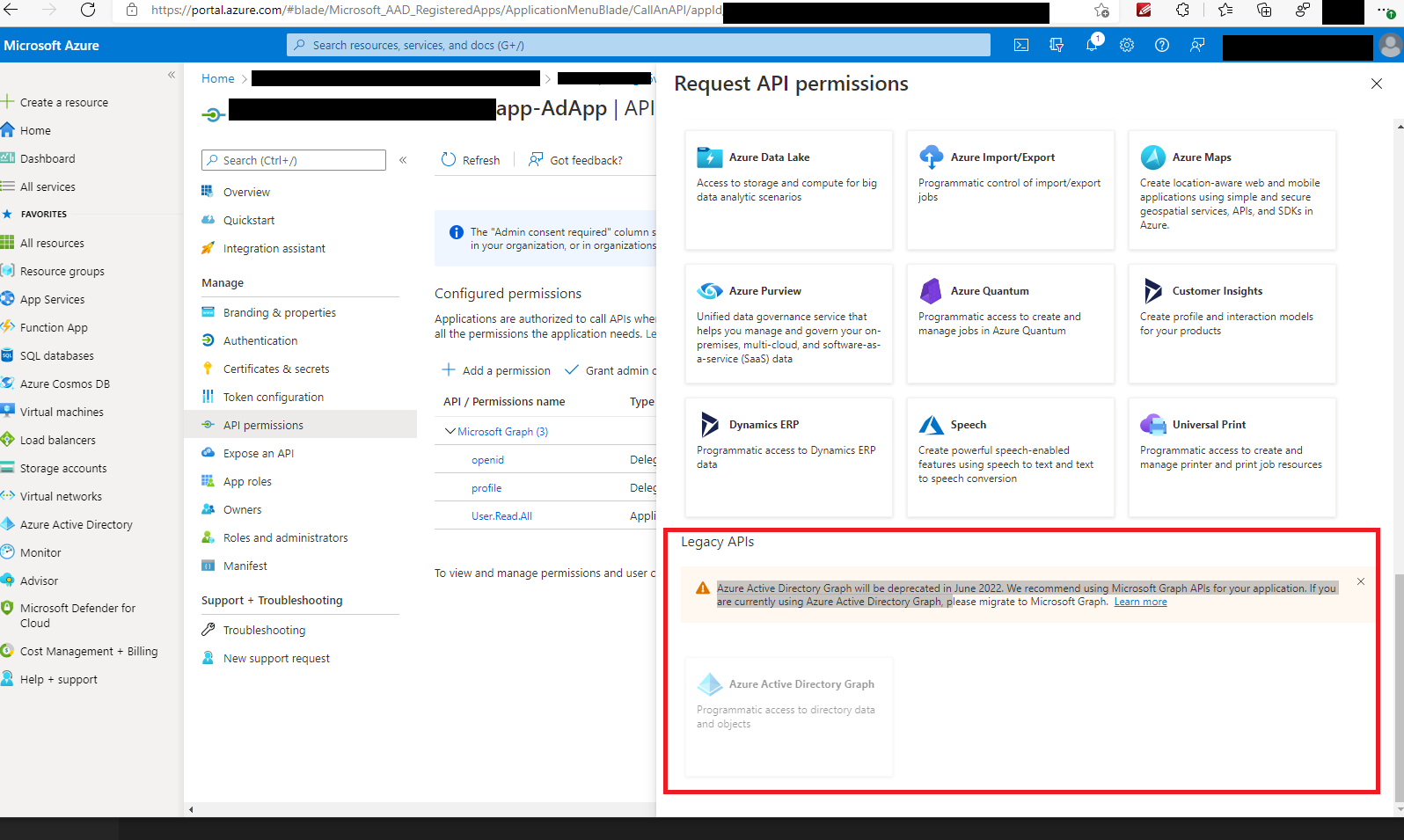
Unfortunately, Azure Active Directory Graph isn't an option for me:
Is this something I can enable as an admin / owner of the subscription? Or better yet, since it's being deprecated, how can I do this via Graph API?
CodePudding user response:
We have tried the same with our Azure function to add identity (Azure Ad Authentication) and getting the same error.
After did some research concluded that we can do the same with Azure Ad Graph Explorer instead of using PowerShell.
To do with Azure Ad graph Explorer please refer this 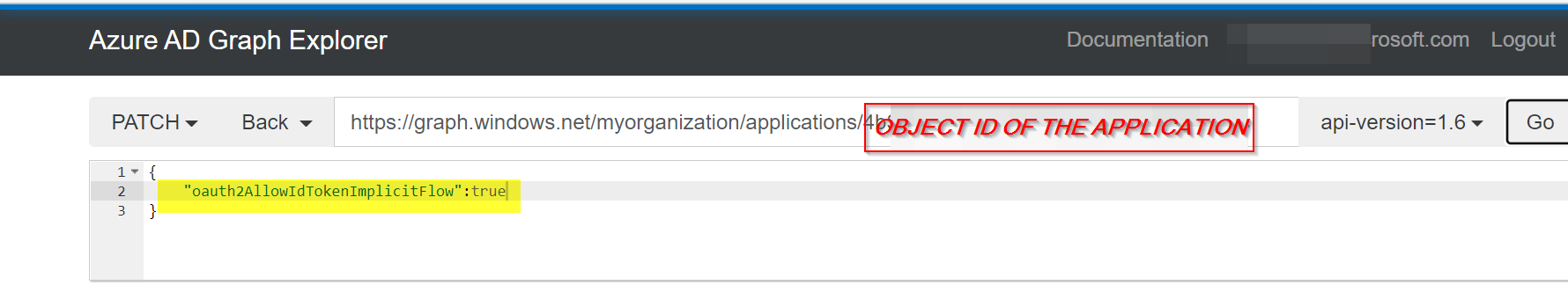
OUTPUT DETAILS:-
For more information please refer the below links:
UPDATE:-
There is still time to deprecate Azure AD Graph Explorer , But we can use till June 2022 : https://graphexplorer.azurewebsites.net/#
Open the above link and login with your account.
and mention the below API in search bar
https://graph.windows.net/myorganization/applications/{object id of the application}?api-version=1.6
and in request body :
{
"oauth2AllowIdTokenImplicitFlow":true
}
For Microsoft graph explorer, i could not see any API to enable the ID Token .