We are distributing an ASP.NET MVC 3.0 application (C# and .NET 4.0), and some customers had an iframe over it for some customizations, but now it has stopped working. I thought that it was related with some security changes we have made:
Set "Content-Security-Policy" to "frame-ancestors 'self'"
Force cookies properties (in global.asax.cs cause in 4.0 there isn't any other way to set the samesite property):
- SameSite: Strict
- Secure: true
- HttpOnly: true
And after remove "Content-Security-Policy" and the cookie rewriting rule it has worked. But then, when I try to authenticate (user/password) the authentication cookie is not sent, and I can't rewrite them because they don't come with the request.
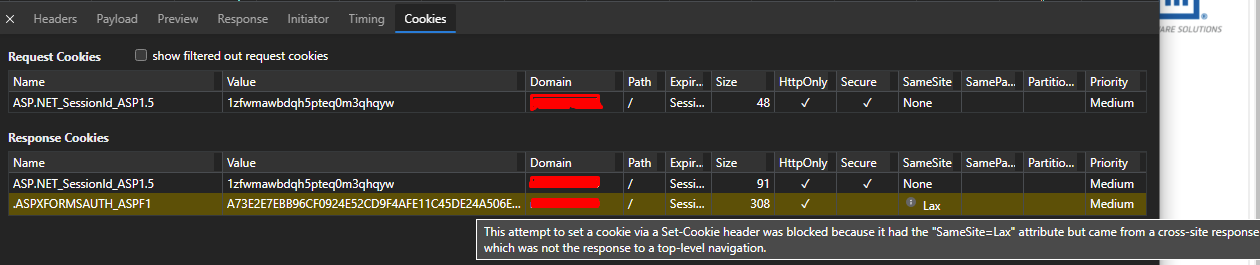
I see the following message on Cookie tab of network request/response: "This attempt to set a cookie via a Set-Cookie header was blocked because it had the "SameSite=Lax" attibute but came from a cross-site response which was not the response to a top-level navigation".
I've read that it's related with "recent" browsers security updates and/or Windows/ASP.NET security patches, but after some research no solutions worked for me...
CodePudding user response:
I've found the solution(s):
Upgrade to .NET Framework 4.7.2: Ok, I'm on 4.0, and I've plans to upgrade to 4.8 this year. I've tested on a branch, and changing some of the new cookie properties of that framework, it works.
But I've a customer that is using iframes over our website, and it isn't easy neither fast to migrate to 4.8, so I've found the solution with the URL Rewrite module of IIS. And I've included a rule for Content Security Policy to add my (their) iFrame page host. I've followed those links:
And my latest version of web.config for that customer:
<rewrite>
<outboundRules>
<preConditions>
<!-- Checks User Agent to identify browsers incompatible with SameSite=None -->
<preCondition name="IncompatibleWithSameSiteNone" logicalGrouping="MatchAny">
<add input="{HTTP_USER_AGENT}" pattern="(CPU iPhone OS 12)|(iPad; CPU OS 12)" />
<add input="{HTTP_USER_AGENT}" pattern="(Chrome/5)|(Chrome/6)" />
<add input="{HTTP_USER_AGENT}" pattern="( OS X 10_14).*(Version/).*((Safari)|(KHTML, like Gecko)$)" />
</preCondition>
</preConditions>
<!-- Adds or changes SameSite to None for the session cookie -->
<!-- Note that secure header is also required by Chrome and should not be added here -->
<rule name="SessionCookieAddNoneHeader">
<!-- Use this regex if your OS/framework/app adds SameSite=Lax automatically to the end of the cookie -->
<match serverVariable="RESPONSE_Set-Cookie" pattern="((.*)(ASP.NET_SessionId[^=]*)(=.*))(?=SameSite)" />
<action type="Rewrite" value="{R:1}; SameSite=None; Secure=true" />
</rule>
<!-- Adds or changes SameSite to None for the session cookie -->
<!-- Note that secure header is also required by Chrome and should not be added here -->
<rule name="FormsCookieAddNoneHeader">
<!-- Use this regex if your OS/framework/app adds SameSite=Lax automatically to the end of the cookie -->
<match serverVariable="RESPONSE_Set-Cookie" pattern="((.*)(ASPXFORMSAUTH[^=]*)(=.*))(?=SameSite)" />
<action type="Rewrite" value="{R:1}; SameSite=None; Secure=true" />
</rule>
<rule name="RewriteContentSecurityPolicy">
<match serverVariable="RESPONSE_Content-Security-Policy" pattern="(.*)" />
<action type="Rewrite" value="{R:0} iframehost" />
</rule>
<!-- Removes SameSite=None header from all cookies, for most incompatible browsers -->
<rule name="CookieRemoveSameSiteNone" preCondition="IncompatibleWithSameSiteNone">
<match serverVariable="RESPONSE_Set-Cookie" pattern="(.*)(SameSite=None)" />
<action type="Rewrite" value="{R:1}" />
</rule>
</outboundRules>
</rewrite>