I am working on Azure AD authentication. I always get 401 even though my token is valid. Where can I get the value of Tenant and ValidAudience?
app.UseWindowsAzureActiveDirectoryBearerAuthentication(
new WindowsAzureActiveDirectoryBearerAuthenticationOptions
{
Tenant =
TokenValidationParameters = new System.IdentityModel.Tokens.TokenValidationParameters
{
ValidAudience =
}
});
CodePudding user response:
You can give the value of tenant and valid audience by modifying your startup method like below:
app.UseWindowsAzureActiveDirectoryBearerAuthentication(
new WindowsAzureActiveDirectoryBearerAuthenticationOptions
{
Tenant = ConfigurationManager.AppSettings["ida:TenantId"]
TokenValidationParameters = new System.IdentityModel.Tokens.TokenValidationParameters
{
ValidAudience = ConfigurationManager.AppSettings["ida:Audience"]
}
});
The value of ida:TenantId will be your Azure AD tenant ID.
Ensure to add below keys in web.config file -> app settings before calling startup method.
<appSettings>
<add key="ida:ClientId" value="[Enter the Application Id (also named ClientId) for the application]" />
<add key="ida:TenantId" value="[Enter the tenant/Directory Id name]" />
<add key="ida:Audience" value="[Enter App ID URI of your application]" />
</appSettings>
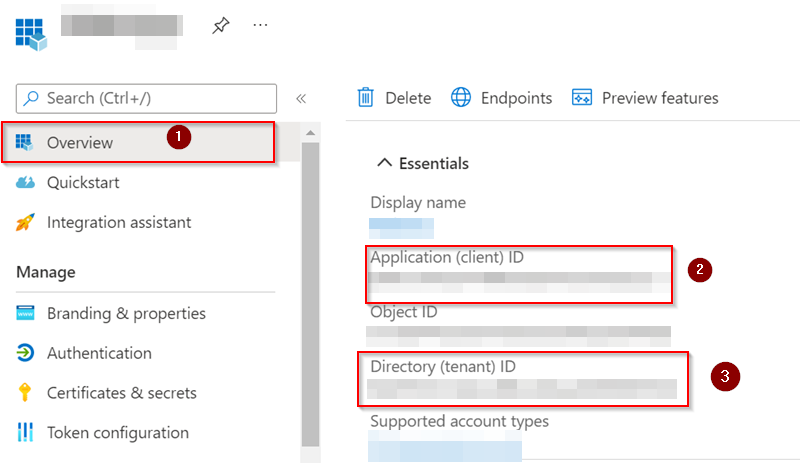
You can find your Application(Client) ID and Tenant(Directory) ID from here:
Go to Azure Portal -> Azure AD -> App Registrations -> Your Application -> Overview
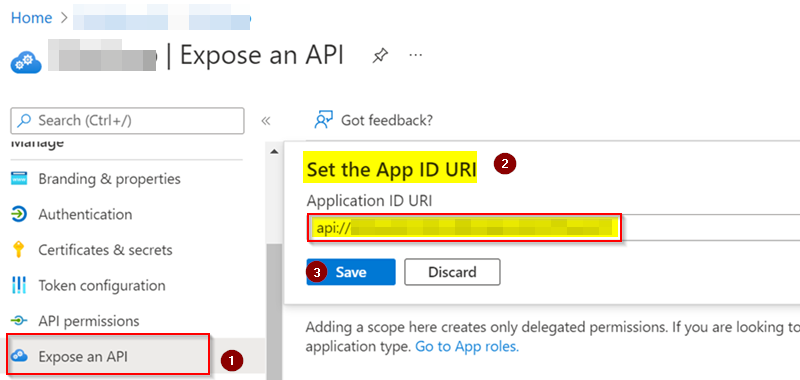
After registering the application in Azure AD, set Application ID URI by exposing the API like below:
The value of ida:Audience will be your Application ID URI that will be in the form of api://yourappid
Make sure to add required scopes to avoid 401 Error.
Reference:
GitHub - Azure-Samples/active-directory-dotnet-webapi-manual-jwt-validation.
Azure Active Directory - Create Applications, Add Scopes And Add API Access (c-sharpcorner.com)
CodePudding user response:
The usual WindowsAzureActiveDirectoryBearerAuthentication middleware uses a metadata endpoint which is not supported by the v2.0 endpoint. Instead, this OpenIdConnectSecurityTokenProvider implementation can be used to fetch & use the OpenIdConnect metadata document - which for the v2 endpoint is https://login.microsoftonline.com/common/v2.0/.well-known/openid-configuration
app.UseOAuthBearerAuthentication(new OAuthBearerAuthenticationOptions
{
AccessTokenFormat = new JwtFormat(
new TokenValidationParameters
{
// Check if the audience is intended to be this application
ValidAudiences = new[] { clientId, "api://clientId" },
// Change below to 'true' if you want this Web API to accept tokens issued to one Azure AD tenant only (single-tenant)
// Note that this is a simplification for the quickstart here. You should validate the issuer. For details,
// see https://github.com/Azure-Samples/active-directory-dotnet-native-aspnetcore
ValidateIssuer = false,
},
new OpenIdConnectSecurityTokenProvider("https://login.microsoftonline.com/common/v2.0/.well-known/openid-configuration")
),
});