How can I create a file that only my application can modify? I need it because I have an app that creates a .txt file where user information is stored and I don't want the user to be able to modify it through File Explorer, but my App should be able to create it, modify it and delete it.
this is my code:
public void Write(List<Queue> Queue)
{
try
{
CreateFile();
using (FileStream Stream = new FileStream(Path, FileMode.Open))
{
using (StreamWriter file = new StreamWriter(Stream))
{
string Data = JsonSerializer.Serialize(Queue);
file.Write(Data);
file.Flush();
file.Close();
}
}
}
catch (IOException ex)
{
Log.GetInstance().Write(ex.Message);
}
public void CreateFile()
{
if (!FileExist)
{
File.Create(Path).Close();
}
}
public List<Queue> ReadFile()
{
try
{
if (FileExist)
{
using (StreamReader file = new StreamReader(Path))
{
string Data= file.ReadToEnd();
return JsonSerializer.Deserialize<List<Cola>>(Data);
}
}
}
catch (JsonException ex)
{
Log.GetInstance().Write(ex.Message);
}
catch (IOException ex)
{
Log.GetInstance().Write(ex.Message);
}
return null;
}
CodePudding user response:
You cannot as far as I know. Users and/or administrators will have access to that file either way. You can, however, detect modification by hashing the file and comparing the hash with the file
CodePudding user response:
How can I create a file that only my application can modify it?
You can't. Simple as that.
The thing is that administrators can access all files. And the user your running your app with. And hackers of course. ;) Typically you would just store application files in some well established locations, e.g. it is a de facto standard to put app files in /var/lib/myapp in unix systems. Of course other users will still be able to access those files, but that way you at least lower accidental modifications risk. However this also means that you should never store sensitive data locally.
Encryption is not really an option, because you have to store the encryption key somewhere, which just moves the pile from one place to another. It does make read/write a bit harder, but it doesn't really solve the issue. Unless you don't store the key anywhere, e.g. you manually provide it on application start or even better during runtime and you ensure it doesn't live too long. Depending on your usecase this may be a valid option.
Modification detection, i.e. hashing the file, has exactly the same issue: you have to store the hash somewhere. You only force the malicious user to modify two locations instead of one.
Note that using a database engine locally won't help at all. At the end of the day a database is just a fancy file, and you still need to store access keys somewhere.
All in all: if you are storing a non-sensitive data, then put it in application data folder and don't worry about it.
CodePudding user response:
You can encrypt the file to prevent tampering. Well at least any tampering will corrupt the file.
The CLR has a mechanism to encrypt data to a specific user without having to generate and store a key separately.This uses the 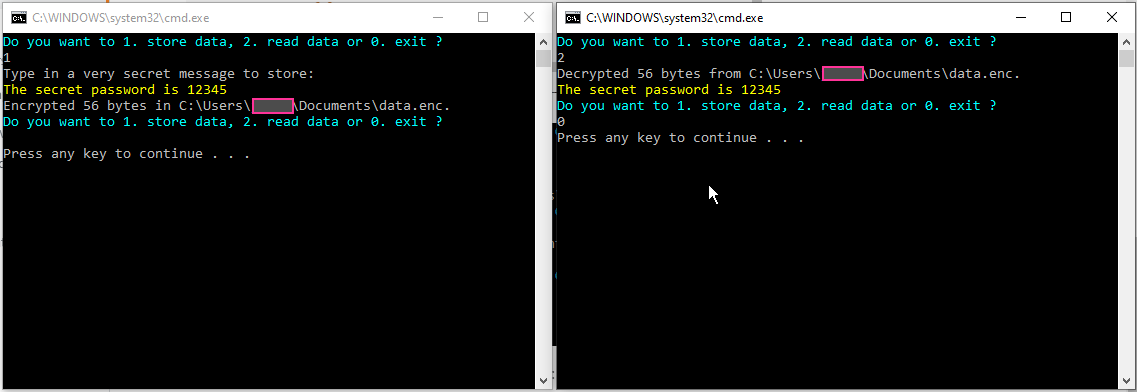
and the contents of data.enc are completely encryted: