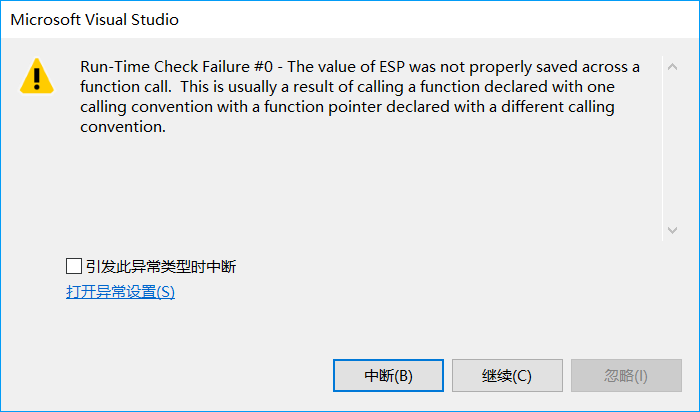
I want to intercept kernel32 ExitProcess function, and can be intercepted, throw an exception, but after interception system checked the seems to be function calls, the provisions of the changed many times still not,
After the DLL's code, it is a simple function
# pragma once
# # ifndef MYDLLAPI
# define MYDLLAPI extern "C" __declspec (dllimport)
# endif
MYDLLAPI void the Add (UINT T);
# include "stdafx. H"
# define MYDLLAPI extern "C" __declspec (dllimport)
# include "DLLLL. H"
Void the Add (UINT T) {
MessageBox (GetForegroundWindow (), TEXT (" HACKED!" ), TEXT (" what stuff? "), 1);
}
After the part is intercepted
#include
#include
#include
Typedef void * (T) (int);
PfnCurrent void ReplaceIATEntryInOneMod (PCSTR pszCalleeModName, T, T pfnNEW, HMODULE hmodCaller) {
PIMAGE_IMPORT_DESCRIPTOR pImportDesc=NULL;
ULONG ulSize;
PImportDesc=(PIMAGE_IMPORT_DESCRIPTOR) ImageDirectoryEntryToData (hmodCaller, TRUE, IMAGE_DIRECTORY_ENTRY_IMPORT, & amp; UlSize);
If (pImportDesc==NULL) {
return;
}
for (; PImportDesc - & gt; Name; PImportDesc++) {
PSTR pszModName=(PSTR) ((PBYTE) hmodCaller + pImportDesc - & gt; Name);
If (lstrcmpiA (pszModName, pszCalleeModName)==0) {
PIMAGE_THUNK_DATA pThunk=(PIMAGE_THUNK_DATA) ((PBYTE) hmodCaller + pImportDesc - & gt; FirstThunk);
for (; PThunk - & gt; U1. Function; PThunk++) {
T * PPFN=(T *) & amp; PThunk - & gt; U1. Function;
BOOL bFound=(* PPFN==pfnCurrent);
If (bFound) {
if (! WriteProcessMemory (GetCurrentProcess (), PPFN, & amp; PfnNEW, sizeof (pfnNEW), NULL) & amp; & (ERROR_NOACCESS==GetLastError ())) {
DWORD dwOldProtect;
If (VirtualProtect (PPFN, sizeof (pfnNEW), PAGE_WRITECOPY, & amp; DwOldProtect)) {
WriteProcessMemory (GetCurrentProcess (), PPFN, & amp; PfnNEW, sizeof (pfnNEW), NULL);
VirtualProtect (PPFN, sizeof (pfnNEW), dwOldProtect, & amp; DwOldProtect);
}
}
}
}
}
}
}
Int main () {
T pfnOrig=(T) GetProcAddress call (GetModuleHandle (TEXT (" Kernel32. DLL) "), "ExitProcess");
HMODULE hmodCaller=GetModuleHandle (TEXT (" ConsoleApplication2. Exe "));
If (hmodCaller==NULL) {
std::cout <& lt; "NO B354" & lt; & lt; GetLastError ();
}
HMODULE Module;
The Module=LoadLibrary (TEXT (" E: \ \ QTC \ \ DLLLL \ \ Debug \ \ DLLLL DLL "));
If (Module==NULL) {
std::cout <& lt; "NO B3" & lt; & lt; GetLastError ();
}
T FA;
FA=(T) GetProcAddress call (Module, "Add");
If (FA==NULL) {
std::cout <& lt; "NO ADD" & lt; & lt; GetLastError ();
}
ReplaceIATEntryInOneMod (" kernel32. DLL, "pfnOrig, FA, hmodCaller);
ExitProcess (0);
//STD: : cout & lt; & lt; "CONTINUE" & lt; & lt; std::endl;
//Sleep (INFINITE);
}
CodePudding user response:
River's lake emergency...CodePudding user response:
System containing 360 (or other anti-virus software), you can't have running this code is successful, all antivirus software is running ahead of schedule, all the DLL hook up ahead of time, you will jump to the somebody else's hook with the code, antivirus software security mechanism will judgment call is legal, you this kind of hook, illegal directly by antivirus software, direct refused, even if you turn off the anti-virus software, code test is successful, also only for your own code starts, call system is the kernel of the app, you can guarantee the somebody else computer or server is not 360!Suggest don't do this, there is no meaning,
