In our environment Windows machines are domain joined, and Azure AD Connect Sync is used to connect the domain to Azure AD. My goal to authenticate in Azure using the context of the currently logged in user.
As I understand, I need to use Integrated Windows authentication (IWA) among the 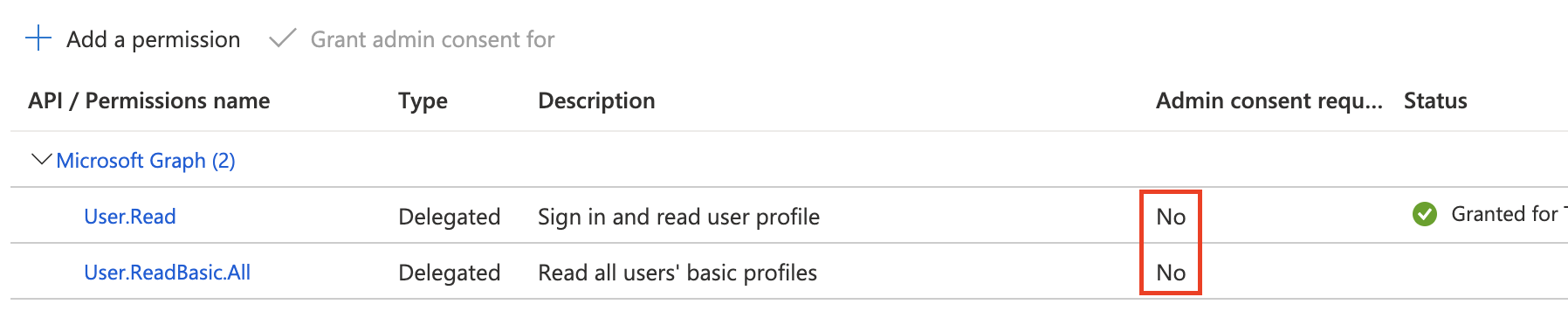
I am not a tenant admin, but I assume "Grant admin consent for ..." button is greyed because there is nothing to grant (it turns active once I add something).
Nevertheless I copied TenantId and app ClientId into the example and tried to run it. It is failing with the following error:
AADSTS65001: The user or administrator has not consented to use the application with ID 'b5e9bd68-5326-44ff-9fc6-c933227708ff' named 'foo-bar'. Send an interactive authorization request for this user and resource. Trace ID: 77c69007-80cb-4eb2-b60b-f029928c5f00 Correlation ID: 63be7460-11e6-49b2-88b9-a3b56025ee43 Timestamp: 2022-06-27 23:08:08Z
Again, what an interactive request? Isn't the purpose of this example to illustrate how I can authenticate silently and transparently for the user, without any interaction?
Please help me to find missing pieces.
CodePudding user response:
IWA is a silent flow that doesn't need user interaction, you must grant consent to all users in the tenant to use the application.
To perform the above action, you must have the tenant admin role as mentioned in the MsDoc.
When that role is enabled, make sure to Grant Admin Consent like below after adding the required API permissions.
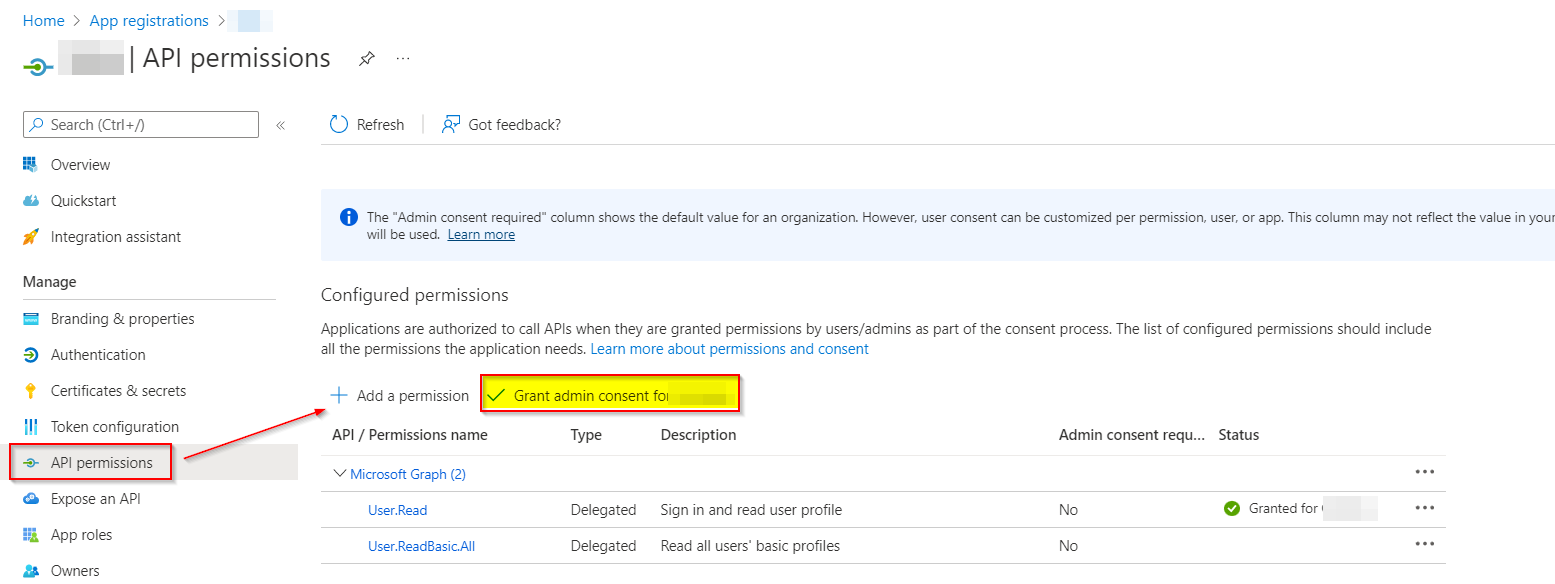
You can also make use of below admin consent endpoint that will give consent form like below:
https://login.microsoftonline.com/{your_tenant_id}/v2.0/adminconsent?
&client_id=Your_client_id
&state=12345
&redirect_uri=Your_redirect_uri
&scope= https://graph.microsoft.com/.default
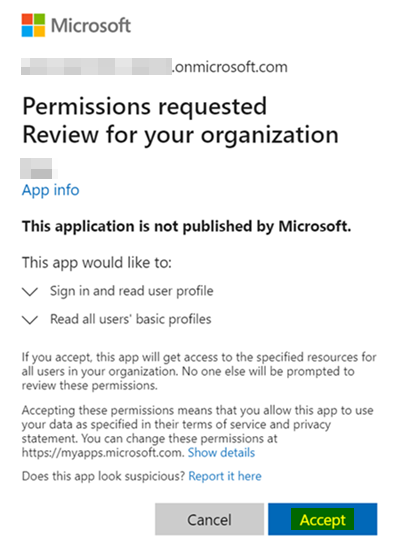
After accepting the above consent, you can get rid of "The user or administrator has not consented to use the application" error.
