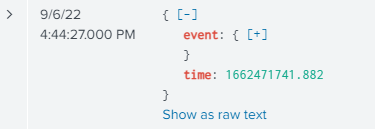
Serilog with Splunk sink writes events in nested structure. It wraps my logged parameters into "events" object. While watching logs on Splunk every time I have to press on " " to expand properties that are actually useful for me. It slows down process of analyzing logs significantly.
Example of how logs are shown:
Is there a way to affect the structure sent to Splunk, like brining everything in "event" one level up? Or maybe there's some setting which could help in Splunk itself?
CodePudding user response:
This appears to be JSON structured data with an 'event' and 'time' field, which is awfully reminiscent of the structure that is used by the 'event' endpoint version of the HTTP Event Collector in Splunk.
Could it be that Serilog is sending to hxxps://yourhechost:port/services/collector/raw when it should be sending to hxxps://yourhechost:port/services/collector/event instead?
CodePudding user response:
added this to your search might help you manually look though the logs
|spath event
|spath input=event (this part is optional)
|table event