It seems that the common practice is to send JWTs in the Authorization header and preceded by the "Bearer " string.
Why is this done this way, and why not simply send the token in the body of a post request? Is there a convenient way to verify the token in node when it's sent in the header?
CodePudding user response:
JWT bearer tokens contain sensitive information, because they allow anyone bearing the token to impersonate you. It thus makes sense to treat them with special caution and, for example, not write them into server logs, or not allow them in cross-origin requests.
But such special treatment is possible only if all involved parties know which parts of a request contain sensitive information. If the token was just part of the payload, only the sending client and the receiving application might know, but intermediate parties like proxies, server frameworks or browers would not. By contrast, everyone knows that the Authorization header always contains sensitive information. And for example, browsers will not make cross-origin requests with an Authorization header, unless a prior 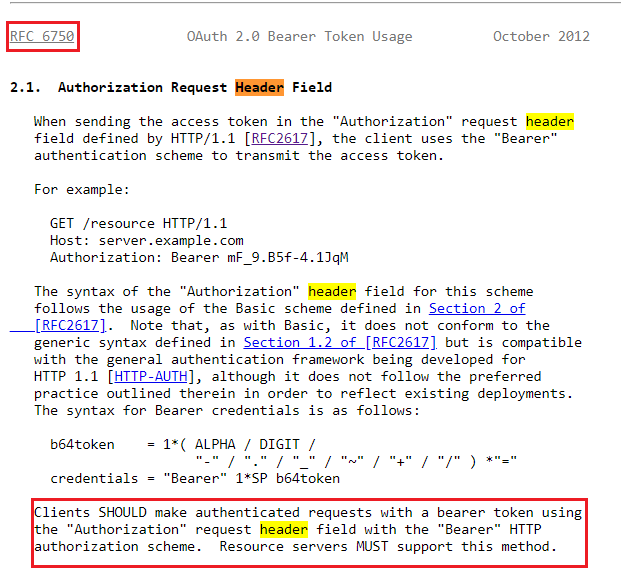
text version
2.1. Authorization Request Header Field
When sending the access token in the "Authorization" request header
field defined by HTTP/1.1 [RFC2617], the client uses the "Bearer"
authentication scheme to transmit the access token.
For example:
GET /resource HTTP/1.1
Host: server.example.com
Authorization: Bearer mF_9.B5f-4.1JqM
The syntax of the "Authorization" header field for this scheme
follows the usage of the Basic scheme defined in Section 2 of
[RFC2617]. Note that, as with Basic, it does not conform to the
generic syntax defined in Section 1.2 of [RFC2617] but is compatible
with the general authentication framework being developed for
HTTP 1.1 [HTTP-AUTH], although it does not follow the preferred
practice outlined therein in order to reflect existing deployments.
The syntax for Bearer credentials is as follows:
b64token = 1*( ALPHA / DIGIT /
"-" / "." / "_" / "~" / " " / "/" ) *"="
credentials = "Bearer" 1*SP b64token
Clients SHOULD make authenticated requests with a bearer token using
the "Authorization" request header field with the "Bearer" HTTP
authorization scheme. Resource servers MUST support this method.
Token types are Basic & Digest also use as Bearer
This guide easy to understand Token concept.
