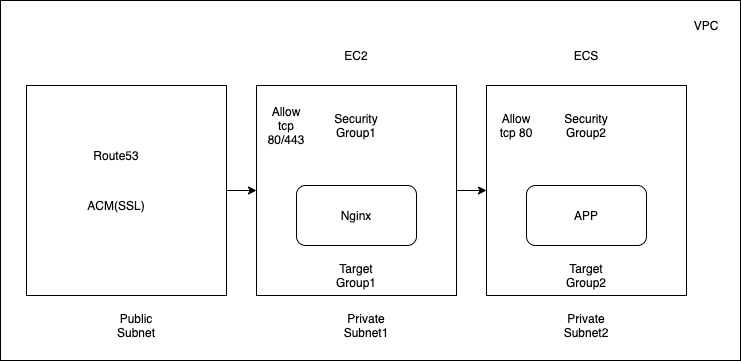
As the picture below, an EC2 and an ECS services are running on different subnet, target group and security groups. But they are in the same VPC.
I want to allow access the ECS service through EC2's Nginx server from public internet.
EC2 is allowing 80 and 443 now. And the ECS' security group is allowing 80 only. The Nginx's config is
/etc/nginx/sites-enabled/nginx.conf
server {
listen 80 default_server;
server_name _;
proxy_pass {{ internal_ecs_elb_endpoint }};
proxy_read_timeout 60s;
proxy_redirect {{ internal_ecs_elb_endpoint }} myproxy.mydomain.com;
return 301 https://$host$request_uri;
}
Does the security group2 in ECS service need to allow security group1's tcp 80/443 port? As they are in the different groups.
CodePudding user response:
Does the security group2 in ECS service need to allow security group1's tcp 80/443 port?
Yes. To follow good practice you would create inbound tcp rule for port 80 in SG2 with source of SG1.