I have the following setup
- A single VPC
- 2 Public subnets across 2 AZ (containing AWS Beanstalk app with exposes an api)
- 2 Private subnets across 2 AZ (containing Lambda function)
- 1 Interface VPC Endpoint for Elastic beanstalk (Service name com.amazonaws.us-east-2.elasticbeanstalk)
Instead of creating a NAT gateway for my lambda function to be able to access the AWS Beanstalk app apis over the internet , i want to create a VPC endpoint so that i can access aws beanstalk within AWS internal network from my lambda function.
The public subnet has security groups that allow web traffic (port 80/443)
The VPC endpoint is associated with the private subnets and its security groups allow web traffic traffic(Port 80/443).
The lambda function is also associated with the private subnets and its security groups allow web traffic traffic(Port 80/443).
DNS resolution and DNS hostnames are enabled at VPC level.
I copied the Endpoint dns name to form the url that is being called by the lambda function and i get a timeout
Even after i tried all steps above, AWS Lambda cannot access the beanstalk app api.
Simplified lambda function:
def lambda_handler(event, context):
http = urllib3.PoolManager()
r = http.request('GET', 'http://vpce-**********.elasticbeanstalk.us-east-2.vpce.amazonaws.com/')
print(r.data)
# TODO implement
return {
'statusCode': 200,
'body': json.dumps('Hello from Lambda!')
}
The Elastic beanstalk app is available over the internet at http://sample-app-dev.******.us-east-2.elasticbeanstalk.com/
What am i missing here?
CodePudding user response:
If I understand correctly, you managed to create a VPC Endpoint which will let you access the Elastic Beanstalk AWS Service (where you can do administration for your EB instances). You did not expose your application itself deployed using Elastic Beanstalk.
I'm saying this, because in order to expose your EB application from a VPC, first you have to create an 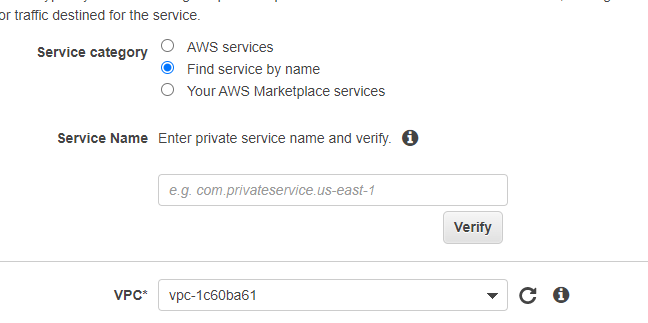
If you found your service, you can place and Endpoint into your consumer VPC to which you can connect.
Nevertheless, if both of your VPCs are in the same AWS account, having exposing a service through PrivateLink might be overkill. Probably a 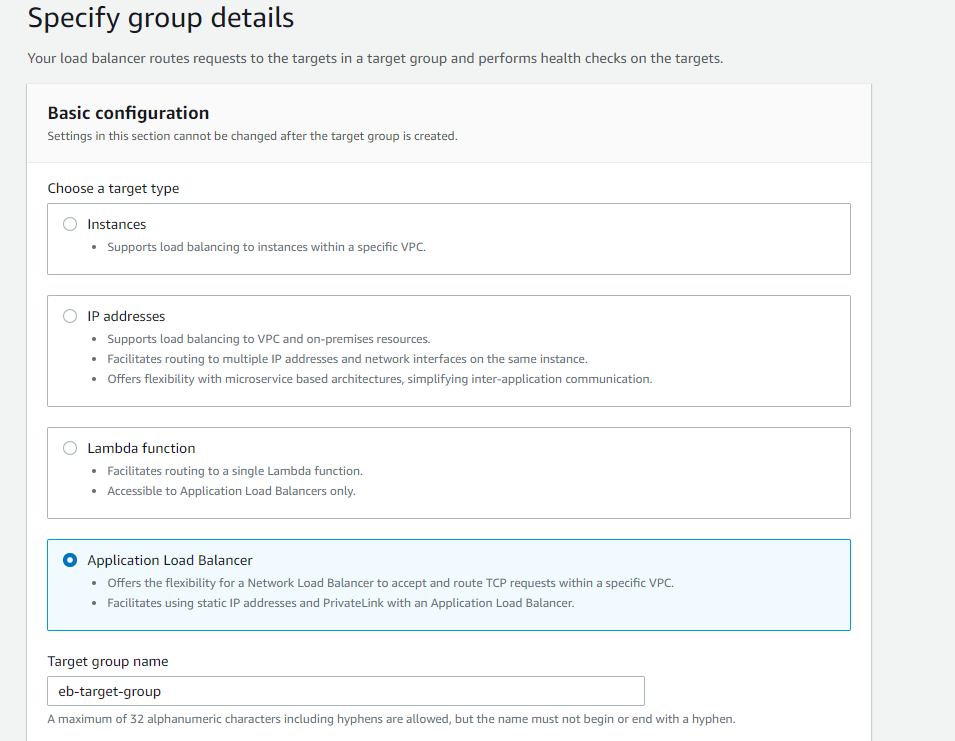
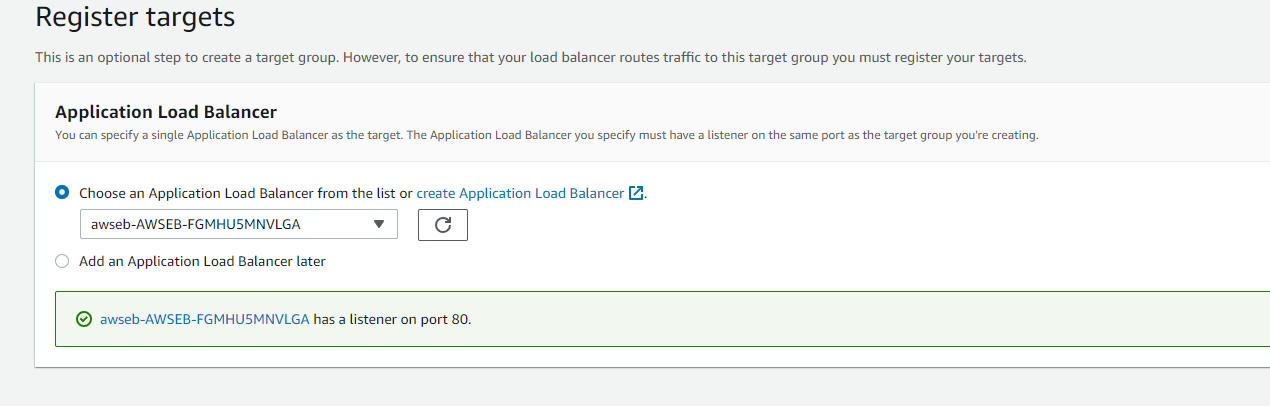
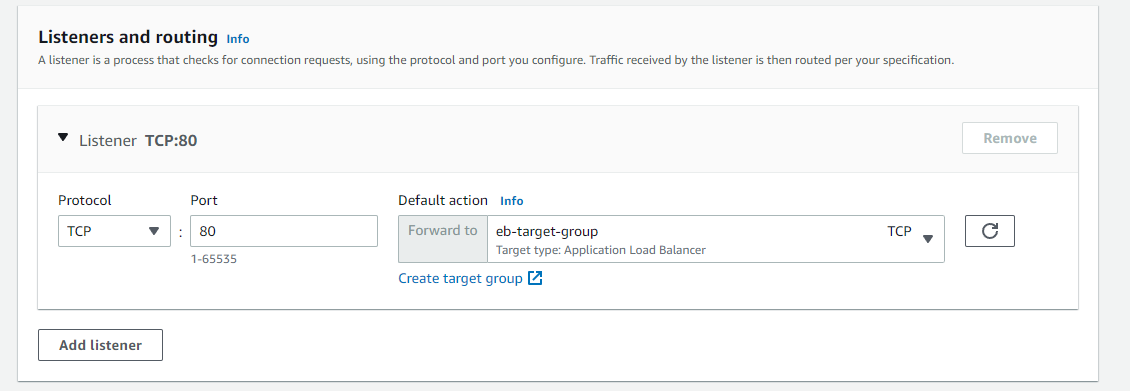
- Register the load balancer from the EB application to the target group.
- Make sure you select the Target Group created before for the network load balancer.
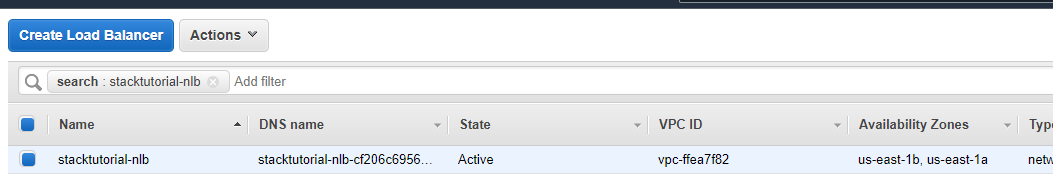
- Wait until the load balancer provisions. It should be in the
activestate.
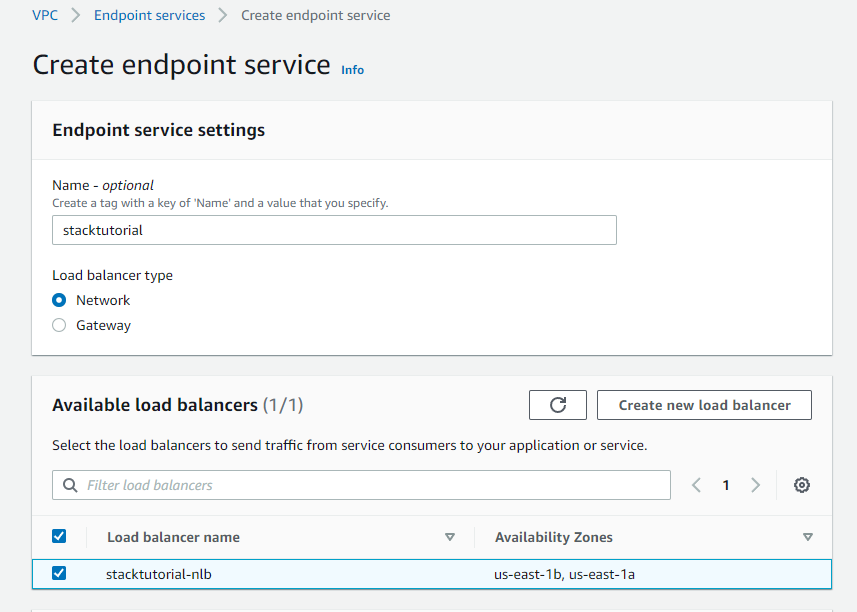
- Go to
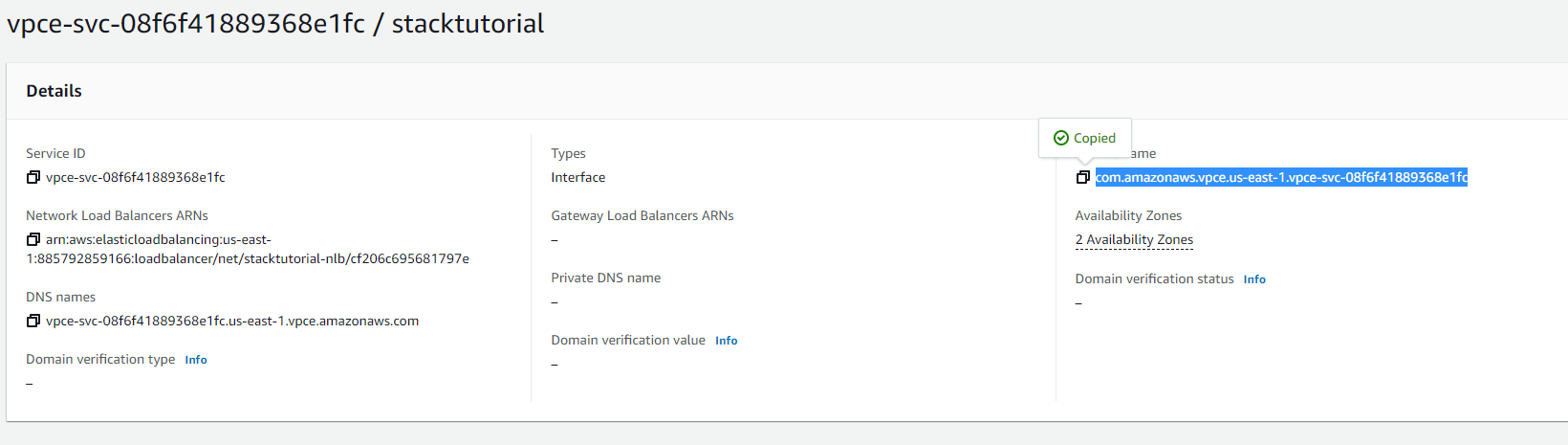
VPC->Endpoint Serviceand create a newEndpoint Service(PrivateLink). You will have to give the name of the load balancer here:
- Grab the Endpoint Service name:
- Go to
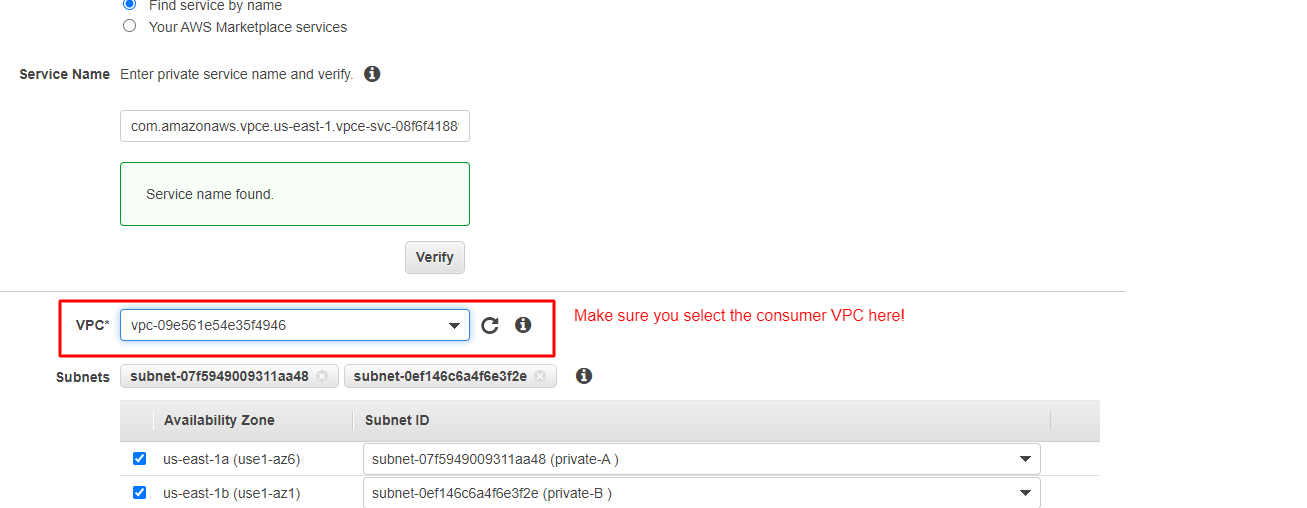
Endpointsand search for the endpoint name:
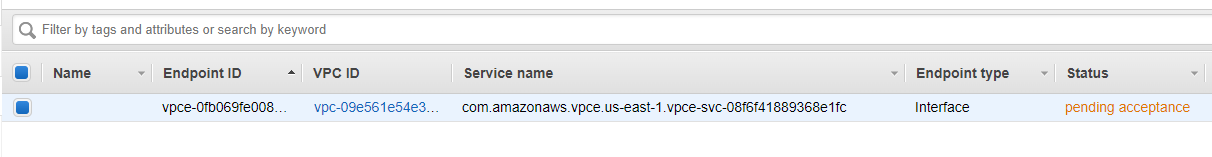
- Create the
Endpoints:
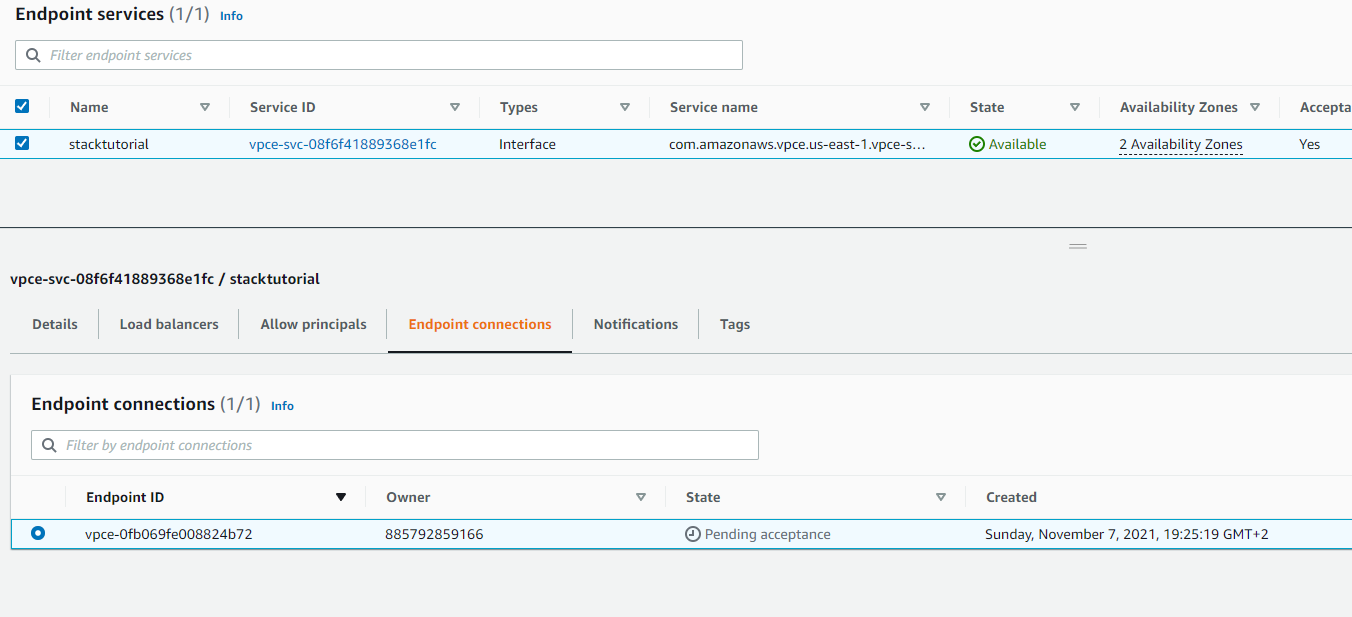
It might require acceptance, so go back to the Endpoint Service and accept the request.
This should also go from pending to available.
- At this point you should be able to access the EB application using the DNS from the
Endpoint.