My resource groups has an environment tag where only specific values are allowed: "dev,test,prod". I want to enforce that with an Azure Policy which will deny all the resource group creation which doesn't have one of this "dev,test,prod" values in their environment tag. My policy code is as below:
{
"properties": {
"displayName": "Allowed tag values for Resource Groups",
"description": "This policy enables you to restrict the tag values for Resource Groups.",
"policyType": "Custom",
"mode": "Indexed",
"metadata": {
"version": "1.0.0",
"category": "Tags"
},
"parameters": {
"allowedTagValues": {
"type": "array",
"metadata": {
"description": "The list of tag values that can be specified when deploying resource groups",
"displayName": "Allowed tag values"
},
"defaultValue": [
"dev","test","prod"
]
}
},
"policyRule": {
"if": {
"allOf": [
{
"field": "type",
"equals": "Microsoft.Resources/subscriptions/resourceGroups"
},
{
"field": "tags[environment]",
"notIn": "[parameters('allowedTagValues')]"
}
]
},
"then": {
"effect": "deny"
}
}
},
"id": "/providers/Microsoft.Authorization/policyDefinitions/xxxxxxx-xxxxxxx-xxxxxxxxxx-xxxxxxx",
"name": "xxxxxxx-xxxxxxx-xxxxxxxxxx-xxxxxxx"
}
This doesn't have any effect at all. I have tried this as well:
{
"not": {
"field": "tags[environment]",
"in": "[parameters('allowedTagValues')]"
}
}
Neither this does work.
Any suggestion?
CodePudding user response:
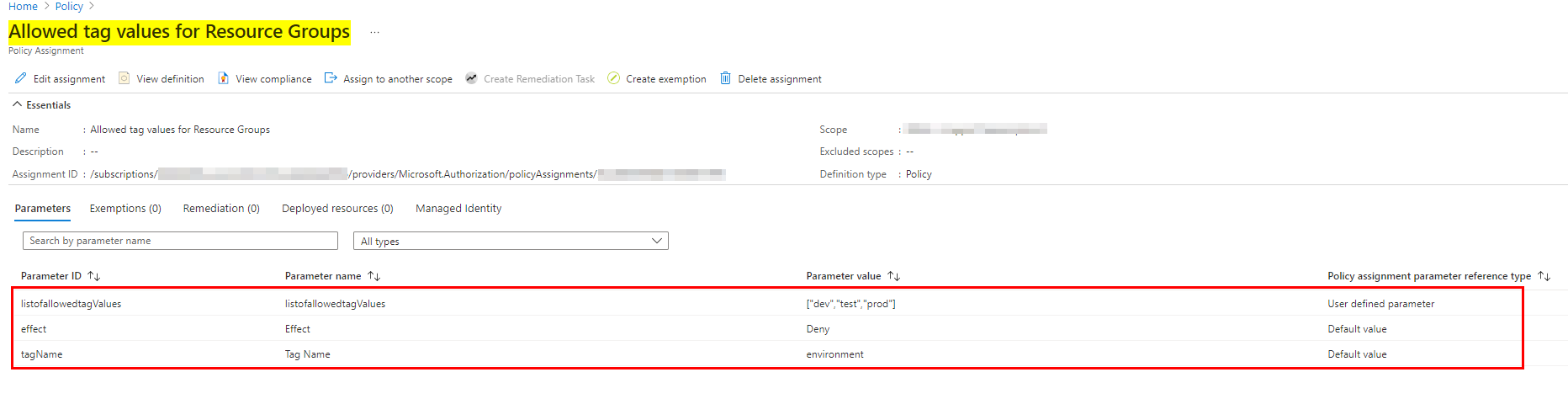
You need to pass the tag values "dev","test","prod" as allowed values for the parameter listofallowedTags as shown below.
Based on your requirement we have created the below policy definition. we have tested this in our local environment which is working fine.
{
"mode": "All",
"policyRule": {
"if": {
"allOf": [
{
"field": "type",
"equals": "Microsoft.Resources/subscriptions/resourceGroups"
},
{
"not": {
"field": "[concat('tags[', parameters('tagName'), ']')]",
"in": "[parameters('listofallowedtagValues')]"
}
}
]
},
"then": {
"effect": "[parameters('effect')]"
}
},
"parameters": {
"effect": {
"type": "String",
"metadata": {
"displayName": "Effect",
"description": "Enable or disable the execution of the audit policy"
},
"allowedValues": [
"Audit",
"Deny",
"Disabled"
],
"defaultValue": "Deny"
},
"tagName": {
"type": "String",
"metadata": {
"displayName": "Tag Name",
"description": "Name of the tag, such as 'environment'"
},
"defaultValue": "environment"
},
"listofallowedtagValues": {
"type": "Array",
"metadata": {
"displayName": "Tag Values",
"description": "Value of the tag, such as 'production'"
},
"allowedValues": [
"dev",
"test",
"prod"
]
}
}
}
Note: As you can see from the below image, the custom policy has been assigned to subscription.
Here are the some sample outputs for reference:
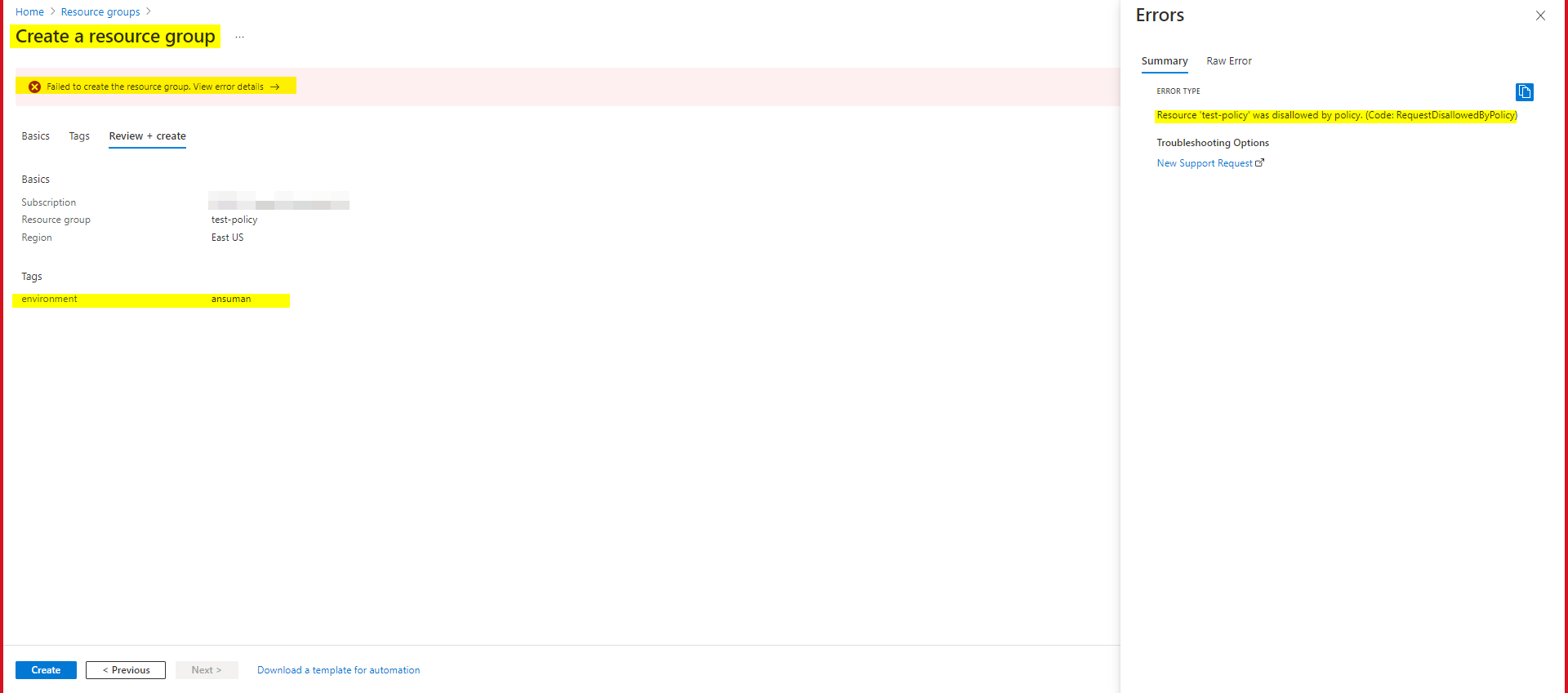
- In the below example, we have passed environment tag a different value apart from those 3 values defined in
listofallowedtagValuesparameter & while deploying the resource group it got failed since it doesn't met policy requirement.
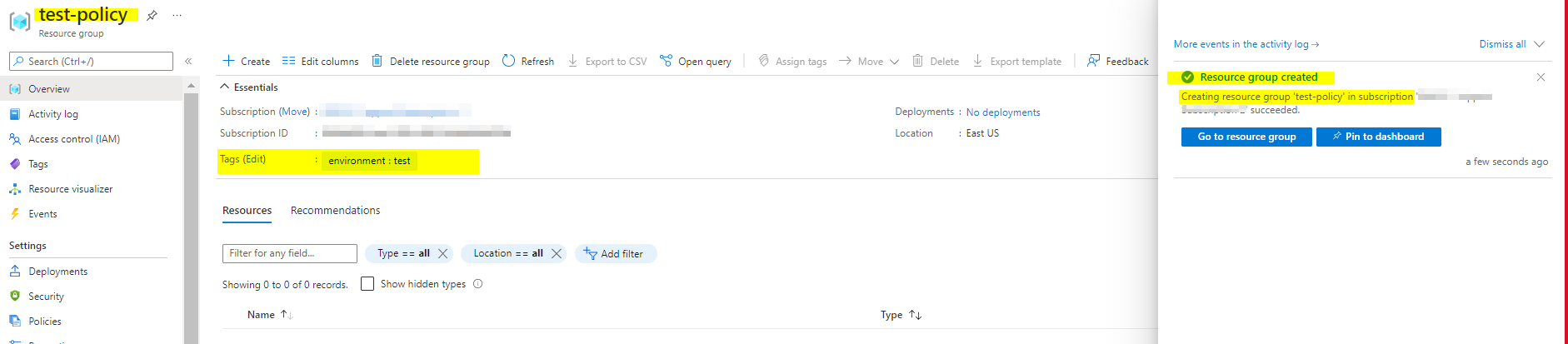
- In the below example, we have passed environment tag value as
testresource group deployment got succeeded as it met the policy requirements.