We have a federation between with our ADFS and the other company Azure AD using the "Claim Provider Trusts". We use the Azure AD to perform the authentication, but our ADFS/AD is sending some claims to our "Relying Party Trusts".
The problem I'm facing is if a user is disabled/expired in our local AD, it is still possible to authenticate and access the applications, because the user is not disabled/expired in the Azure AD. I can't manage the Azure AD and it is a valid situation where the user is disabled/expired in our AD, but still working on the Azure AD.
How can I figure this out to prevent disabled/expired user from my local AD to access my apps?
Thanks!
CodePudding user response:
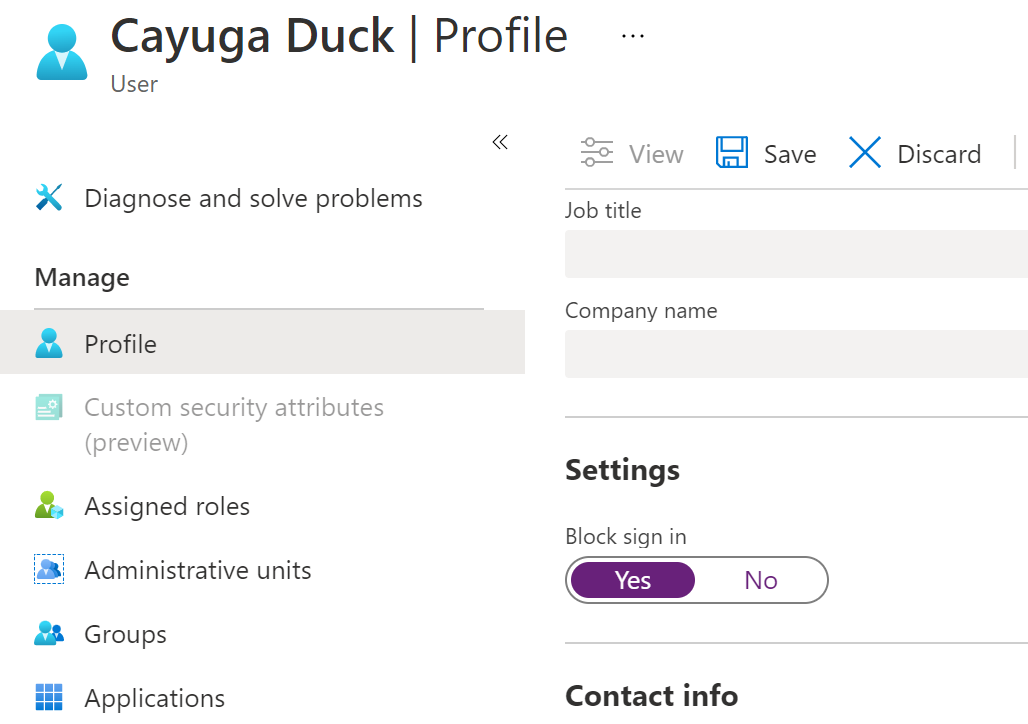
In Azure AD you need to go to the user's profile and block the user's sign in under the user's profile > Edit > Settings
You do need to have at least the User Administrator role in Azure, so if you don't have access to the Azure AD you will need to ask an admin to do this.
You can also use Graph API to set accountEnabled to false.
PATCH https://graph.windows.net/myorganization/users/{user_id}?api-version
Body:
{
"accountEnabled": false
}
Otherwise you can delete the user in Azure or ask the admin to do that.
CodePudding user response:
For federation, the user should either be in your AD or in the other parties AAD.
(If you use AAD Connect, the user status is synched up to a shadow account).
Otherwise, you end up with this problem.
Is there a reason you have them in both?
Is there a way to match the AAD and the AD user?
If so, you can have a claims rule to get the status of the matching AD user and then deny access if disabled.