Overview
We have an Azure AD secured API living in Azure as a web app. We need to be able to:
- Trigger this API via user interaction from a client application (this part works).
- Trigger this API programmatically from a scheduled job that will simply get a token & hit this API (this part does not work due to authentication issues).
Problem
The issue is that when we request a token from Azure AD, scope is not being set in our token claims resulting in the API rejecting the token.
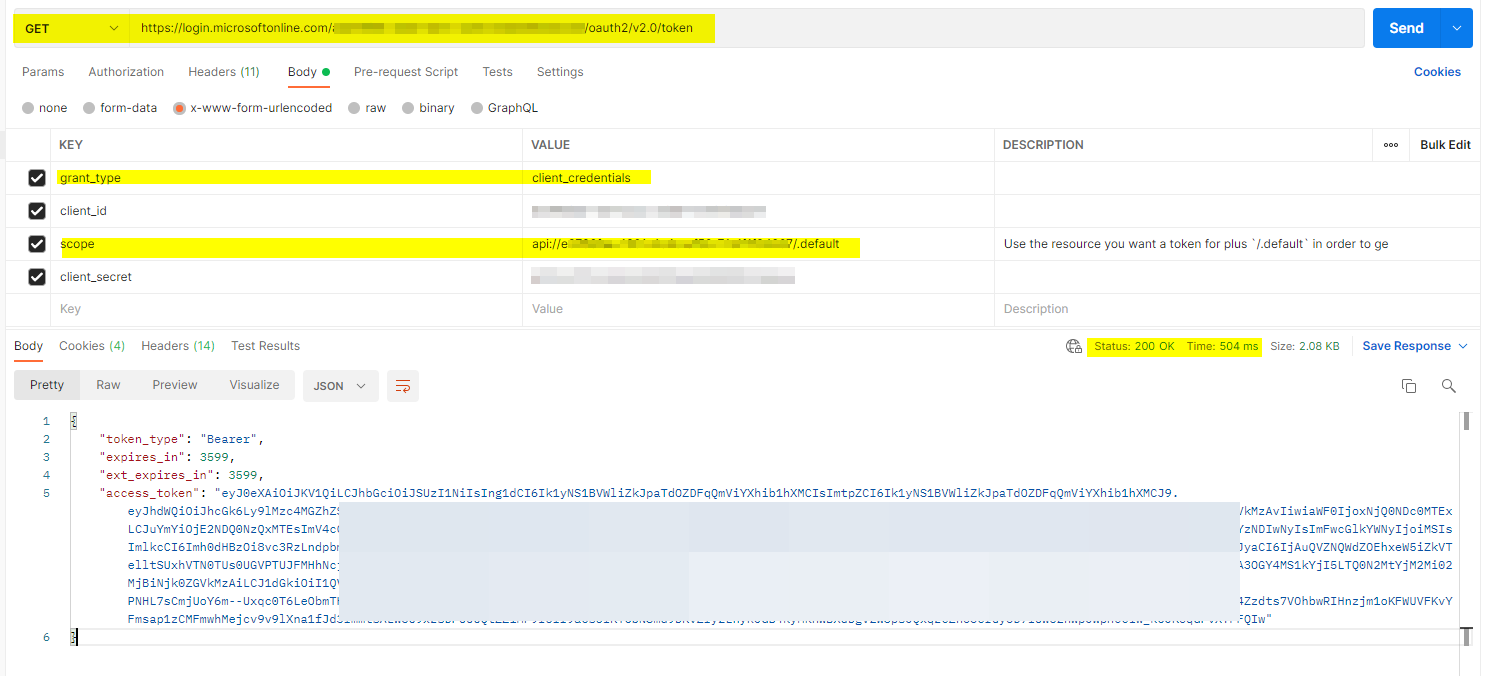
This is the request we are making:
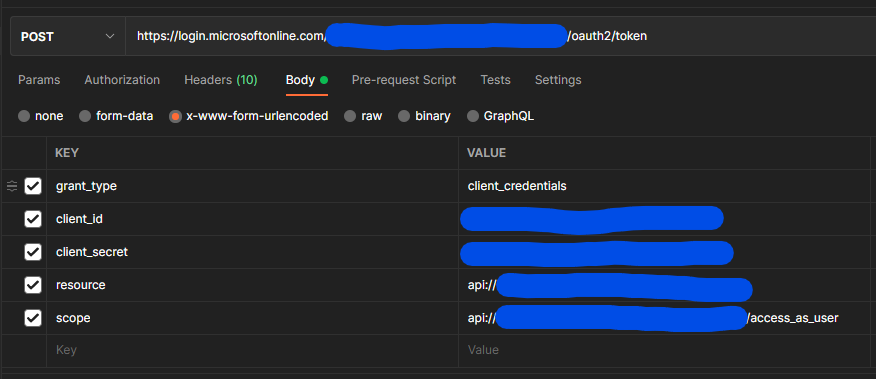
This request returns an access token with the following claims:
{
"aud": "<our api client id>",
"iss": "https://login.microsoftonline.com/<tenantId>/v2.0",
"iat": 1644421512,
"nbf": 1644421512,
"exp": 1644425412,
"aio": "<value>",
"azp": "<scheduled job client id>",
"azpacr": "1",
"oid": "<guid>",
"rh": "<value>",
"sub": "<guid>",
"tid": "<guid>",
"uti": "<value>",
"ver": "2.0"
}
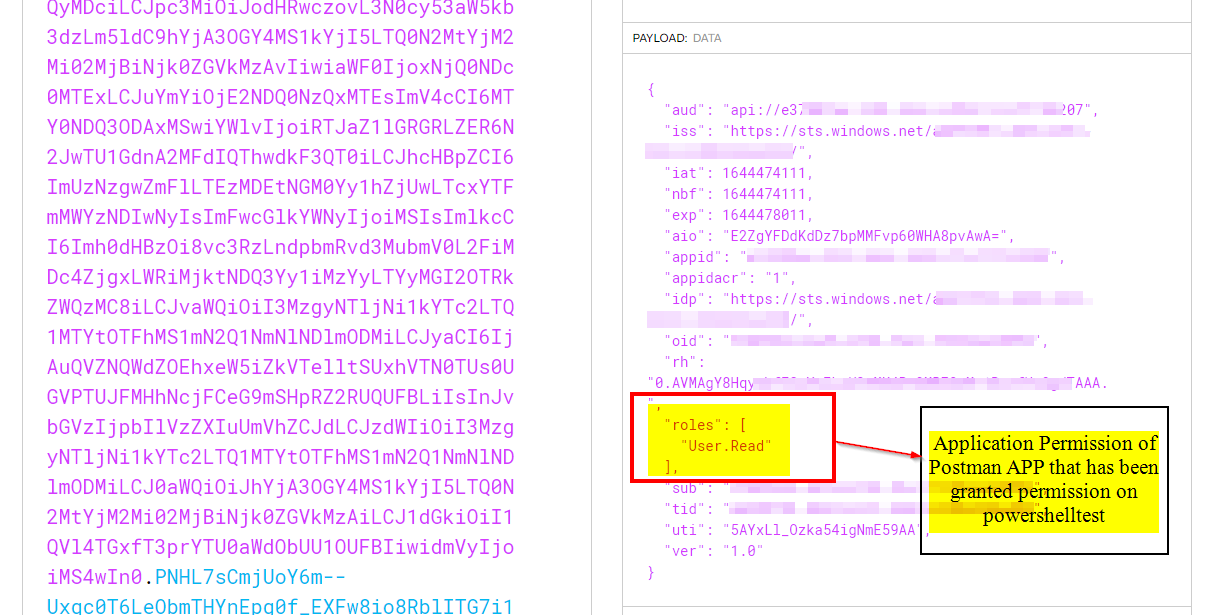
As you can see scp (scope) is not included in the token claims even though we include it in the request.
If we use this token to make a request to our API we get the following error:
System.UnauthorizedAccessException: IDW10201: Neither scope or roles claim was found in the bearer token.
Any help on how we can get an access token from Azure AD with the proper scope/permissions to call our API, would be greatly appreciated.
Note
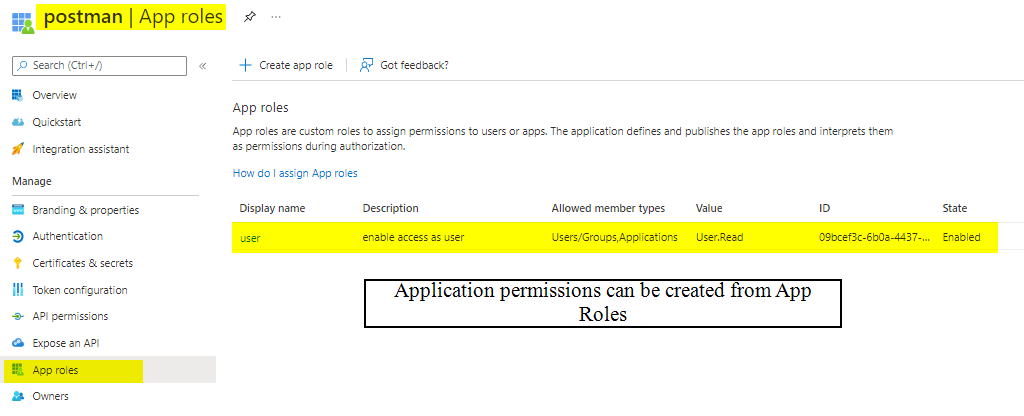
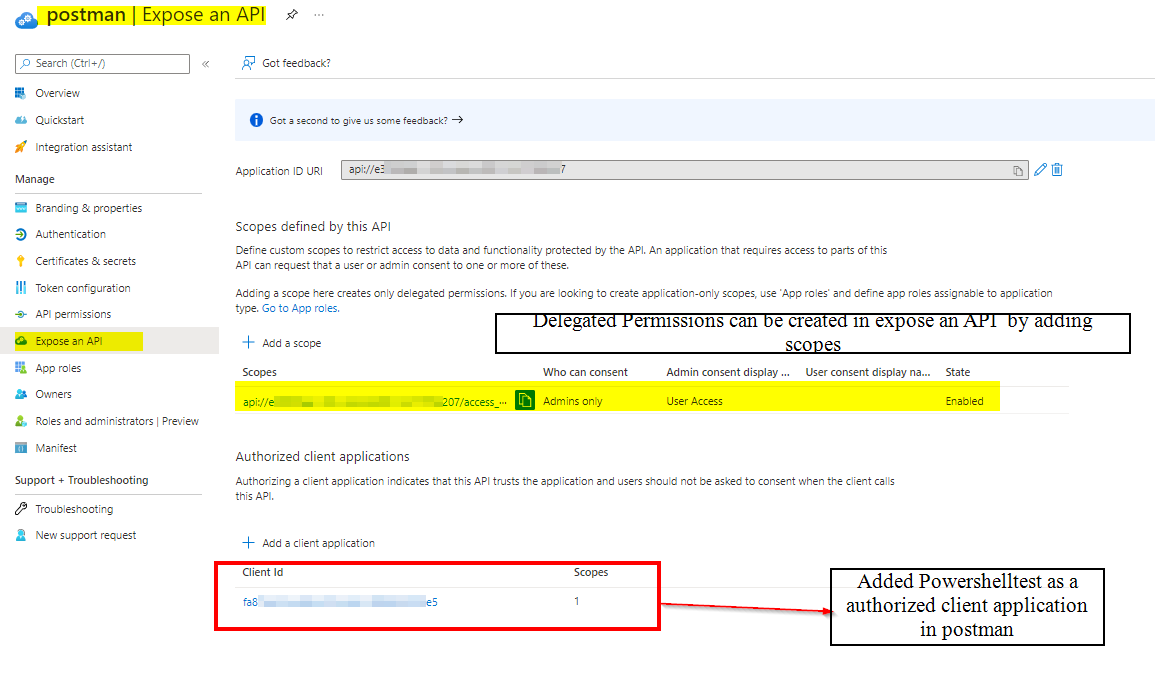
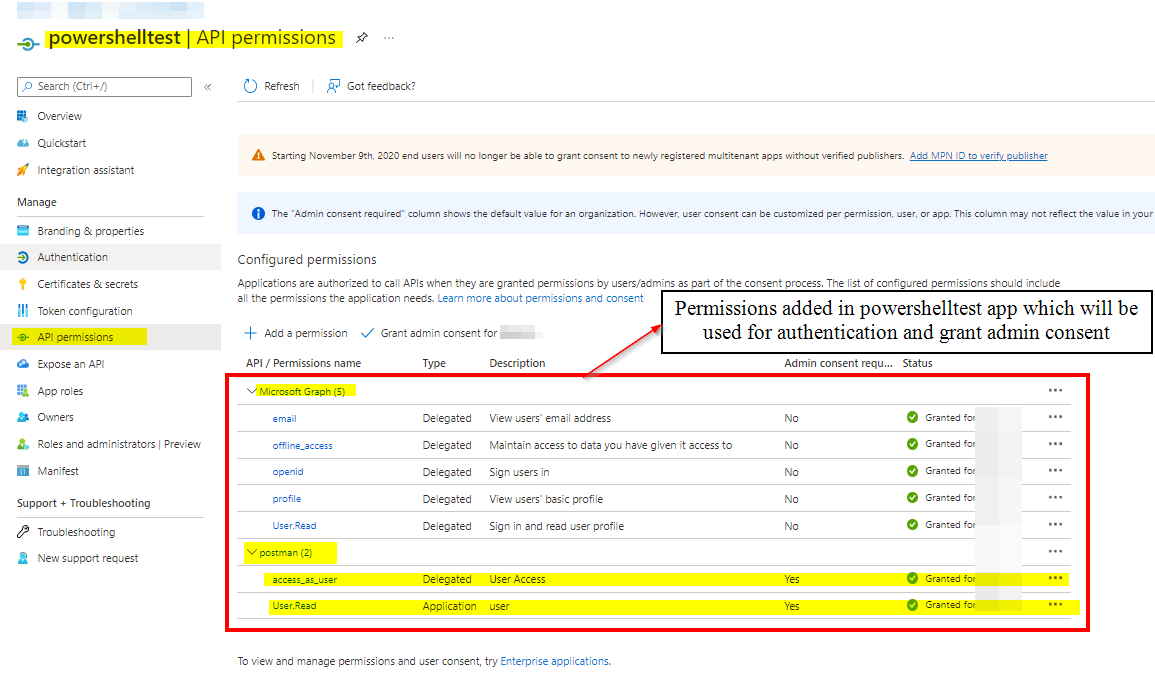
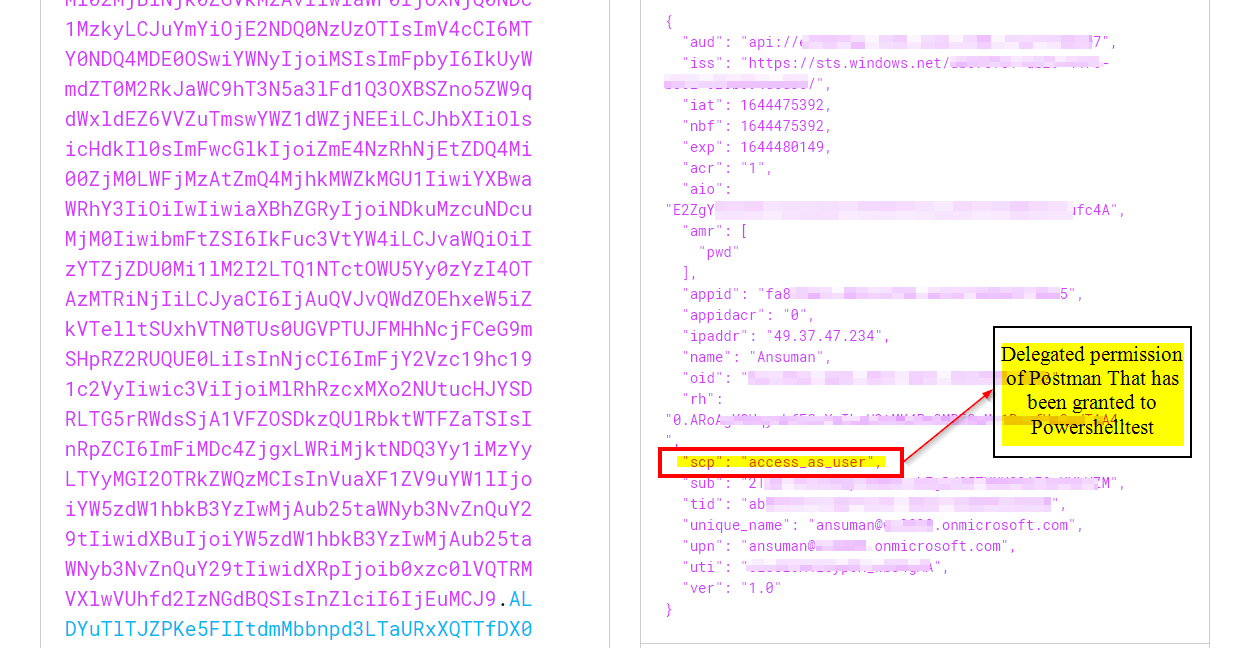
The Azure AD App Registration for our scheduled job that will request a token and then hit our API, does have the Delegated API Permission access_as_user which you can see I am including in the token request's scope.
CodePudding user response:
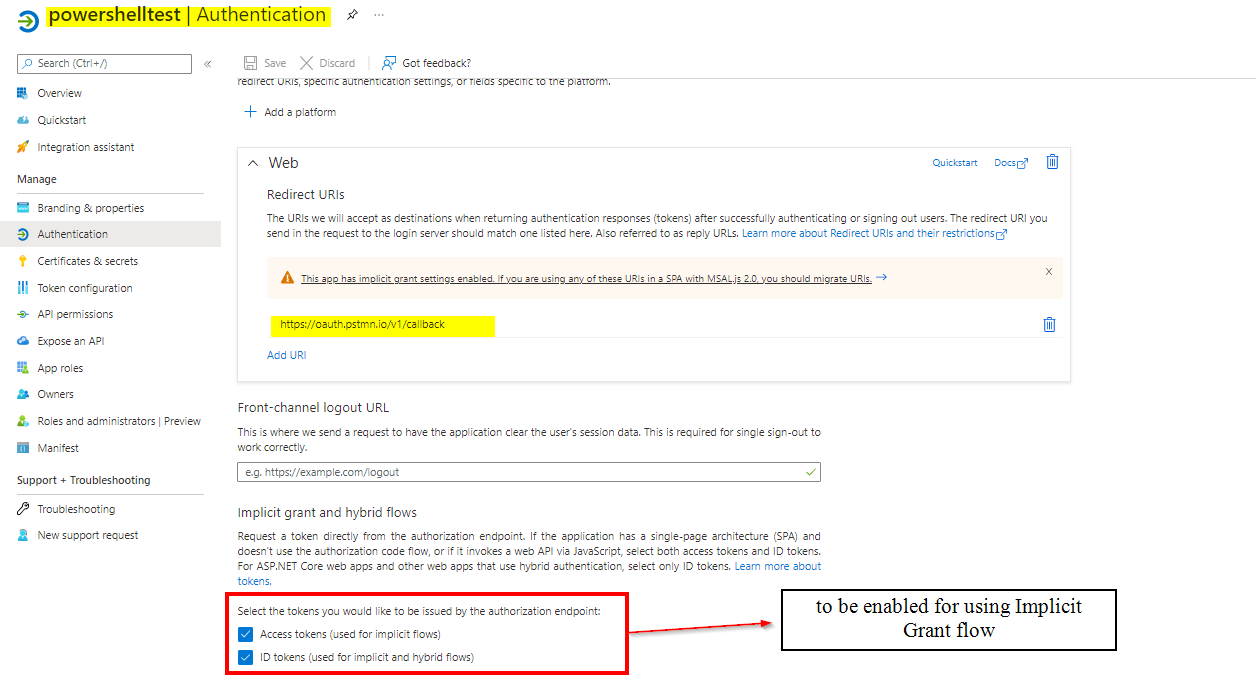
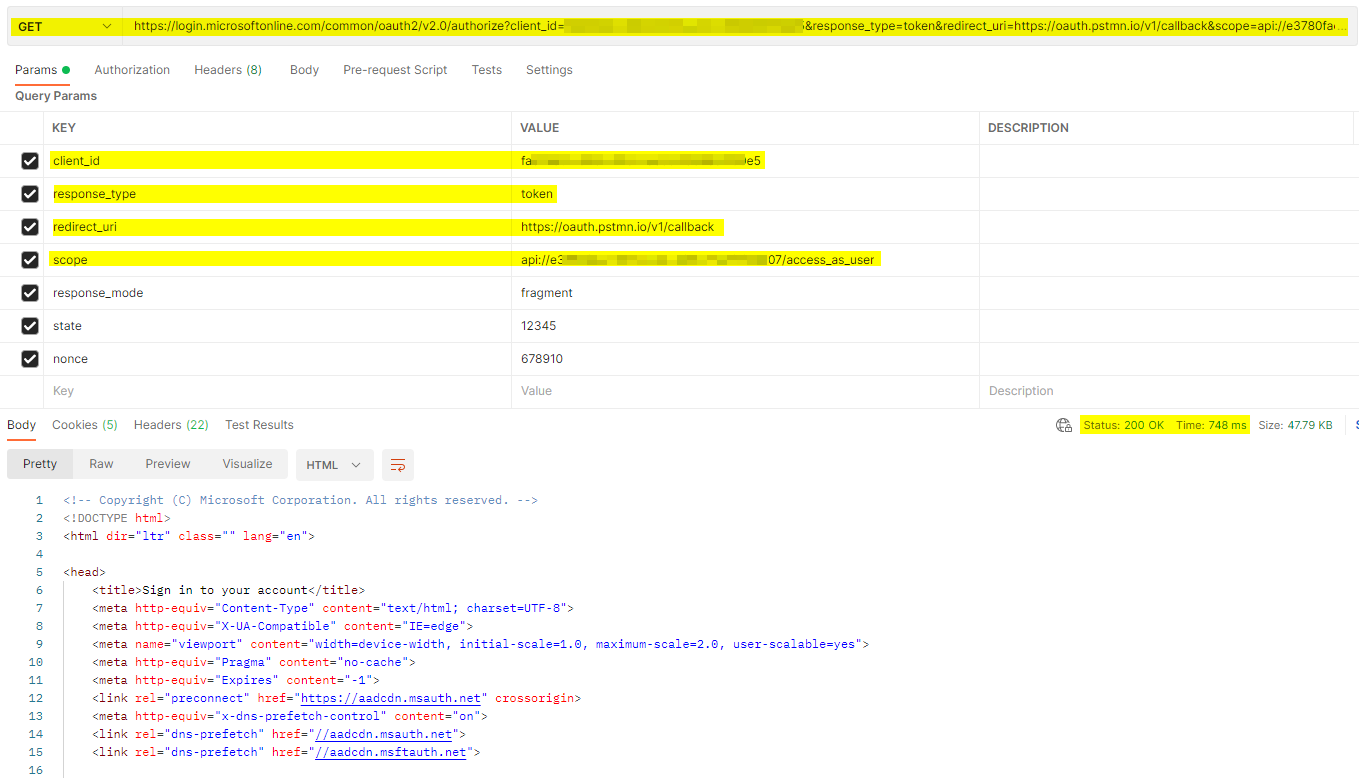
The above is expected as using client credentials you can't get the delegated permissions i.e. the access_as_user permission and also the scope in client credentials should be used as api://<APP_ID>/.default . So , If you want delegated permissions then you will have to use implicit grant flow instead of client credentials.
For testing , I created two app registrations , One on which API is exposed (Postman) and other which is to be used for authentication (Powershelltest) and then , I have tested the same in 2 different scenarios like one for client credentials and another for implicit grant :
Main APP whose API has been exposed :
App used for authentication:
Scenario 1 Using Client Credential flow :
Scenario 2 using Implicit Grant flow :