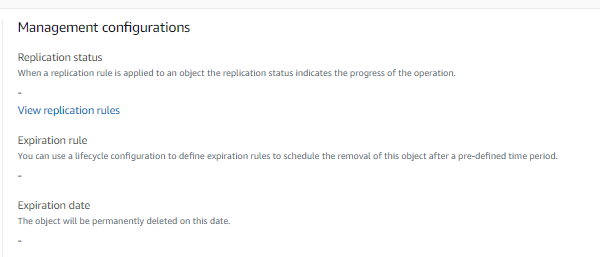
I created a S3 Lifecycle rule to delete expired objects. Then, I uploaded a S3 object using unsigned request aws cli aws s3 cp hello-unsigned.txt s3://bucket/ --no-signed-request --endpoint-url https://bucket.s3-vpce_dns/. The unsigned object was uploaded successfully, but didn't be applied Lifecycle rule. There is nothing in expiration rule and expiration date in S3 Object Management configurations block.
I uploaded another S3 object using signed request aws s3 cp hello-signed.txt s3://bucket/ --endpoint-url https://bucket.s3-vpce/. This signed object was applied Lifecycle rule successfully.
So, I guess the unsigned request is the reason why the S3 object isn't be applied Lifecycle rule.
I have few questions,
- Do I guess right?
- Is this a bug or normal behavior about unsigned S3 object?
- If I'm right, How do I apply Lifecycle rule to unsigned request s3 objects
CodePudding user response:
The most likely reason for not being able to perform certain operations on S3 objects is that you do not actually own the S3 objects. Objects can be uploaded by other accounts or by unauthenticated users and if you have not explicitly done something to ensure that you, as bucket owner, take full control of those objects then they continue to be owned by that other party, even though they reside in your bucket.
Good options to ensure you own the objects in your bucket are:
- configure bucket owner enforced
- your bucket policy can require bucket-owner-full-control
Note that bucket owner enforced is now a best practice for S3 buckets but be aware that it will disable legacy ACLs for that bucket, potentially causing you to have to apply a bucket policy e.g. if you want to make certain objects public and they were previously made public by ACL.