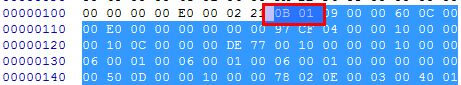
 the NT optional header in the file of the head offset 0 x108, according to the offset
the NT optional header in the file of the head offset 0 x108, according to the offset 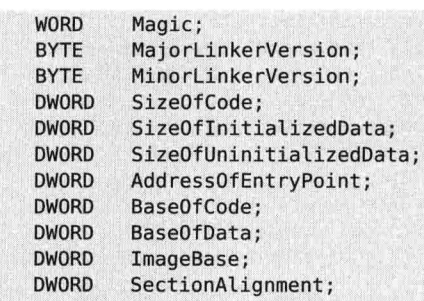 imagebase file offset 0 x124
imagebase file offset 0 x124 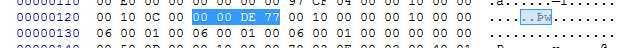 value of x77de0000 [0] but OD inside the
value of x77de0000 [0] but OD inside the 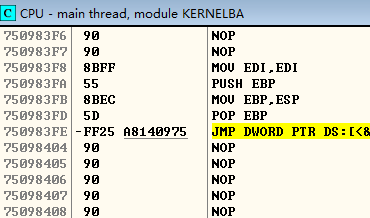 all is 0 x75 beginning?
all is 0 x75 beginning? And if want to find the function name is AddAtomW, according to the offset of optional header found the RVA of the EXPORT Directory value namely IMAGE_EXPORT_DIRECTORY structure address members find AddressOfNames, according to the AddAtomW inside the name array index to find ordinalarray array value, according to the ordinal value as the index function of the relative virtual address address for x000430ed [0], again in OD AddAtomW find function according to the name of the virtual address
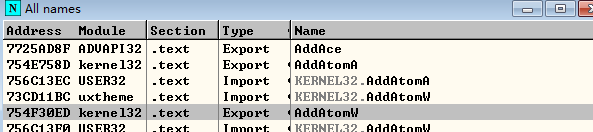
Then according to the words in this way, the correct image=0 x754f30ed x754b0000 x000430ed=0 and 0 0 x77de0000, is this why? Please comment, orz
CodePudding user response:
Is not the same as the actual load address, is said to be the high version of Windows viruses, trojans and other malicious software; You can try your program, each loaded base may be different,